Table of Contents
Did you know that the majority of cyber breaches exploit basic vulnerabilities? Do you know why some organizations thrive in the face of cyber threats while others falter? Isn’t it curious how a single overlooked risk can cascade into a major breach?
Welcome to a world where the answers to these questions lay the foundation for robust cybersecurity strategies. As we embark on this lesson, we will demystify cyber risks, revealing the science behind every risk management decision. This journey will take us through the maze of challenges, methodologies, and best practices that remain at the forefront of today’s digital transformation. By choosing to immerse yourself in this course, you’ve chosen to empower yourself, knowledge, and a gain deeper understanding of the risk management in cybersecurity. Together, let’s navigate the fine details of cyber risk management, laying the groundwork for a safer, more secure cyberspace.
An Email from the CEO to a Newly Hired CISO
Dear Mr. CISO,
Welcome to Acme Bank Corp. Your expertise in cybersecurity and risk management is pivotal as we address our present challenges. We’ve faced issues with our processes, inventory, documentation, and many other areas, which have impacted the trust of our stakeholders and customers.
A significant budget has been allocated to ensure we elevate our risk management strategies and cybersecurity defenses within 6 month timeframe. As you are our bank is subject to many compliance and standards issues which we are already late for submission. I’m keen to see your roadmap and encourage open communication with our teams. Together, we can restore confidence, fortify our defenses, and lead Acme Bank into a new era of cybersecurity and risk management excellence.
Best wishes,
CEO
What is this Lesson About?
Welcome to an exciting lesson in cyber risk management. This lesson is inspired by an imaginary scenario at Acme Bank Corp, where you, our esteemed participant, step into the shoes of the newly appointed Chief Information Security Officer (CISO). As you navigate the challenges presented in the introductory email from the CEO, you’ll unearth the complexities, responsibilities, and strategic considerations inherent in this role.
This lesson’s objective is twofold:
Knowledge Building by diving into essential terminologies and concepts crucial to risk management. From understanding the nuances of process optimization, inventory management, and the importance of robust documentation, to unraveling the complications of compliance and standards, this lesson offers a comprehensive guide to the foundational elements of cyber risk management.
Practical Application which goes beyond theoretical understanding, the lesson prompts you to devise actionable strategies and roadmaps. Imagine yourself at the helm of Acme Bank’s cybersecurity endeavors. How would you prioritize tasks? Which strategies would provide the most bang for the buck? How can trust be restored amongst stakeholders and customers?
We designed this lesson to be easy to digest and exciting as we know the topic of Risk Management is too lengthy and can be boring if we just cover the theory part. By the end of this lesson, you will not only gain an in-depth understanding of cyber risk management but also be equipped with the tools to make informed, cost-effective decisions in real-world scenarios.
Embrace this opportunity to reshape Acme Bank’s cybersecurity future and, in the process, refine your skills and insights as a cybersecurity professional.
What is CISO?

A CISO, standing for Chief Information Security Officer, is a senior-level executive responsible for an organization’s information and data security. They formulate and implement strategies to protect sensitive data from cyber threats, ensuring the confidentiality, integrity, and availability of company assets.
In addition to technical responsibilities, a CISO plays a significant role in bridging communication between IT departments and executive leadership. They often lead cybersecurity teams, manage budgets, and navigate compliance regulations, all while maintaining an organizational culture focused on security awareness and best practices.
You Just Started

While reading this lesson, we want you to imagine always that you are the CISO guy who owns the complete responsibility of the cyber risk management mission. You have just started, your credentials are provided, and you have access to your computer. Your team is presented to you, so you now know each of them.
Acting as a CISO, particularly in a challenging environment like Acme Bank Corp, demands a blend of technical prowess, leadership skills, and strategic foresight. Here’s a typical roadmap for initial preparation:
- Equip Yourself
Before diving into the complexities of your role, ensure that your credentials and corporate computer accesses are in order. Familiarize yourself with the systems, software, and security protocols that Acme Bank Corp uses. It’s essential to be comfortable with the tools of your trade. - Understand Your Team
Spend quality time getting to know your team members individually. Recognize their strengths, areas for growth, and professional aspirations. While they might lack extensive experience, every member can bring a unique perspective to the table. It’s important to appreciate their competencies and understand the training or resources they might need. Leading an inexperienced team can be a challenge but also a rewarding opportunity. - Prioritize Education
Invest in regular training sessions. Focus on both hard skills, like understanding specific cybersecurity tools and protocols, and soft skills, such as effective communication and critical thinking. - Foster Open Communication
Create an environment where team members feel comfortable sharing concerns, asking questions, and suggesting improvements. As the CISO, you are their guide, and it’s crucial they feel supported in their roles. - Set Clear Expectations
Outline your vision for Acme Bank Corp’s cybersecurity future. With clear objectives, it’s easier for your team to align their efforts and understand the bigger picture.

