In today’s cybersecurity posture, Key Performance Indicators (KPIs) serve as the compass guiding Security Operations Centers (SOCs) toward excellence. KPIs, essentially metrics or indicators, are not just numbers or data points, they are the heartbeat of SOC operations, ensuring that every aspect of incident response and management is not just operational but optimized for efficiency, speed, accuracy, and fidelity.
Cyber threats evolve with daunting speed and complexity, and the ability of a SOC to respond effectively is crucial. KPIs are the lens through which SOCs can evaluate their performance, identify areas for improvement, and ensure that their incident handling processes are both swift and precise. Without these indicators, SOCs may find themselves navigating in the dark, unable to gauge the effectiveness of their operations or justify the investment in cybersecurity to stakeholders.
The absence of well-defined KPIs can lead to a reactive rather than proactive incident response, where threats are only addressed after they have caused significant damage. This not only impacts the organization’s security posture but can also have dire financial and reputational consequences. Moreover, without KPIs, measuring the improvement or decline in SOC operations over time becomes a challenge, making it difficult to adapt to the ever-changing threat landscape.
Let us review the key KPIs related to SOC.
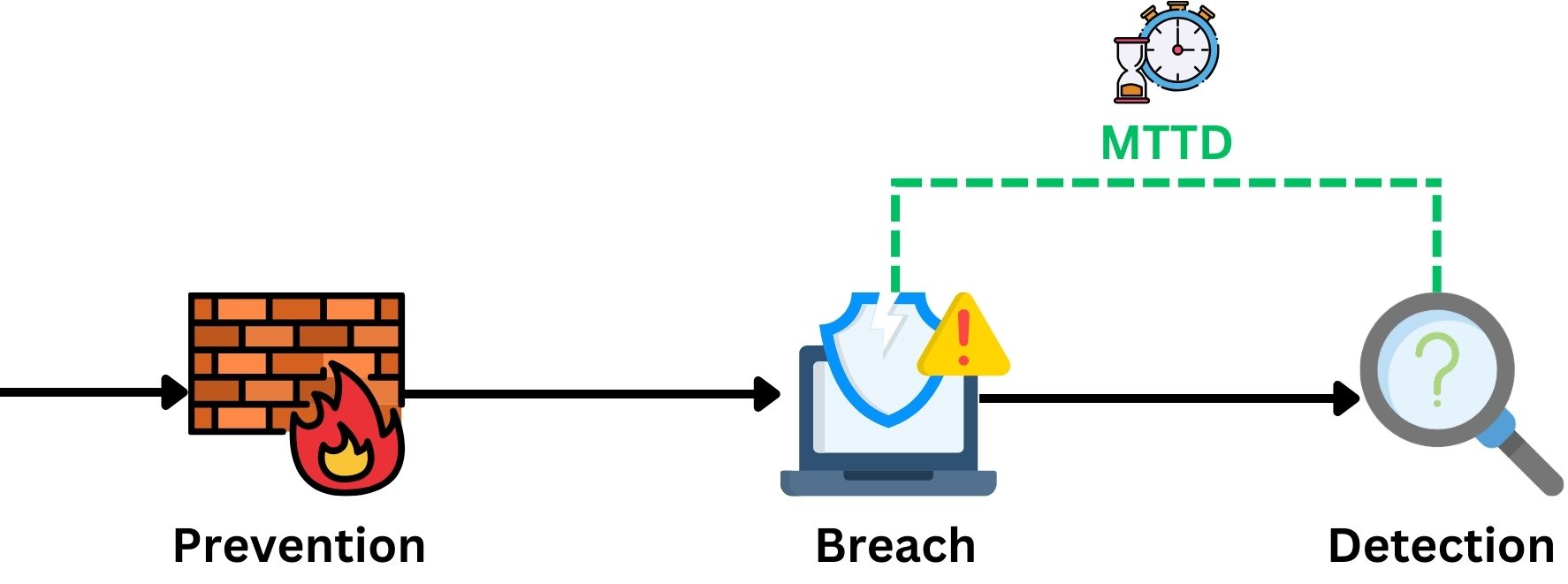
Mean Time to Detect (MTTD)
MTTD is a core SOC and pivotal metric, spotlighting the efficiency and speed of identifying cybersecurity threats and attacks. This indicator measures the time duration between the inception of a security incident and its detection by the SOC team. A lower MTTD signifies a more agile and responsive SOC, capable of swiftly recognizing potential threats. This rapid detection is crucial for minimizing the window of opportunity for attackers. Optimizing MTTD is essential for effective incident response and management in today’s fast-paced cyber landscape.
A common example is using Machine Learning to detect Zero-Day malware or vulnerability exploits.
