Free Members Quiz
Quiz Summary
0 of 100 Questions completed
Questions:
Information
You have already completed the quiz before. Hence you can not start it again.
Quiz is loading…
You must sign in or sign up to start the quiz.
You must first complete the following:
Results
Results
0 of 100 Questions answered correctly
Your time:
Time has elapsed
You have reached 0 of 0 point(s), (0)
Earned Point(s): 0 of 0, (0)
0 Essay(s) Pending (Possible Point(s): 0)
| Average score |
|
| Your score |
|
Categories
- Not categorized 0%
-
You have Failed in the Quiz, Please get 100% Pass the Quiz.
-
You have Passed in the Quiz.
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
- 59
- 60
- 61
- 62
- 63
- 64
- 65
- 66
- 67
- 68
- 69
- 70
- 71
- 72
- 73
- 74
- 75
- 76
- 77
- 78
- 79
- 80
- 81
- 82
- 83
- 84
- 85
- 86
- 87
- 88
- 89
- 90
- 91
- 92
- 93
- 94
- 95
- 96
- 97
- 98
- 99
- 100
- Current
- Review
- Answered
- Correct
- Incorrect
-
Question 1 of 100
1. Question
1 point(s)To strengthen security measures, a company decides to implement an additional verification step for employees accessing company resources. This step requires not only a password but also a verification code that employees receive on their smartphones. The objective is to protect against unauthorized access, especially in instances where a password may be compromised.
Which of the following best describes the security measure being implemented?
CorrectIncorrect -
Question 2 of 100
2. Question
1 point(s)To enhance network security, a company mandates that all devices attempting to connect to the LAN network must first meet specific security policies; otherwise, access is denied. This strategy aims to minimize the risk of security breaches by ensuring that only compliant devices can access network resources.
What action should the company take to effectively enforce this policy?
CorrectIncorrect -
Question 3 of 100
3. Question
1 point(s)A hospital LAN network needs to enforce strict security measures. The network must automatically evaluate and enforce compliance with security policies for any device attempting to connect, including up-to-date antivirus software, necessary patches, and configurations that comply with healthcare regulatory standards. The goal is to permit only authorized and compliant devices access while restricting or remedying those that are not.
Which network security solution is best suited to meet this challenge?
CorrectIncorrect -
Question 4 of 100
4. Question
1 point(s)In a company’s LAN network, it is required that all devices, including switches, support authentication protocols that can integrate with a RADIUS server for centralized authentication, authorization, and accounting. Given the importance of these protocols, such as IEEE 802.1X, for network security, it becomes crucial to determine which types of switches can be appropriately configured to work with a RADIUS server.
Which of the following statements best reflects the capability required of switches in a LAN network to be controlled by a RADIUS server?
CorrectIncorrect -
Question 5 of 100
5. Question
1 point(s)what is the primary function of Extensible Authentication Protocol (EAP) in the network access control process?
CorrectIncorrect -
Question 6 of 100
6. Question
1 point(s)A web application employs extensive input validation and output encoding mechanisms to protect against XSS attacks. Despite these defenses, the application’s developers decide to integrate Content Security Policy (CSP) as an additional layer of protection. They configure CSP to prevent inline scripts from running and to limit script sources to only trusted domains.
Which of the following CSP directives best exemplifies this security enhancement?
CorrectIncorrect -
Question 7 of 100
7. Question
1 point(s)You are tasked with reviewing the security of a web application that allows users to submit feedback. The application stores user feedback in a database and displays it on a public page. During your review, you discover that the application does not properly sanitize user input before storing it in the database and rendering it on the public page.
Which of the following types of XSS attacks would an attacker most likely attempt to exploit this vulnerability?
CorrectIncorrect -
Question 8 of 100
8. Question
1 point(s)Which of the following is the most effective method to prevent Reflected XSS attacks in a web application that dynamically generates HTML pages based on user input?
CorrectIncorrect -
Question 9 of 100
9. Question
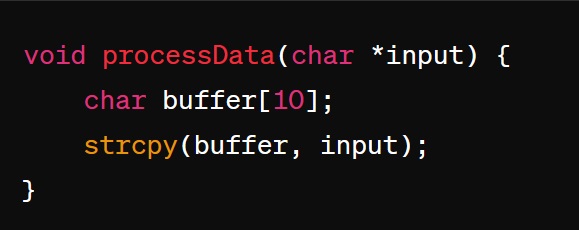
1 point(s)In the development of a C++ application, a programmer writes a function to handle user input. Given the following pseudocode:
Assuming the user can control the content and the length of input, which of the following attacks is the function most vulnerable to, and what is the most likely outcome if it is exploited?
CorrectIncorrect -
Question 10 of 100
10. Question
1 point(s)A critical network application is experiencing intermittent crashes. You’ve been tasked with investigating the issue. Early analysis suggests a potential buffer overflow vulnerability, but the code responsible is complex.