Embrace your role as a mentor. Remember, the combined strength of a cohesive, well-guided team can often surpass the capabilities of a few experienced individuals. Your leadership can be the driving force that propels Acme Bank Corp’s cybersecurity measures to new heights.
These foundational steps enable you to establish a strong, cohesive cybersecurity team equipped to address Acme Bank Corp’s unique challenges. By understanding assets, technology, tools, compliance requirements, and teams, prioritizing education, fostering open communication, and setting clear expectations, you can more effectively identify, assess, and mitigate cyber risks. A well-prepared and united team is significant in creating a robust risk management framework. Thus, these steps not only streamline internal operations but also enhance the bank’s overall cybersecurity posture, ensuring stakeholder trust and regulatory compliance are maintained.
What Does “Risk” Mean in General?
The concept of risk is as ancient as human civilization. At its core, risk represents the potential for an action or event to result in an undesirable outcome. Historically, risk has been a constant companion to humankind. Think of ancient traders navigating treacherous seas, risking their lives and cargo for the promise of trade and profit. Or farmers in earlier civilizations, who bet their livelihoods on the unpredictability of weather patterns, praying for a bountiful harvest. These historical examples underscore the inherent nature of risk: the uncertainty of outcome.

Risk has been a topic of interest across various fields and disciplines. In business finance, risk signifies the chance that an investment’s actual returns will differ from the expected outcomes, influencing decisions about where and how money is invested. Project managers grapple with risks tied to timelines, resources, and the potential challenges a project may encounter. Understanding and managing these risks ensures projects meet their objectives within scope, time, and budget constraints.
Put simply, risk is tied to the unpredictability of life. It relates to the uncertainty of outcome, which could manifest as a positive opportunity or a negative threat. For instance, investing in a start-up is risky because while there’s a chance of it becoming the next big tech giant, there’s also a possibility it could fail. Similarly, launching a new product in the market can lead to substantial profit and market share (opportunity) or result in losses if the product doesn’t resonate with consumers (threat).
By this definition, imagine a business that has been informed it will face a regulatory fine in one month due to a past compliance failure. This event is certain, so it’s no longer a “risk” in the traditional sense. Instead, it becomes a “liability” or “obligation” the business must address. The focus shifts from assessing the likelihood of the event to preparing for its financial and reputational impact, ensuring that necessary funds are available, and implementing measures to prevent similar compliance failures in the future.
Or a company’s break room vending machine has a 90% likelihood of malfunctioning in the next month. However, since it has no bearing on the company’s operations, financials, or reputation, its impact is 0.0%. Thus, even with a high probability, it’s not considered a risk due to its inconsequential impact.
Yet, the way we perceive and define risk has evolved over time. In modern parlance, the risk is often articulated as the likelihood of a threat agent exploiting a vulnerability and the consequent business impact. This is a more structured approach, balancing the probability of an event occurring against its potential repercussions. For example, in the context of a business, if a company operates in a region prone to natural disasters without adequate insurance or protective measures, the risk is not just the likelihood of a disaster occurring, but also the damage it could inflict on the company’s operations and bottom line.
The same principle applies in cybersecurity where the risk is a function of the likelihood of a cyber threat (like a hacker) exploiting a vulnerability (like an unpatched software) and the resultant harm to the organization, be it financial, reputational, or operational.
So, if risk is defined in various ways and understood differently across fields, where does that leave us? It’s crucial to recognize that while the specifics might vary, the underlying essence remains consistent; risk embodies the potential for unwanted outcomes arising from inherent uncertainties. In this lesson, we dive deep into cyber risks, which, though a more recent subset of risks, draws on these age-old principles of uncertainty and potential adverse outcomes.
What is Cyber Risk?
Cyber risk pertains to the potential threats and vulnerabilities associated with electronic data and the computer systems used by organizations. Today, every action, from sending an email to processing transactions, can be vulnerable to cyber threats. Such risks can emanate from a variety of sources, including cybercriminals, insider threats, and even state-sponsored actors. Common manifestations include malware, ransomware, phishing schemes, and distributed denial-of-service (DDoS) attacks. The consequences of these threats can range from loss of data and compromised systems to financial losses and severe reputational damage.
While traditional business risks like credit, market, or operational risks have been around for centuries and can often be quantified and managed using established methods, cyber risk is relatively new and inherently more dynamic. Traditional risks might be influenced by economic factors, market dynamics, or internal operational challenges. In contrast, cyber risks evolve rapidly, influenced by technological advancements and an ever-shifting landscape of threat actors. Unlike other risks where historical data can guide future predictions, the digital realm offers limited historical precedent. Moreover, cyber risks can be highly interconnected, where a breach in one area can ripple across multiple facets of a business, sometimes with global implications.