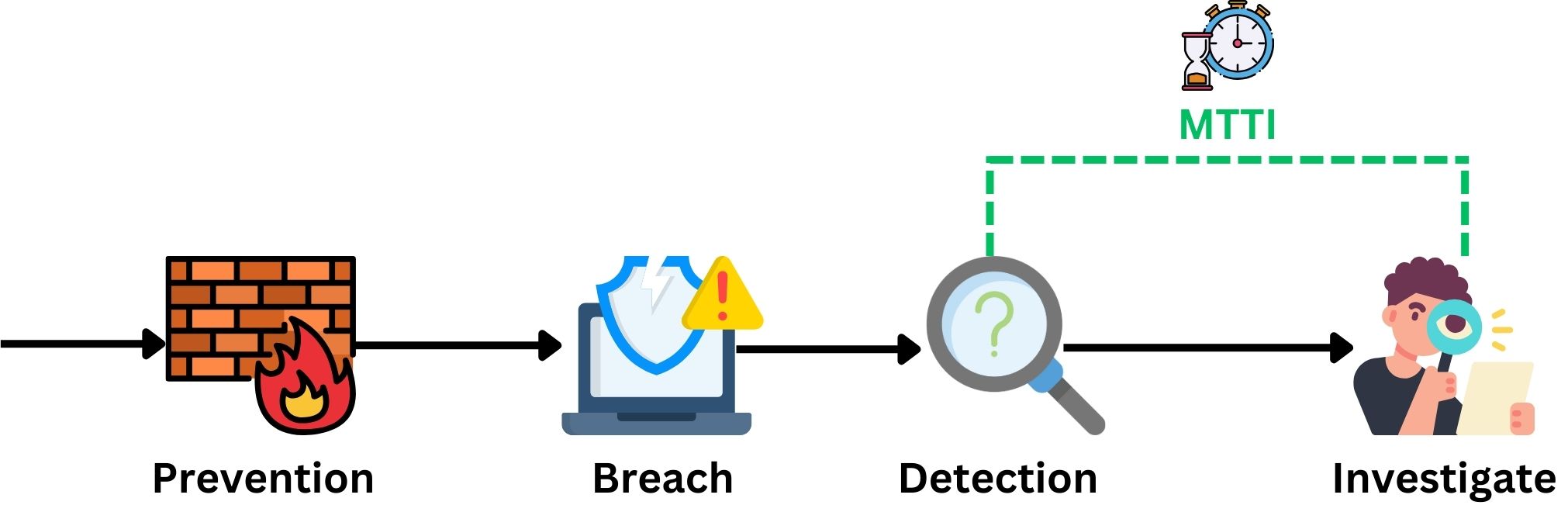
Mean Time to Investigate (MTTI)
Following detection, the Mean Time to Investigate (MTTI) is the next metric for SOCs, emphasizing rapid and accurate analysis and understanding of the nature of the detected cybersecurity incident. This metric gauges the average time taken from the initial detection of a threat to when it is thoroughly investigated. A shorter MTTI reflects a SOC’s capability to quickly dissect and comprehend the complexities of an incident, facilitating a more informed and effective response.
A common example is trained personnel using a centralized threat intelligence warehouse to rapidly query, analyze, and understand the full details of the incident.
Mean Time to Respond (MTTR)
Apparently, MTTR is a post-detection metric. MTTR measures the average time from the identification of a cybersecurity threat to the initiation of a response that mitigates or contains the impact. A lower MTTR indicates a SOC’s proficiency in quickly activating its resources to counteract threats. Optimizing MTTR is essential for effective incident handling, ensuring that SOCs can maintain a robust defense against the evolving landscape of cyber threats.