Which primary debugging technique would be the MOST effective at pinpointing the exact location and nature of the overflow?
CorrectIncorrect -
Question 11 of 100
11. Question
1 point(s)A web server is running on a Linux system and is vulnerable to a stack-based buffer overflow attack. During a penetration testing engagement, you discover that the server is using an insecure copy() function to copy user-supplied data into a fixed-size buffer on the stack. The buffer size is 256 bytes.
You craft a malicious input string that consists of:
- A NOP sled of 200 bytes
- Shellcode of 60 bytes
- The malicious return address that points to the beginning of the NOP sled
Which of the following return addresses should you use to successfully exploit the buffer overflow vulnerability and gain remote code execution on the server?
CorrectIncorrect -
Question 12 of 100
12. Question
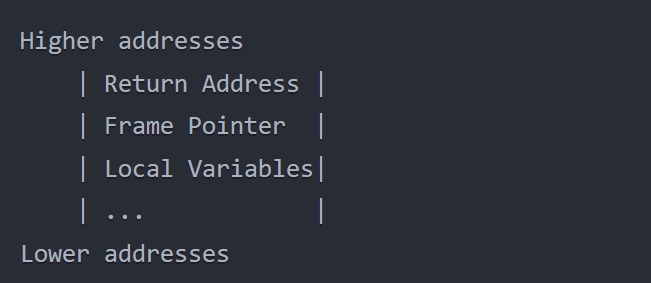
1 point(s)A web server is running on a 32-bit Linux system and is vulnerable to a stack-based buffer overflow attack. The server is using an insecure
copy()function to copy user-supplied data into a fixed-size buffer of 256 bytes (including the null terminator) on the stack. The server is compiled with gcc 4.8.5 without any security mitigations like Stack Canaries or Address Space Layout Randomization (ASLR).The memory layout of the stack follows the typical structure for a 32-bit x86 architecture:
During a penetration testing engagement, you discover the vulnerability and craft a malicious input string consisting of:
- A NOP sled of 200 bytes
- Shellcode of 60 bytes
- The malicious return address that should overwrite the original return address on the stack
Assuming that the buffer is located at the memory address
0xBFFFF8A0, which of the following return addresses should you use to successfully exploit the buffer overflow vulnerability and gain remote code execution on the server?CorrectIncorrect -
Question 13 of 100
13. Question
1 point(s)Given a web application that implements CSRF tokens to protect against CSRF attacks, an application developer notices inconsistent behavior with CSRF protection across different parts of the application. Upon review, it is discovered that some state-changing requests do not utilize the CSRF token validation as expected.
Which of the following factors is most likely causing the inconsistent CSRF protection?
CorrectIncorrect -
Question 14 of 100
14. Question
1 point(s)In an enterprise-level web application, CSRF protection is implemented through a double submit cookie technique. A security analyst is tasked with enhancing the security of this system. The analyst suggests that in addition to the double submit cookie technique, a server-side token validation should be implemented for certain critical functions of the application.
Which of the following reasons best explains the advantage of adding server-side token validation to the double submit cookie technique?
CorrectIncorrect -
Question 15 of 100
15. Question
1 point(s)An organization uses a web framework that automatically embeds a CSRF token in every form and validates it on every POST request. However, the security team identifies that AJAX requests within the application are not consistently protected against CSRF attacks. To address this, the team considers several strategies.
Which of the following is the most effective strategy to ensure CSRF protection is uniformly applied to AJAX requests?
CorrectIncorrect -
Question 16 of 100
16. Question
1 point(s)A highly sensitive web application processes critical financial transactions. The developers have implemented standard CSRF protection using anti-CSRF tokens. However, a recent security audit revealed potential issues.
Which of the following scenarios could STILL pose a CSRF risk despite the existing protection?
CorrectIncorrect -
Question 17 of 100
17. Question
1 point(s)An organization has deployed an Intrusion Prevention System (IPS) to protect its critical network resources. The IPS is configured to inspect traffic in inline mode and take appropriate actions based on predefined rules. In this scenario, which of the following actions would the IPS NOT be capable of performing?
CorrectIncorrect -
Question 18 of 100
18. Question
1 point(s)You’re implementing a new network-based IPS for a critical segment of your enterprise network. To maximize the effectiveness of the IPS, which of the following network design considerations is MOST important?
CorrectIncorrect -
Question 19 of 100
19. Question
1 point(s)An enterprise network deploys both network-based IPS (NIPS) and host-based IDS (HIDS) solutions to enhance its security posture against sophisticated attacks. Considering the strategic placement and inherent capabilities of these systems, which of the following would most effectively utilize the strengths of a NIPS rather than a HIDS?
CorrectIncorrect -
Question 20 of 100
20. Question
1 point(s)An administrator needs to configure the IPS to reduce the incidence of false positives without significantly impacting the detection of new, unknown threats. Which of the following adjustments would BEST achieve this balance?