Managing cyber risk is substantial in the digital era for several reasons. Firstly, the sheer dependency on technology means that any disruption can severely impact business continuity. A cyber incident can halt operations, leading to direct financial losses. Secondly, breaches often result in the exposure of sensitive data, which can erode customer trust and lead to regulatory fines. With data privacy laws becoming stricter globally, organizations face both reputational and financial penalties for lapses. Furthermore, as businesses become more interconnected, a vulnerability in one organization can jeopardize its partners, stakeholders, and the broader industry. Therefore, managing cyber risk isn’t just about self-preservation; it’s about upholding the trust and security of the entire digital ecosystem.
Why Business Should Care about Cyber Risks?
Historically, cybersecurity was often siloed, viewed primarily as an IT concern rather than a holistic business risk. Several factors contribute to this perception among C-Executives. Traditional business risks, like financial or operational challenges, present immediate, tangible consequences, whereas cyber risks, being digital, might appear intangible until a breach occurs. The dynamic and technical nature of cyber threats can be daunting. Without a tech background, some executives may struggle to grasp the small differences, leading to a possible underestimation of its impact. Additionally, the rapid evolution of cyber threats means that today’s solutions might be obsolete tomorrow, creating a sense of perpetual catch-up, which can be overwhelming. Lastly, there’s a historical precedence: business schools and traditional executive training programs historically didn’t emphasize cybersecurity, making it a newer frontier for many seasoned executives. As a result, while they might acknowledge its importance, they might not fully internalize its potential business ramifications.
By successfully managing cyber risks for a bank leads to a cascade of positive outcomes, both tangible and intangible:
- Enhanced Customer Trust
- Accelerate Compliance
- Business Continuity
- Stabilize the Business
- Competitive Edge
Understand the Current Landscape Before Managing the Risks
As a newly appointed CISO at Acme Bank Corp, it’s essential to gauge the cybersecurity terrain before charting any strategic path. To deep dive into understanding the current landscape, you need to assess the situation by beginning with a comprehensive audit of the existing security infrastructure. This is akin to a doctor’s diagnosis before prescribing treatment. Analyze the effectiveness and gaps in current security measures. Have there been past security breaches? If so, what lessons were learned, and how have they shaped current protocols?
Furthermore, recognize the vulnerabilities that may not have been exploited yet but pose potential threats. Utilize both internal resources, like IT teams, and consider external audits for an unbiased view. Sometimes, an outsider’s perspective can shed light on blind spots that internal teams might overlook.
This foundational step isn’t just about gathering data but interpreting it in a way that provides a clear picture of where Acme Bank stands in its cybersecurity journey. Once you have this snapshot, it will become significantly easier to determine subsequent moves, prioritize resources, and communicate the urgency and importance of certain initiatives to other stakeholders.
Remember, knowledge is power. In the realm of cybersecurity, a thorough understanding of your starting point is crucial to determining the right path forward, aligning resources, and ensuring the safety of both Acme Bank and its valued customers.
Types of Audits

- Internal Audit
An internal audit is conducted by the organization’s own employees or a dedicated internal audit team. This audit scrutinizes the internal controls, processes, and mechanisms in place to ensure they align with established cybersecurity standards and best practices.
How does it benefit the CISO?
Internal audits offer firsthand insight into the day-to-day operations and security protocols of the bank. As these are carried out by insiders, they often benefit from a deep understanding of the organization’s culture, systems, and structures. For a CISO, this type of audit provides a ground-level view, helping identify areas of improvement in existing processes and pinpointing potential vulnerabilities in routine operations. - External Audit
An external audit is performed by independent entities or professionals who are not affiliated with the organization. Their primary goal is to provide an unbiased evaluation of the organization’s cybersecurity posture and ensure compliance with industry standards and regulations.
How does it benefit the CISO?
The primary advantage of an external audit lies in its objectivity. External auditors come without preconceived notions or biases related to the bank’s operations. Their findings can validate or challenge the conclusions of internal audits. For a CISO, this impartial perspective is invaluable, ensuring that the organization’s security measures are not just effective internally but stand up to external scrutiny and industry benchmarks. - 3rd Party Audit
An external audit is conducted by certified professionals who are not affiliated with the organization. Its primary goal is to evaluate the organization’s compliance with specific industry standards, regulations, or frameworks such as ISO 27001, HIPAA, GDPR, etc. These auditors work based on a predefined set of criteria that align with these standards, offering a formal attestation of the organization’s adherence to them.
How does it benefit the CISO?
External audits provide validation that the organization’s cybersecurity and data protection practices align with widely accepted standards and regulations. For a CISO, this third-party validation is essential not only for compliance but also for building trust with stakeholders, partners, and customers. Additionally, the recommendations from these certified auditors provide a roadmap for improvements, ensuring the bank’s cybersecurity measures are not just compliant, but also effective against evolving threats.
Inventory and Asset Management
Inventory and Asset Management is the systematic process of identifying, categorizing, documenting, and managing all digital assets within an organization. This includes hardware (like servers and workstations), software (both commercial and proprietary applications), data repositories, and network components.