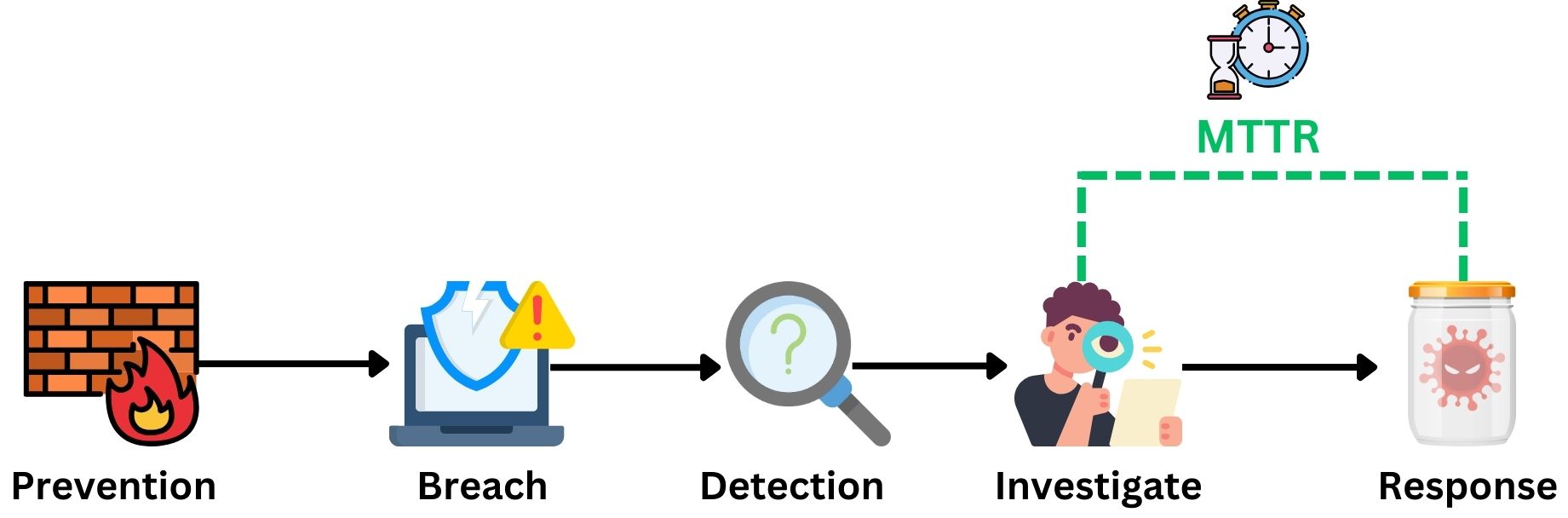
Examples of the most common responses include, but are not limited to:
- Share Indicator of Compromises (IOCs)
- Isolate a Machine
- Lock User Account
- Block IP Addresses
- Patch Vulnerabilities
- Update Security policy
- Lunch Malware Scan
Organizations aiming to optimize MTTR typically rely on a high level of automation and orchestration, developing an ecosystem where tools and processes communicate seamlessly, ensuring swift and coordinated response actions.
Triage and Fidelity
In SOC operations, Triage and Fidelity emerge as key metrics, emphasizing the importance of prioritizing incidents based on their severity and the reliability of the data indicating a potential threat.
Triage is the process of evaluating and prioritizing security alerts based on their severity, impact, and likelihood of being a true positive. This process enables SOC teams to focus their efforts on the most critical issues first, ensuring that resources are allocated effectively.
Fidelity, on the other hand, relates to the accuracy and reliability of security alerts. High-fidelity alerts are those with a high confidence level of being genuine threats, reducing the time and resources spent on investigating false positives.
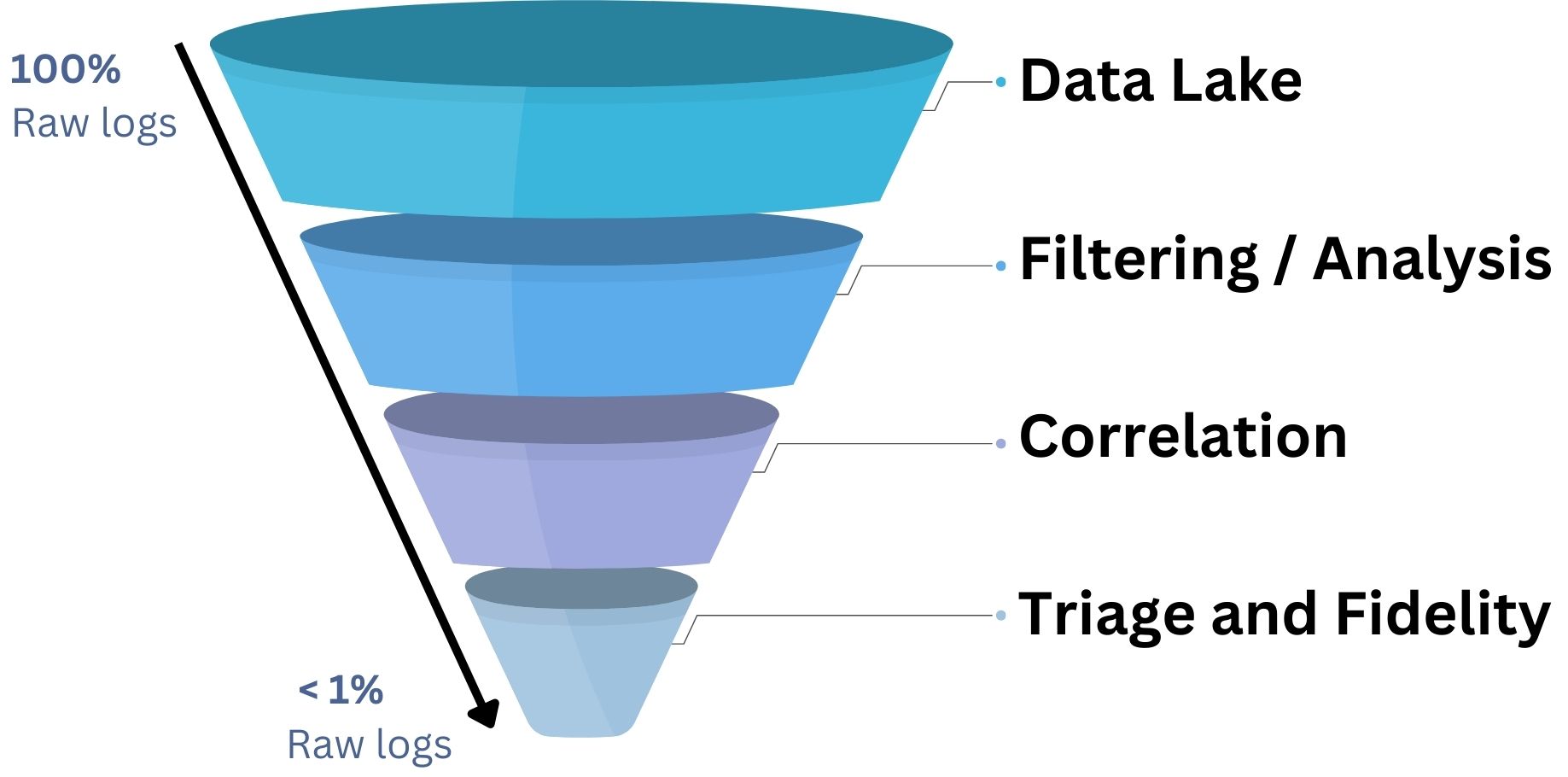
Together, effective triage and high-fidelity alerts enhance the SOC’s ability to detect, assess, and respond to security threats promptly and efficiently.
Incident Volume
Incident Volume quantifies the total number of security alerts within a given timeframe. This metric directly impacts SOC operations, as a high volume of incidents can lead to Alert Fatigue where analysts become overwhelmed by the sheer number of alerts, potentially causing critical alerts to be overlooked.

Managing incident volume effectively is crucial for maintaining operational efficiency and ensuring that SOC teams can swiftly identify and respond to genuine threats. Minimizing Alert Fatigue is essential to keep SOC responses both vigilant and precise.
Enterprises tackle this problem by implementing solutions like Security Information and Event Management (SIEM) and Extended Detection and Response (XDR), which strategically correlate numerous alerts into a singular, meaningful insight. This approach simplifies the response process, enhancing the SOC’s ability to act swiftly and accurately on critical threats.
