AES, or Advanced Encryption Standard, is a cornerstone in modern cryptography, renowned for its robustness and widespread use. Developed to replace the older DES (Data Encryption Standard), AES was established as a federal standard by the U.S. National Institute of Standards and Technology (NIST) in 2001.
What sets AES apart is its block cipher algorithm, which encrypts data in fixed-size blocks (128 bits). It offers three key sizes – 128, 192, and 256 bits – with the 256-bit key being the most secure. AES’s strength lies in its simplicity and efficiency. It can run on a variety of platforms, from powerful servers to small embedded devices, maintaining strong security across diverse applications.
One of the reasons AES is so reliable is its resistance to all known practical cryptographic attacks. For instance, brute-force attacks, which involve trying every possible key, are impractical due to the sheer number of potential combinations, an astronomically high number, especially with the 256-bit key.
AES’s design is such that it combines several cryptographic concepts like substitution and permutation, in a way that maximizes security while keeping the algorithm efficient and fast. This balance between speed and security makes AES a go-to choice for securing sensitive data in a range of industries, from finance to government communications, and is a testament to its reliability and special status in the world of encryption.
The Chosen CPU
In our theoretical estimation of the power required to crack AES encryption keys, we’ve chosen the AMD Threadripper 3990X processor as our benchmark. This selection is due to its status as one of the most powerful CPUs available at the time of writing this blog.
The AMD Ryzen Threadripper 3990X stands out with its impressive specifications:
- It boasts 64 cores and 128 threads, providing a formidable foundation for handling complex computational tasks
- The processor operates at a base clock frequency of 2.9 GHz, but can ramp up to 4.3 GHz under certain workloads, thanks to Turbo Core technology
- It has a substantial L3 cache size, with sources citing either 128 MB or 256 MB. This large cache aids in faster data access and processing
- The Ryzen Threadripper 3990X is built on a 7 nm production process and contains about 30,400 million transistors, indicating a highly efficient and compact design
- This CPU features a quad-channel memory interface supporting up to 2TB of memory and includes extensive PCI-Express generation 4 support, enhancing its connectivity and bandwidth capabilities
What it Takes to Crack AES Encryption Key
To estimate the computational power required to crack AES encryption keys, we need to understand the formula for calculating Operations Per Second (OPS). This formula is critical for understanding how fast a processor like the AMD Threadripper 3990X can attempt to break an encryption key through brute-force methods.

Here’s the formula for Operations Per Second:
- Cores: This represents the number of independent processing units in the CPU. In our case, the AMD Threadripper 3990X has 64 cores. More cores generally mean more simultaneous operations.
- Clock Speed (Hz): The number of instruction cycles a CPU can execute in one second. It is measured in cycles per second (Hertz, Hz). For the Threadripper 3990X, it ranges from 2.9 GHz (base) to 4.3 GHz (turbo).
- Operations Per Cycle: This term varies depending on the CPU’s architecture. It signifies how many operations a core can perform in one clock cycle. The specific number of operations per cycle can depend on various factors, including the type of operation and the CPU’s design.
We chose cores over threads because each core is an actual physical unit within the CPU, capable of performing independent tasks. While threads, enabled by hyperthreading, can increase efficiency by allowing cores to handle multiple tasks simultaneously, they don’t equate to the full capability of an individual core. Hence, cores provide a more realistic measure of raw computational power.
Let us fill in the formula:
- Cores: 64
- Maximum Clock Speed: 4.3 GHz (or 4,300,000,000 Hz)
- Operations Per Cycle: This is a variable factor and heavily depends on the CPU’s architecture and the specific operation. For our calculation, let’s assume a conservative estimate of 4 operations per cycle, a typical value for many modern processors.
Using the AMD Threadripper 3990X at its maximum capacity, the theoretical number of AES keys that can be brute-forced per second is approximately 1.1 trillion (1,100,800,000,000) operations.

It’s important to note that this is a theoretical maximum, not accounting for real-world factors like software efficiency, AES algorithm implementation, Parallelization, and many other overhead factors. Even with this immense power, it highlights the immense challenge of brute-forcing modern encryption like AES.
So if one CPU brute-forces 1.1 trillion keys per second, then how long would it take to brute-force the complete AES 128-bit?
To estimate the time it would take for the AMD Threadripper 3990X to brute-force an AES 128-bit key, we need to consider the total number of possible keys and the rate at which keys can be tested.
With the Threadripper 3990X brute-forcing approximately 1.1 trillion keys per second, we calculate the time as follows:
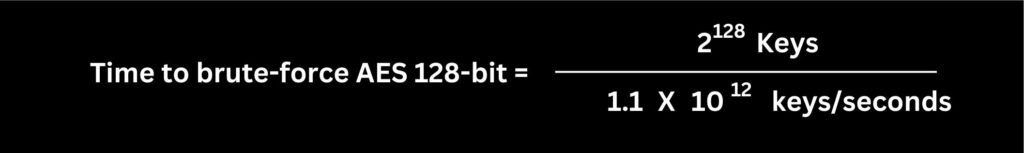
Let’s calculate this time.
Using the AMD Threadripper 3990X to brute-force an AES 128-bit key, it would take approximately 9.81×1018 years (9.81 quintillion years). This staggering duration, spanning billions of billions of years, highlights the impracticality of brute-forcing AES 128-bit encryption even with one of the most powerful CPUs currently available. It underscores the formidable strength of AES encryption and why it remains a standard in securing data against unauthorized access.
Let us imagine all the computers in the world are on a mission to crack an AES 128-bit key. We assume the total number of computers in the world is 100 Billion, and to make that even more fun, assume all of them are using the same CPU processor that we are considering in this example AMD Threadripper 3990X. To estimate the time, we multiply the brute-forcing rate of a single CPU by 100 billion and then calculate the time as before.
With each Threadripper 3990X capable of brute-forcing approximately 1.1 trillion keys per second, 100 billion of these CPUs would collectively brute-force 1.1×1012 × 1011 keys per second.
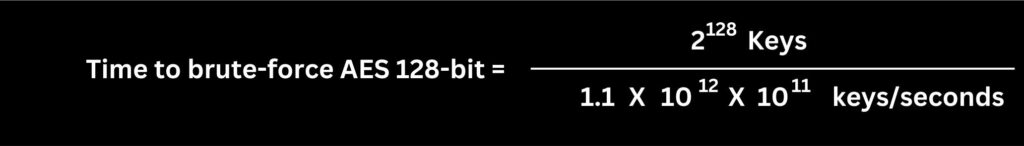
Let’s calculate the time it would take all these machines combined to crack an AES 128-bit key.
If 100 billion AMD Threadripper 3990X machines were combined to crack an AES 128-bit key, it would take approximately 98 million years. This calculation, while significantly lower than the time required by a single CPU, still shows a time span that is far beyond practicality. It vividly illustrates the formidable security provided by AES 128-bit encryption, even when faced with an unimaginably large network of powerful computers.
In this blog, we’ve explored the theoretical aspect of breaking an AES key, using calculations rather than practical lab tests. Our formula demonstrates the immense challenge of brute-forcing even a 128-bit AES key, let alone larger ones like 192-bit or 256-bit. I encourage you to apply this calculation structure to these keys as well, to gain a deeper appreciation of the strength and reliability of AES encryption in securing data.