CorrectIncorrect -
Question 21 of 100
21. Question
1 point(s)A legacy encryption system uses a polyalphabetic substitution cipher where the key is a 10-character word. During operation, the key is repeated to match the length of the plaintext. Which of the following attack strategies would be MOST effective at recovering the plaintext?
CorrectIncorrect -
Question 22 of 100
22. Question
1 point(s)In symmetric block ciphers, the mode of operation plays a crucial role in defining the cipher’s security and applicability. One particular mode ensures both confidentiality and integrity of the data, making it exceptionally suitable for environments demanding high security, such as military and defense applications. Which of the following modes of operation provides this level of security?
CorrectIncorrect -
Question 23 of 100
23. Question
1 point(s)Using the same encryption key for an extended period in symmetric cryptography can significantly increase the risk of key compromise and cryptographic attacks, such as brute force or cryptanalysis, especially in sectors with stringent security requirements like government and military operations.
CorrectIncorrect -
Question 24 of 100
24. Question
1 point(s)In symmetric cryptography, the security of encrypted communication is independent of the key management practices, since the strength of the encryption algorithm alone determines the overall security of the system.
CorrectIncorrect -
Question 25 of 100
25. Question
1 point(s)Understanding the modes of operation is crucial for secure encryption and decryption processes. These modes determine how block ciphers process plaintext and ciphertext, affecting both security and performance. Considering the case where data integrity, confidentiality, and real-time processing are crucial, select all the modes of operation that are most suitable for encrypting streaming multimedia content over a network [Select all that apply].
CorrectIncorrect -
Question 26 of 100
26. Question
1 point(s)The Advanced Encryption Standard (AES) is widely recognized for its robustness and versatility in securing sensitive data. A key feature of AES is its flexibility in key length, offering variations of 128, 192, and 256 bits to accommodate different levels of security requirements. Given the critical importance of choosing the appropriate key size to balance security needs and computational efficiency, consider the following statement:
“The AES algorithm’s security is solely determined by its key length, with longer keys always providing proportionally increased security against all forms of cryptographic attacks, without considering other factors such as the mode of operation, implementation practices, or potential vulnerabilities in the cryptographic protocol itself.”
CorrectIncorrect -
Question 27 of 100
27. Question
1 point(s)Consider a substitution cipher system where the security relies significantly on the secrecy of the substitution algorithm rather than just the key. This approach contradicts which of the following principles?
CorrectIncorrect -
Question 28 of 100
28. Question
1 point(s)Consider a substitution cipher with a 29-character alphabet. During an attack, it’s discovered that certain ciphertext character combinations appear significantly more often than others in intercepted messages. Which cryptanalysis technique is MOST likely to succeed in breaking this cipher?
CorrectIncorrect -
Question 29 of 100
29. Question
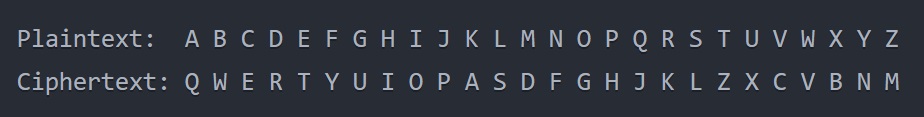
1 point(s)Alice wants to send a confidential message to Bob using a substitution cipher. The plaintext message is “MEETMEATPARK“. Alice and Bob have agreed to use a monoalphabetic substitution cipher with the following encryption key:
If Alice encrypts the plaintext message “MEETMEATPARK” using the given key, what is the ciphertext?
CorrectIncorrect -
Question 30 of 100
30. Question
1 point(s)When analyzing a cipher text produced by a monoalphabetic substitution cipher, a cryptanalyst notices a disproportionately high occurrence of certain letters compared to others. What is the most likely technique this cryptanalyst would use to exploit this characteristic in decrypting the cipher text?
CorrectIncorrect -
Question 31 of 100
31. Question
1 point(s)An organization assesses the risk associated with a critical data asset. The data asset has been valued at $500,000 (Asset Value, AV). A vulnerability assessment identifies a potential threat that could exploit a weakness in the system, with an Exposure Factor (EF) of 20%. The Annual Rate of Occurrence (ARO) of this threat is estimated to be once every five years. The organization is considering implementing a control to mitigate this risk.
Given the information above, calculate the Annual Loss Expectancy (ALE) before and after implementing a control that is expected to reduce the threat frequency by half. Additionally, if the cost of implementing the control is $20,000 per year, determine whether the Cost-Benefit Analysis (CBA) justifies the control implementation.
CorrectIncorrect -
Question 32 of 100
32. Question
1 point(s)An organization operates a web application that handles sensitive customer data. The IT department has identified several risks related to data breaches and is considering implementing additional security measures. Given the following data, select the option that best describes the most cost-effective security measure the organization should consider, based on the potential impact and cost of implementation:
- SQL Injection vulnerability, with an estimated Exposure Factor (EF) of 30% and an Annual Rate of Occurrence (ARO) of 0.8. The cost to implement a Web Application Firewall (WAF) is $15,000 annually.