False Positives/Negatives Rate
The False Positives/Negatives Rate highlights the accuracy of threat detection systems. A high rate of false positives can lead to Alert Fatigue, diverting valuable resources away from real threats, while a high rate of false negatives indicates missed detections, leaving the organization vulnerable. SOCs strive to minimize these rates to ensure that alerts are both reliable and actionable. Achieving a balance enhances incident handling efficiency, allowing SOCs to focus on genuine threats and maintain a strong security posture against potential cyber attacks.
Not to get confused with Triage and Fidelity which focus on prioritizing incidents and the trustworthiness of alerts respectively. They are about the quality and prioritization of the alerts, ensuring they are worthy of investigation. However, the False Positives/Negatives Rate specifically measures the accuracy of these alerts.
Reducing false positives/negatives is about refining detection systems to improve this quality further. These metrics are closely related, with each playing a unique role in enhancing SOC operations and ensuring resources are focused on real threats.
Conclusion
Throughout this blog, we’ve explored various metrics that are essential for assessing and enhancing the performance of Security Operations Centers (SOC). Our goal was to illuminate the significance of these metrics. They are not just numbers, they are the guiding stars for SOCs, ensuring that every action taken is precise, efficient, and impactful.
We aimed to draw your attention to the critical role these metrics play. They are the foundation upon which the continuous improvement of cybersecurity defenses is built. Understanding and applying these metrics means not only reacting to threats but anticipating them, ensuring your SOC operates at its peak.
Moreover, modern cybersecurity platforms have revolutionized how we detect, respond to, and measure threats. These platforms are not just tools for defense, they are instruments that allow us to quantify our security posture, making the invisible visible. They enable SOCs to not only respond to threats with speed and accuracy but also to track and improve these responses over time.