Knowing what you have is foundational to protecting it. Without a clear understanding of all assets, it’s impossible to apply appropriate security measures, leaving potential vulnerabilities unnoticed and unaddressed.
The CISO can initiate automated asset discovery tools that periodically scan the network, cataloging and documenting new assets. Integrating this with configuration management databases (CMDB) can ensure assets are not just identified but also correctly configured. Regularly scheduled reviews, perhaps quarterly or bi-annually, can validate the inventory’s completeness and accuracy.
To ensure continuous updates, the CISO can implement a system of checks and balances wherein the procurement of any new asset or decommissioning of an existing one mandates an update to the inventory. Automated alerts for unauthorized changes can also be set up, ensuring real-time inventory integrity.
An accurate asset inventory is the bedrock of risk assessment. Once you know what assets you have and where they are, you can evaluate the risks associated with them. It allows the organization to prioritize resources, focusing on assets that, if compromised, would pose the greatest risk. Moreover, in the event of a security incident, a well-maintained inventory can expedite response times, as security professionals won’t waste crucial moments trying to identify affected assets. Throughout the risk management lifecycle from identification and assessment to mitigation and monitoring an accurate and up-to-date asset inventory is pivotal.
A CMDB is a centralized repository that stores details about IT assets and their configurations. It provides a structured view of the assets' relationships, dependencies, and configurations. CMDB tracks assets throughout their lifecycle, from procurement to decommissioning. Integration with assets ensures that any changes to an asset's configuration are recorded in real-time, offering a continually updated snapshot of the organization's IT environment, enhancing decision-making and risk assessment.Quick Quiz
Choose Risk Management Framework
A Risk Management Framework (RMF) is a structured and standard approach to identifying, assessing, and managing risks. It provides structured guidance on the entire risk management lifecycle, from initial risk identification to ongoing monitoring and mitigation.
Selecting a standard framework is essential because it offers a consistent, tried-and-tested methodology built on best practices. It ensures that the organization’s approach to risk is comprehensive, aligned with industry standards, and recognizable to stakeholders, partners, and regulators.
Ignoring a structured RMF can lead to a piecemeal, reactive approach to threats, potentially leaving vulnerabilities unnoticed. Inconsistencies in risk management processes might arise, leading to gaps in security measures and increased susceptibility to breaches.
While organizations can create their own bespoke RMF, it comes with challenges. A custom framework may lack the rigor and comprehensiveness of standard ones. It may not be readily understood or accepted by external stakeholders, potentially complicating regulatory compliance or partnership discussions. Additionally, developing a proprietary framework can be resource-intensive and may not provide the same level of assurance as adopting a globally recognized standard. While custom frameworks offer tailor-made solutions, they may lack the credibility, efficiency, and thoroughness of established RMFs. For most organizations, especially those operating in complex environments like banking, leveraging a standard framework proves both effective and prudent.
After an exhaustive research and evaluation phase, the CISO of Acme Bank Corp recognized the need for a Risk Management Framework that would not only meet the bank’s unique challenges but also align with global best practices. Navigating through numerous frameworks, considering their merits and adaptabilities, he was drawn to the structured yet flexible approach of ISO 27005. Recognizing its integration with the broader ISO 27000 series and its wide acceptance in the international business community, he discerned its potential for Acme Bank Corp. ISO 27005’s emphasis on a systematic, iterative risk management process, combined with its holistic view of information security, positioned it as the ideal choice. By electing ISO 27005, the CISO is making a strategic move to fortify Acme Bank Corp’s cybersecurity posture and align its operations with globally recognized standards.

FYI, there are many popular and standard Risk Management Framework other than ISO 27005. Such as;
NIST SP 800-37, developed by the U.S. National Institute of Standards and Technology, this RMF provides guidelines for applying the risk management process to federal information systems.
COSO ERM Framework, the Committee of Sponsoring Organizations of the Treadway Commission (COSO) has an Enterprise Risk Management (ERM) framework that emphasizes aligning risk appetite and strategy.
ISO 31000, an international standard that provides guidelines on creating a risk management framework and process.
FAIR (Factor Analysis of Information Risk), a quantitative framework for cybersecurity and operational risk.
OCTAVE (Operationally Critical Threat, Asset, and Vulnerability Evaluation), originated by CERT, OCTAVE is a suite of tools, techniques, and methods for risk-based information security strategic assessment and planning.
ITIL (Information Technology Infrastructure Library), while primarily known for its approach to IT service management, ITIL has processes related to risk management that organizations can incorporate.
COBIT (Control Objectives for Information and Related Technologies), this framework from ISACA integrates principles of enterprise governance and management of IT, including risk.