- Phishing attacks, with an EF of 50% and an ARO of 1.2. Employee security awareness training costs $10,000 annually.
- Insider threat due to weak access controls, with an EF of 70% and an ARO of 0.5. Implementing stronger access control measures costs $20,000 annually.
Asset Value (AV) for the web application’s data is estimated at $500,000.
Calculate the Annual Loss Expectancy (ALE) reduction for each risk after implementing the respective control and determine the most cost-effective security measure.CorrectIncorrect -
Question 33 of 100
33. Question
1 point(s)An organization’s newly developed application has been identified with vulnerabilities that could potentially allow unauthorized access to sensitive customer data. Considering the risk impacts, which of the following actions should the organization prioritize to mitigate the identified risk effectively?
CorrectIncorrect -
Question 34 of 100
34. Question
1 point(s)You are investigating a potential breach within an enterprise network. You’ve identified irregular outbound traffic patterns from several workstations in the accounting department. The traffic is consistent with file exfiltration, but the source process is obfuscated in the initial log analysis.
Which of the following actions would be the MOST effective next step in your investigation?
CorrectIncorrect -
Question 35 of 100
35. Question
1 point(s)An incident response team has detected suspicious activity on a critical server during the night shift. The team has collected various artifacts, including network traffic captures, process listings, and disk images. To effectively hunt for threats and identify potential indicators of compromise (IOCs), which technique should the team prioritize using?
CorrectIncorrect -
Question 36 of 100
36. Question
1 point(s)You observe lateral movements within the network that are suspected to be carried out by a sophisticated actor using encrypted channels. To efficiently detect and analyze these movements, which of the following approaches should be prioritized for immediate implementation, considering the need for decoding encrypted traffic and identifying stealthy command and control communications?
CorrectIncorrect -
Question 37 of 100
37. Question
1 point(s)A suspicious scheduled task running on a critical production server. The task executes a PowerShell script with encoded content. You want to understand the script’s behavior but are concerned about triggering any potentially harmful actions. Which of the following is the BEST course of action?
CorrectIncorrect -
Question 38 of 100
38. Question
1 point(s)A security analyst discovers a suspicious executable file on a compromised host. To gather more insights into the potential malware’s capabilities and behavior, which dynamic analysis technique should the analyst prioritize?
CorrectIncorrect -
Question 39 of 100
39. Question
1 point(s)A university employs Identity and Access Management (IAM) to control access to online course materials and the Zero Trust security model to enhance the protection of its digital resources. Under this model, even students who are authenticated and authorized to access certain online materials must undergo additional verification steps when accessing these resources from new devices or locations.
Which of the following strategies best addresses this concern?
CorrectIncorrect -
Question 40 of 100
40. Question
1 point(s)A financial analyst requires access to specific financial reports. The system must be designed in a way to grants access only to the reports requested by the analyst, thereby preventing access to other sensitive financial information.
Which of the following access control models best fits this requirement?
CorrectIncorrect -
Question 41 of 100
41. Question
1 point(s)What is the most effective type of data to extract from an adversary’s infrastructure to ensure a prolonged impact on their operations, according to the Pyramid of Pain?
CorrectIncorrect -
Question 42 of 100
42. Question
1 point(s)Which of the following best describes the concept of the Pyramid of Pain?
CorrectIncorrect -
Question 43 of 100
43. Question
1 point(s)Your organization’s risk management framework has traditionally focused on technical and operational risks. Senior management now wants to incorporate strategic and overall risk assessment program. Which of the following would be the MOST important factor to consider when expanding your risk assessment approach?
CorrectIncorrect -
Question 44 of 100
44. Question
1 point(s)Which of the following best describes the concept of Risk Appetite?
CorrectIncorrect -
Question 45 of 100
45. Question
1 point(s)In a multinational corporation, the Chief Information Security Officer (CISO) is developing a strategy that aligns with global data protection regulations. The organization operates in multiple jurisdictions with differing compliance requirements. What should be the primary focus of this strategy to ensure compliance across all regions?
CorrectIncorrect -
Question 46 of 100
46. Question
1 point(s)Your organization is expanding internationally and needs to integrate compliance with multiple new regulatory frameworks. You’ve been tasked with aligning the company’s security program with these requirements. Which of the following activities would be the MOST effective first step?
CorrectIncorrect -
Question 47 of 100
47. Question
1 point(s)Your company’s competitor has a similar infrastructure to yours, has recently suffered a significant data breach. The attack was carried out by exploiting a zero-day vulnerability in a widely-used Content Management System (CMS).
Which of the following would be the most effective proactive measure to prevent a similar breach in your organization?