Risk IT, another framework by ISACA, it complements COBIT and emphasizes risk management, focusing specifically on IT risks.What is ISO 27005
ISO/IEC 27005 is an international standard dedicated to information security risk management. Rather than prescribing specific measures or actions, it offers a logical and structured approach to risk management within the context of an Information Security Management System (ISMS). The framework outlines processes for risk assessment, risk treatment, monitoring, and review, as well as offering guidance on the methodology’s application across varied organizational contexts. ISO 27005 emphasizes the importance of a cyclical, iterative approach, ensuring continuous improvement and adaptation in the face of evolving threats. This standard is particularly powerful when used in conjunction with ISO/IEC 27001, which provides requirements for establishing, implementing, and maintaining an ISMS. Together, they offer organizations a robust toolkit for both understanding their cyber risks and addressing them in a methodical, consistent manner.
Please note that ISO 27005 is not a free document. It is paid and can be found here:
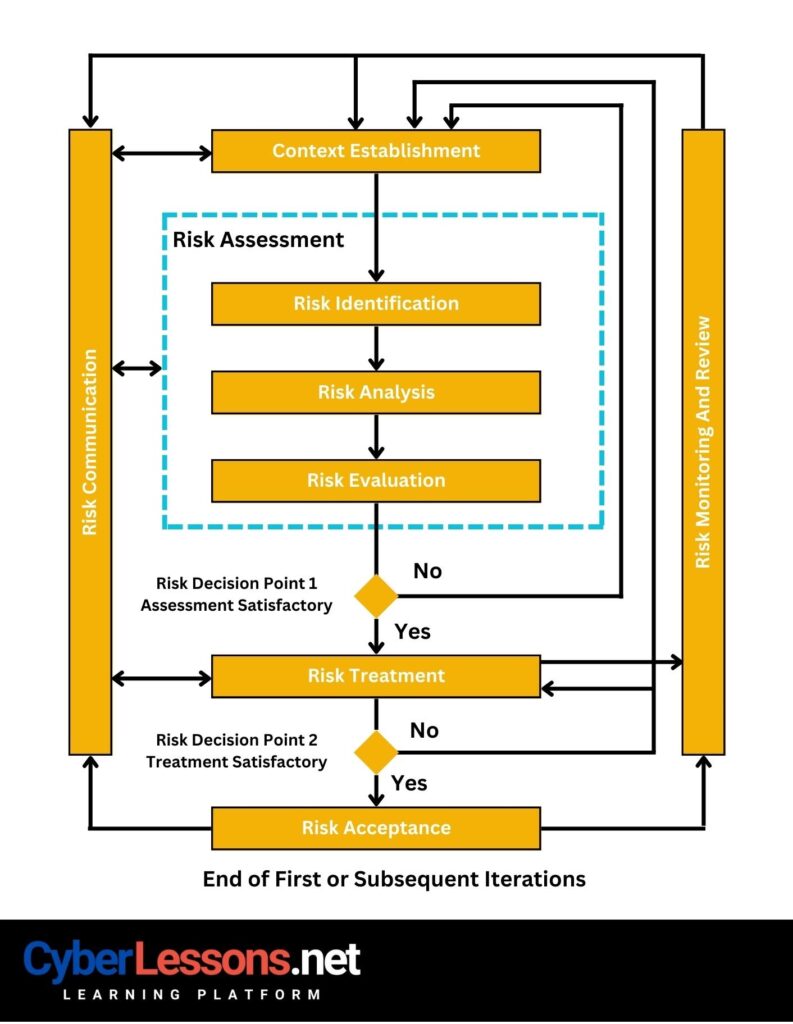
ISO 27005: Context Establishment
Context Establishment is the initial phase where the organization defines the scope and boundaries of its information security risk management efforts. It encompasses understanding the business environment, objectives, needs, and constraints, ensuring that the risk management process is tailored to the organization’s unique circumstances.
In the ISO 27005 RMF, this phase is crucial as it lays the foundation for the entire risk management process. By clearly establishing context, the organization ensures that risk assessments are relevant, comprehensive, and aligned with business goals. This phase adds significant value by making subsequent steps more focused and effective, ensuring that resources are aptly utilized and risks are prioritized in line with the broader organizational landscape and objectives. Essentially, it anchors the RMF in the realities of the organization, making the framework both actionable and impactful.
Tailoring
Tailoring involves adjusting the risk management process to fit the specific characteristics and needs of the organization. For example, If the bank primarily uses cloud services, its risk management practices might be tailored to emphasize cloud security measures and protocols.
Scoping
Scoping defines the boundaries and limits of the risk management process, identifying what is included and what is excluded. For example, in the bank, the initial risk management efforts might be scoped to focus solely on the payment systems, leaving other systems for subsequent assessments.
ISO 27005: Risk Assessment
Risk Assessment is the process of identifying, analyzing, and evaluating risks associated with an organization’s information assets. It provides a structured way to understand potential threats, their likelihood of occurrence, and their potential impact on the organization.
The importance of Risk Assessment is that it directly informs decision-making. Without a clear understanding of risks, organizations are navigating blind, making them vulnerable to unforeseen threats. Risk Assessment illuminates the path, revealing where defenses are robust and where they are lacking.
For a CISO, the Risk Assessment process is thought of a diagnostic health check. Just as a doctor needs to understand a patient’s symptoms, history, and potential issues before prescribing treatment, a CISO must grasp the full landscape of risks before determining the best security measures. This clarity ensures that resources both time and money are directed efficiently, addressing the most pressing threats first.
Furthermore, Risk Assessment is the foundation upon which other elements of the risk management process are built. Risk treatment or mitigation strategies are directly derived from the outcomes of the risk assessment. Monitoring and review activities are, in turn, aligned to the identified and treated risks, ensuring that the organization remains vigilant to the most pertinent threats.
Risk Assessment translates abstract threats into concrete data, allowing organizations to move from vague concerns about “what might happen” to targeted strategies addressing “what we need to prepare for.” For a CISO, mastering this phase is paramount. It provides the data-driven insights essential to build a robust, resilient, and responsive cybersecurity infrastructure, ensuring that the organization is not just reactive but proactively prepared for evolving cyber challenges.
Risk Assessment is often represented in a tabular format, providing a clear and organized overview of identified risks, their potential impact, likelihood of occurrence, and corresponding mitigation strategies. While simple risk assessments might use Excel sheets for this purpose, larger organizations or those with more complex IT infrastructures typically employ more sophisticated tools, like CMDB solutions. CMDBs not only allow for a structured representation of risks but also facilitate real-time updates, integrations with other IT management tools, and advanced analytics capabilities. Whether using basic spreadsheets or advanced CMDB solutions, the goal is to provide a clear, actionable view of risks, making it easier for decision-makers to prioritize and address them.
ISO 27005: Risk Identification
Risk Identification is the foundational step in the Risk Assessment phase, pinpointing potential vulnerabilities and threats that an organization might face. It operates as a thorough examination, diving deep into an organization’s systems, processes, and operations to uncover weak points and areas susceptible to cyber threats. The reason it’s the initial step under Risk Assessment is simple: before an organization can analyze or evaluate risks, it must first know what those risks are. Think of it as a doctor’s preliminary diagnosis – before determining the severity of an illness or deciding on treatment, the doctor first identifies the symptoms and underlying issues. For a robust cybersecurity posture, it’s imperative to start with a clear and comprehensive understanding of all potential vulnerabilities and threats, ensuring subsequent steps in the Risk Assessment process are grounded in comprehensive knowledge.
Let us Imagine you acting as the CISO have launched a Risk Identification process and discovered the following 5 Risks in the bank. Typically in the real world, you will find far more than that, but we take this as an example!
| # | Vulnerability | Impact |
|---|---|---|
| 1 | Unpatched software in ATM systems | Unauthorized withdrawals, fraudulent transactions, compromise of customer financial data |
| 2 | Weak employee password policies | Unauthorized access to sensitive data, potential data breaches |
| 3 | Outdated firewall configurations | Breach of internal network, potential data theft or malware introduction |
| 4 | Lack of encryption in mobile banking applications | Exposure of customer banking details, unauthorized transactions |
| 5 | Inadequate employee cybersecurity training | Accidental data leaks, increased susceptibility to phishing attacks |
When the CISO initially identifies and lists out the risks without considering any controls or mitigation measures that are in place, this is referred to as “Inherent Risk.” It represents the raw or natural risk exposure that an organization would face if no action were taken. In the case of Acme Bank Corp, the table created by the CISO displayed these inherent risks. Understanding inherent risk is crucial because it provides a baseline that shows the potential severity of threats if left unaddressed. This baseline then guides the organization in determining the appropriate controls and mitigation strategies to implement, ultimately leading to the determination of residual risk post-mitigation.
ISO 27005: Risk Analysis
Risk Analysis goes much deeper into the risks that have been identified, quantifying and characterizing them to comprehend their potential implications for the organization. At its core, Risk Analysis focuses on two primary facets: the likelihood of a particular risk materializing and the potential impact or harm it could cause if it does. By examining these two dimensions, organizations gain a clearer understanding of the severity and priority of each risk.
Now, a common area of confusion is the distinction between Risk Assessment and Risk Analysis. While they’re closely related, they serve different functions. Risk Assessment is the broader process encompassing the entire journey of recognizing, analyzing, and evaluating risks. It’s the umbrella term. Within this journey, Risk Analysis is a specific phase where you quantify and characterize the risks you’ve identified, essentially adding depth and detail to your understanding.
To put it simply, if Risk Identification is about spotting potential cybersecurity ailments, Risk Analysis is close to understanding just how sick the organization might get and how likely it is to happen. It’s the step that turns a list of vulnerabilities into a data-driven, prioritized understanding of threats.