CorrectIncorrect -
Question 48 of 100
48. Question
1 point(s)Rumors are spreading about a zero-day vulnerability in a critical software component used extensively within your organization. No patch is yet available from the vendor. Which of the following actions offers the BEST initial risk mitigation?
CorrectIncorrect -
Question 49 of 100
49. Question
1 point(s)When your Threat Intelligence tools highlight repeated attempts to exfiltrate data to an unknown external IP in an unusual geographic region, which of the following actions should be prioritized to effectively manage the threat?
CorrectIncorrect -
Question 50 of 100
50. Question
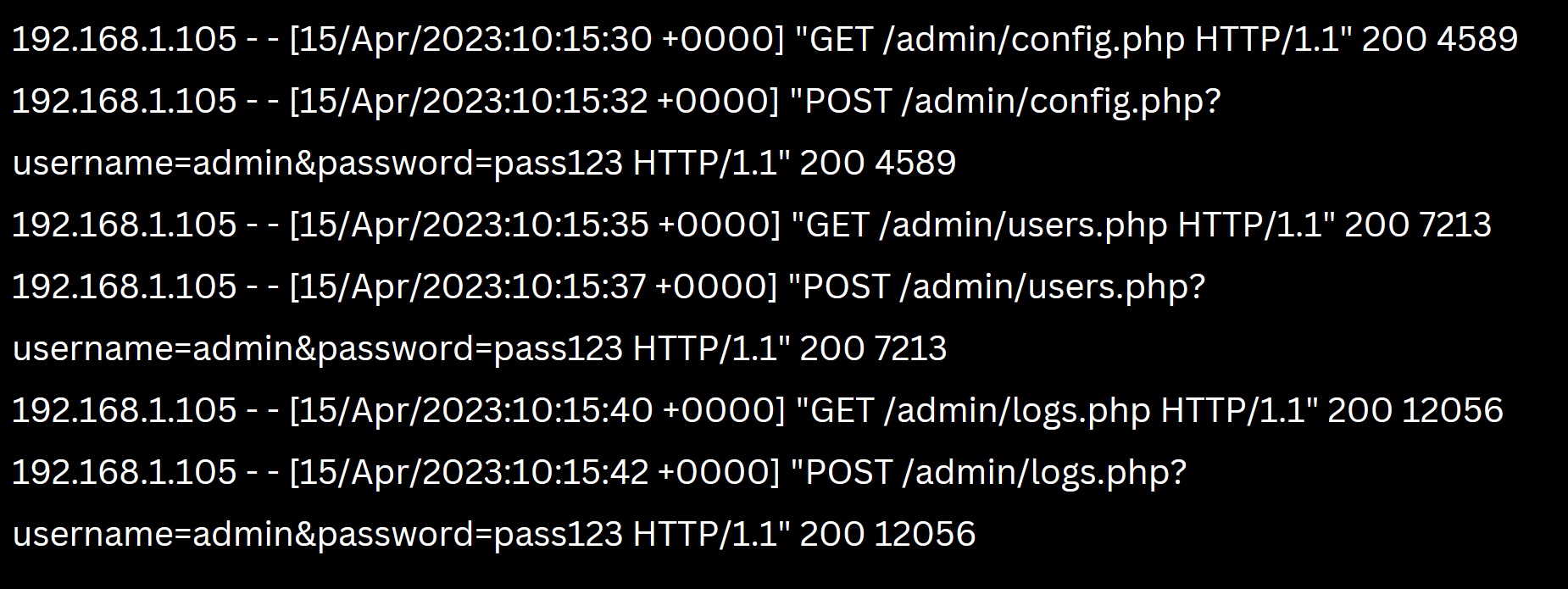
1 point(s)You are analyzing server access logs from your organization’s website during a period when a breach is suspected. Below is a snippet of the logs:
!
Based on the provided log snippet, which of the following attack vectors is most likely being employed?
CorrectIncorrect -
Question 51 of 100
51. Question
1 point(s)An organization transitioning to a more collaborative threat intelligence sharing model. To streamline intelligence exchange, you recommend adopting STIX. Which of the following is the most significant benefit STIX provides in this situation?
CorrectIncorrect -
Question 52 of 100
52. Question
1 point(s)In assessing the alignment of a Threat Intelligence platform with the MITRE ATT&CK framework, which of the following metrics would most effectively indicate the platform’s effectiveness?
CorrectIncorrect -
Question 53 of 100
53. Question
1 point(s)Which of the following techniques is most effective in mitigating runtime attacks caused by buffer overflow vulnerabilities in a web application?
CorrectIncorrect -
Question 54 of 100
54. Question
1 point(s)You are responding to a suspected intrusion on a critical server. Initial analysis shows a potentially malicious process running with elevated privileges, communicating over an unusual network port. Which of the following actions would be the MOST effective as your next step?
CorrectIncorrect -
Question 55 of 100
55. Question
1 point(s)A cybersecurity engineer is tasked with identifying and mitigating an advanced attack where the threat actor injects malicious code into a running application. Which of the following techniques would be most effective in detecting and preventing such an attack?
CorrectIncorrect -
Question 56 of 100
56. Question
1 point(s)An organization recently discovered that their systems were compromised by a highly sophisticated malware variant. Upon analysis, the security team found that the malware employed a combination of anti-debugging, anti-virtualization, and anti-sandboxing techniques to evade detection and analysis. The malware also utilized a complex command and control (C2) infrastructure with multiple layers of encryption and obfuscation.
Which type of malware is most likely responsible for this attack?
CorrectIncorrect -
Question 57 of 100
57. Question
1 point(s)You are investigating a recent incident on a sensitive corporate network segment where several critical assets appear to be compromised. Upon initial analysis, there’s no evidence of typical malware signatures or suspicious network traffic. However, you notice that specific system resource utilization seems abnormally high.
Which of the following could be the most likely cause of this situation?
CorrectIncorrect -
Question 58 of 100
58. Question
1 point(s)In ransomware attack campaigns, which of the following is the most likely initial vector used by attackers to gain access to an organization’s network, emphasizing the manipulation of human behavior rather than exploiting software vulnerabilities?
CorrectIncorrect -
Question 59 of 100
59. Question
1 point(s)A penetration tester discovers a critical zero-day vulnerability in a widely used open-source library, allowing arbitrary code execution. What should be their next step?
CorrectIncorrect -
Question 60 of 100
60. Question
1 point(s)Which of the following techniques would a sophisticated malware use to evade detection by an antivirus program, relying on the modification of its code structure without altering its functional behavior?
CorrectIncorrect -
Question 61 of 100
61. Question
1 point(s)You are the lead cybersecurity engineer for a multinational corporation, and your team has identified a possible intrusion using threat intelligence feeds focusing on Tactics, Techniques, and Procedures (TTPs) known to be used by a sophisticated APT group. However, there’s no clear evidence on your traditional detection solutions.
Which of the following actions should you take FIRST?
CorrectIncorrect -
Question 62 of 100
62. Question
1 point(s)According to the Pyramid of Pain, which of the following indicators would be the most difficult for an adversary to change and re-acquire, causing them the greatest amount of pain?
CorrectIncorrect -
Question 63 of 100
63. Question
1 point(s)Your network security team has recently experienced a significant increase in security alerts related to suspected malware. Many of these are identified by traditional, signature-based solutions. Which of the following activities would be MOST effective in improving detection capabilities while also reducing false positives?
CorrectIncorrect -
Question 64 of 100
64. Question
1 point(s)An organization has been targeted by a sophisticated adversary group. The security team has identified some of the adversary’s tactics, techniques, and procedures (TTPs) and wants to prioritize their defense efforts. Which of the following actions would be the most effective defense strategy against this threat actor?
CorrectIncorrect -
Question 65 of 100
65. Question
1 point(s)A cybersecurity analyst detects an unusual sequence of outbound network traffic patterns from a company’s internal file server. This traffic is directed towards a known Command and Control (C2) server. Which of the following best serves as the primary Indicator of Compromise (IOC) in this scenario?
CorrectIncorrect -
Question 66 of 100
66. Question
1 point(s)A security analyst is investigating potential security breaches and notices repeated connections to suspicious IP addresses listed in recently updated threat intelligence feeds. Which of the following would be the most specific Indicator of Compromise (IOC) to focus further forensic analysis on?
CorrectIncorrect -
Question 67 of 100
67. Question
1 point(s)Which of the following is the most effective way to identify and track the lateral movement of an attacker within a compromised network using Indicators of Compromise (IOCs)?
CorrectIncorrect -
Question 68 of 100
68. Question
1 point(s)A company has structured its network into smaller, secure zones to enhance security. Employees are granted access only to the resources within their designated zone that are necessary for their job roles. This segmentation ensures that if an attacker compromises an employee’s credentials, the breach’s impact is confined to that particular zone, significantly reducing the risk of widespread access to the network.
Which of the following network security solutions best fits this requirement?
CorrectIncorrect -
Question 69 of 100
69. Question
1 point(s)Your organization has relied on traditional anti-malware to defend against ransomware. However, recent threat intelligence reports indicate that sophisticated ransomware groups are now routinely exfiltrating data before encrypting systems.
Which of the following security controls should be prioritized to address this threat?
CorrectIncorrect -
Question 70 of 100
70. Question
1 point(s)A zero-day vulnerability has been discovered in a critical business application widely used within your organization. There’s no vendor patch available, and intelligence reports confirm active exploitation of the vulnerability.
Which of the following actions is the MOST appropriate initial response?
CorrectIncorrect -
Question 71 of 100
71. Question
1 point(s)A company’s database stores sensitive customer information, including personally identifiable information (PII) and financial data. The database is accessible through a web application, which has been identified as vulnerable to SQL injection attacks.