Refer to the table below, which has been updated to reflect the Risk Analysis process, providing a more in-depth understanding of the vulnerabilities and their potential impact on Acme Bank Corp.
| # | Vulnerability | Impact | Likelihood | Risk |
|---|---|---|---|---|
| 1 | Unpatched software in ATM systems | Unauthorized withdrawals, fraudulent transactions, compromise of customer financial data | High | Critical |
| 2 | Weak employee password policies | Unauthorized access to sensitive data, potential data breaches | Very High | High |
| 3 | Outdated firewall configurations | Breach of internal network, potential data theft or malware introduction | Medium | High |
| 4 | Lack of encryption in mobile banking applications | Exposure of customer banking details, unauthorized transactions | High | Critical |
| 5 | Inadequate employee cybersecurity training | Accidental data leaks, increased susceptibility to phishing attacks | Very High | Medium |
At the core, risk is often conceptualized as a function of the likelihood (or probability) of a particular event occurring and the impact (or consequences) that event would have if it were to occur. Mathematically, it can be represented as:

By multiplying likelihood with impact, organizations can assign a quantifiable value or score to the risk. This resultant risk score helps in prioritizing risks: a high likelihood combined with a high impact would yield a high risk score, indicating a critical risk that needs urgent attention. On the other hand, a low likelihood combined with low impact would suggest a lower priority risk.
Using this calculated risk value, organizations can make informed decisions about which risks to mitigate immediately, which to accept, and which to monitor. This process ensures that resources are deployed efficiently, addressing the most significant threats first.
It's crucial to note that our illustration here is a simplified representation for educational purposes. In real-world business scenarios, risk management is a far more complex process. Additionally, our approach in this lesson leans towards Qualitative Risk Assessment. There's also Quantitative Risk Assessment, which dives into numerical metrics and is a more complex methodology.Risk Matrix
A risk matrix is a powerful visual tool used to ascertain and communicate the severity of risk events. At its core, it operates by correlating the likelihood of an event with its potential impact, producing a graphical representation of overall risk. The Risk Assessment table formulated by the CISO is deeply anchored in this methodology, with vulnerabilities being mapped against their likelihood and potential impact to determine the overall risk.
There are various dimensions to risk matrices, the most common being 3×3 and 5×5. The choice between them often hinges on the desired granularity and the complexity of the environment being assessed.
A 3×3 matrix is relatively straightforward and is beneficial for organizations or scenarios where risks are not overly complex and where a high-level overview suffices. It provides a simple classification – usually categorized as low, medium, and high – for both likelihood and impact. For many small to mid-sized businesses or less complex environments, this provides ample differentiation between risks to drive decision-making.
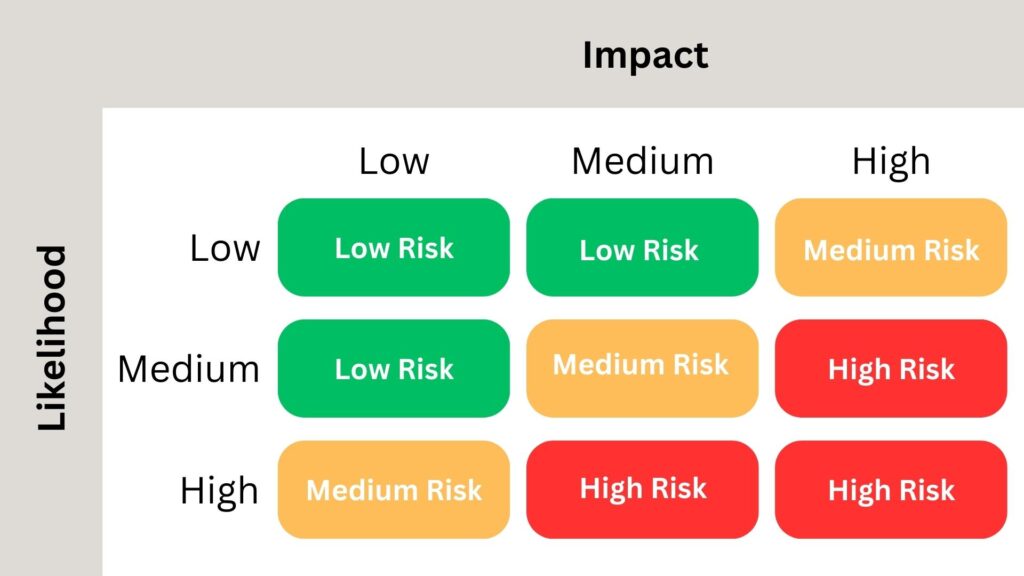
On the other hand, the 5×5 matrix offers a more detailed view, allowing for a finer granularity in risk assessment. The five levels – often labeled as very low, low, medium, high, and very high – offer a more detailed differentiation, crucial for larger organizations or more complex risk landscapes. Such a matrix becomes invaluable when the distinctions between risk levels are razor-thin, requiring a more in-depth analysis.