Which of the following security controls would be the MOST effective in protecting against SQL injection attacks in this scenario?
CorrectIncorrect -
Question 72 of 100
72. Question
1 point(s)You are a security engineer for a financial institution. During a routine audit, you discover a legacy application that processes sensitive customer data and transmits it over the network without encryption. Which of the following represents the most immediate threat?
CorrectIncorrect -
Question 73 of 100
73. Question
1 point(s)A company’s server is running outdated software and has been configured without a firewall while being directly exposed to the internet. How would you classify the level of vulnerability of this system?
CorrectIncorrect -
Question 74 of 100
74. Question
1 point(s)The IT team has delayed implementing critical software updates for its network systems despite repeated warnings about known vulnerabilities. What is the most likely impact of this decision on the company’s network security?
CorrectIncorrect -
Question 75 of 100
75. Question
1 point(s)A cybersecurity team has just encountered a never-before-seen malware infecting their systems, suspected to be leveraging a zero-day vulnerability. During the initial triage, which action should be prioritized to best contain and analyze the threat?
CorrectIncorrect -
Question 76 of 100
76. Question
1 point(s)During a forensic investigation of a compromised system, an analyst notices an unusual spike in CPU usage and the presence of encrypted files with the extension “.locky”. Further analysis reveals that the encrypted files are critical system files and documents. Which of the following is the most likely type of malware responsible for this attack?
CorrectIncorrect -
Question 77 of 100
77. Question
1 point(s)While performing static analysis on a malware sample, a security analyst observes the following characteristics in the disassembled code:
- Heavy usage of obfuscation techniques
- Presence of strings like “kernel32.dll”, “LoadLibrary”, and “GetProcAddress”
- References to specific Windows API functions
- Embedded shellcode within the binary
Based on these findings, which of the following is the MOST LIKELY origin and type of the malware?
CorrectIncorrect -
Question 78 of 100
78. Question
1 point(s)In analyzing network traffic logs to identify potential malware infections, what behavioral indicator is most indicative of an Advanced Persistent Threat (APT) attempting lateral movement within a network?
CorrectIncorrect -
Question 79 of 100
79. Question
1 point(s)During a red team engagement, you successfully phish the CEO’s credentials using a crafted spear-phishing campaign. Upon accessing the CEO’s email account, you discover that the CEO has authorized large wire transfers to untrusted accounts in the past via email.
Which of the following factors likely contributed most to the success of the unauthorized wire transfers?
CorrectIncorrect -
Question 80 of 100
80. Question
1 point(s)You are the lead cybersecurity engineer for a mid-sized company. Sudden reports emerge of several critical company servers showing files with a “.encrypted” extension. Initial investigations indicate a privileged account belonging to a recently terminated IT administrator was used in the attack.
Which of the following should be your IMMEDIATE priority?
CorrectIncorrect -
Question 81 of 100
81. Question
1 point(s)Following a breach on an e-commerce site where attackers exfiltrated credit card information, which response action is most critical to mitigate further damage and ensure regulatory compliance?
CorrectIncorrect -
Question 82 of 100
82. Question
1 point(s)During a red team engagement, you are tasked with gaining initial access to a multinational company’s secure environment. After performing OSINT, you discover that the company uses a specific helpdesk ticketing system. You decide to launch a phishing campaign impersonating the helpdesk system.
Which of the following tactics would be most effective in increasing the success rate of your phishing campaign?
CorrectIncorrect -
Question 83 of 100
83. Question
1 point(s)In penetration testing, you are tasked with bypassing a newly implemented Intrusion Detection System (IDS) that is reputed for its advanced detection algorithms and threat pattern recognition. Which of the following techniques would be most effective in evading detection while carrying out your activities?
CorrectIncorrect -
Question 84 of 100
84. Question
1 point(s)During a red team operation, you are tasked with assessing the security of a web application that uses OAuth for authentication. After initial reconnaissance, you discover an endpoint that seems vulnerable to an OAuth redirection attack.
Which of the following strategies would most effectively exploit this vulnerability to perform unauthorized actions on behalf of the logged-in users?
CorrectIncorrect -
Question 85 of 100
85. Question
1 point(s)You are reviewing a threat intelligence report that includes STIX data detailing a specific malware attack. The data is structured as follows:
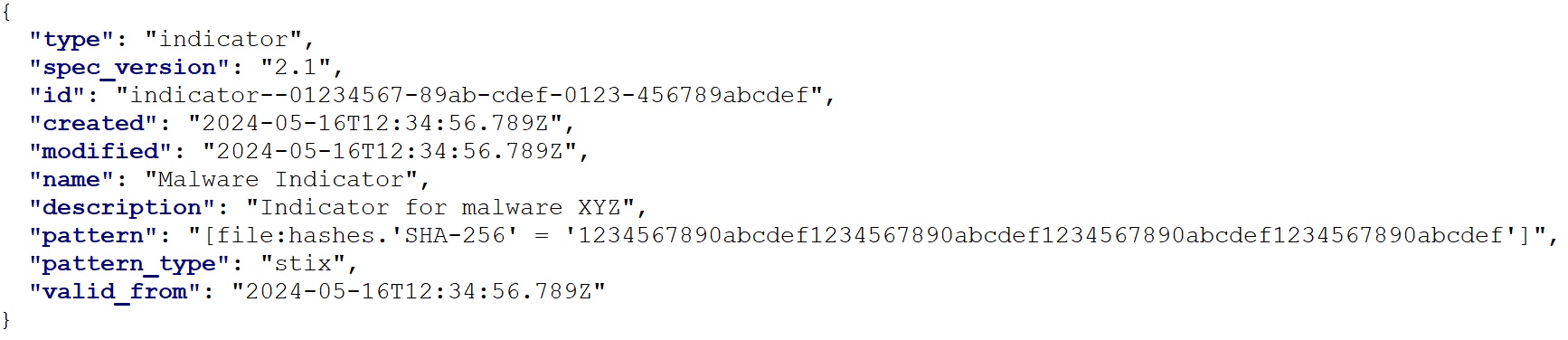
What format is this STIX data presented in?
CorrectIncorrect -
Question 86 of 100
86. Question
1 point(s)How does STIX improve incident response automation within a security operations center (SOC)?
CorrectIncorrect -
Question 87 of 100
87. Question
1 point(s)Your organization is participating in a threat intelligence sharing community. You need to ensure that the data format enables efficient exchange of information about threat actors, their tactics, techniques, and procedures (TTPs). Which of the following is the most suitable option?
CorrectIncorrect -
Question 88 of 100
88. Question
1 point(s)In a large-scale cyber threat intelligence sharing initiative involving multiple organizations across different sectors, which of the following challenges is MOST likely to be mitigated by adopting STIX as the primary information sharing format?
CorrectIncorrect -
Question 89 of 100
89. Question
1 point(s)How can integrating STIX with a SIEM system enhance automated threat detection and response capabilities?
CorrectIncorrect -
Question 90 of 100
90. Question
1 point(s)As a cybersecurity analyst, you are investigating a sophisticated cyber attack on your organization. To effectively analyze the threat data, map it to the MITRE ATT&CK framework, and share your findings with the incident response team, which of the following STIX objects would be most crucial to leverage?
CorrectIncorrect -
Question 91 of 100
91. Question
1 point(s)A cybersecurity engineer aims to streamline threat intelligence sharing between their organization and external partners. Which combination of STIX components would be MOST effective in achieving this goal while ensuring machine readability, standardization, and efficient collaboration?
CorrectIncorrect -
Question 92 of 100
92. Question
1 point(s)A nation-state actor has compromised a key software vendor, potentially affecting multiple critical infrastructure sectors. Which of the following TTPs is most likely employed in such a supply chain attack, and what is the best practice for identifying and mitigating this threat?
CorrectIncorrect -
Question 93 of 100
93. Question
1 point(s)During an investigation of a breach with limited Indicators of Compromise (IoCs), you rely on Tactics, Techniques, and Procedures (TTPs) for threat attribution. What is a significant challenge you might face in using TTPs for this purpose?
CorrectIncorrect -
Question 94 of 100
94. Question
1 point(s)Your organization suspects a persistent threat actor is using advanced evasion techniques to bypass security measures. Which of the following methods is most effective in identifying and mitigating these techniques?
CorrectIncorrect -
Question 95 of 100
95. Question
1 point(s)A healthcare provider is developing a continuity plan to ensure minimal disruption in patient care during a ransomware attack. Which of the following is the MOST critical step in the planning process?
CorrectIncorrect -
Question 96 of 100
96. Question
1 point(s)A financial institution is implementing AI-driven anomaly detection for real-time threat detection. Which of the following is the MOST critical factor to ensure the system’s long-term effectiveness and adaptability to evolving threats?
CorrectIncorrect -
Question 97 of 100
97. Question
1 point(s)An organization is evaluating its multi-layered defense strategy to ensure business continuity during cyber incidents. Which of the following is the most critical component to ensure effective integration and coordination of multiple security layers?
CorrectIncorrect -
Question 98 of 100
98. Question
1 point(s)In a targeted phishing attack against a healthcare organization, which of the following is the MOST reliable indicator for identifying Patient Zero?
CorrectIncorrect -
Question 99 of 100
99. Question
1 point(s)In the event of a ransomware outbreak, what is the most effective method to identify the Patient Zero and trace the origin of the malware?
CorrectIncorrect -
Question 100 of 100
100. Question
1 point(s)During a complex cyberattack investigation on a large corporate network with multiple compromised systems, which of the following is the most effective approach to rapidly identify Patient Zero?
CorrectIncorrect