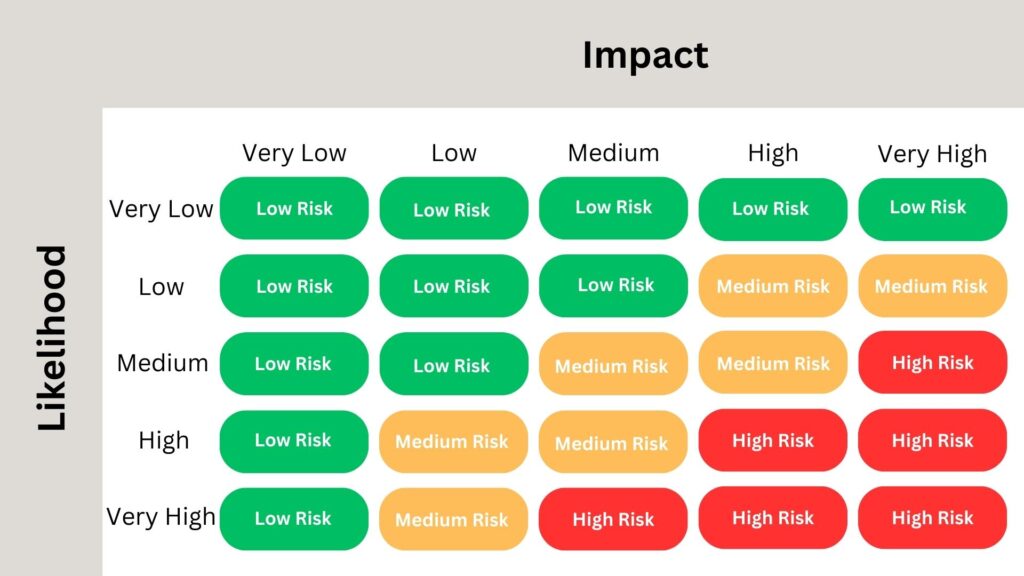
Let us talk now in more detail about what is Qualitative Risk Assessment and Quantitative Risk Assessment
Qualitative Risk Assessment
Involves assessing risks based on their subjective qualities rather than quantifiable data. It categorizes risks into rankings Matrix table like “low,” “medium,” or “high” based on expert judgment, experience, and intuition.
It is often visualized using a Risk Matrix. This matrix plots risks based on their likelihood of occurrence against their potential impact. It simplifies complex risks into a clear visual format, aiding decision-making by highlighting the most pressing concerns.
Qualitative assessment is often used when it’s challenging to obtain specific numerical data or when a quick, high-level overview of the risk landscape is required. It’s especially helpful for understanding new or emerging risks where limited quantitative data is available.
Advantages
- Simplicity; provides a straightforward, easily understandable snapshot of risks.
- Flexibility; it can be applied in scenarios with limited data.
- Collaborative; Encourages team discussions and consensus-building around risk perceptions.
Disadvantages
- Subjectivity which lacks the precision of quantitative assessments.
- Potential bias, heavily influenced by individual perceptions, which can vary.
- Limited granularity and may not capture the detailed nuances of each risk.
In our Acme Bank Corp context, a Qualitative Risk Assessment offers a rapid understanding of the bank’s major vulnerabilities. Given the immediate challenges highlighted by the CEO’s email and the need to quickly prioritize areas of concern, a qualitative approach provides an actionable overview. While it may not offer the detailed metrics a quantitative assessment would, it equips the bank’s leadership with the insight needed to make informed decisions in the short term, setting the stage for more detailed analysis down the line.
Quantitative Risk Assessment
Quantifies risks using numerical values, providing a more objective and data-driven approach to risk analysis. Instead of subjective categorizations like “low” or “high,” Quantitative Risk Assessment uses specific metrics, monetary values, or percentages.
It is employed when precise data is available and when organizations want a more detailed and objective understanding of their risk landscape. It allows for clearer prioritization based on potential financial or operational impact.
Key Terms in Quantitative Assessment:
Asset Value (AV): The worth of an asset, often expressed in monetary terms ($$$).
Exposure Factor (EF): The percentage of an asset’s value that could be lost due to a specific threat.
Single Loss Expectancy (SLE): The monetary loss ($$$) expected from a single event. It’s calculated as SLE= AV × EF
Annualized Rate of Occurrence (ARO): The estimated frequency with which a specific threat will occur within a year.
Annualized Loss Expectancy (ALE): The expected annual loss ($$$) from a risk. It’s calculated as: ALE=SLE×ARO
Let us take an example; Let’s consider Acme Bank Corp’s online transaction system as an asset. Its AV is $1 million. If there’s a cyberattack, the EF (potential data loss or downtime) is estimated at 10%. The SLE would be $100,000 ($1 million x 10%). If such attacks are expected twice a year, the ARO is 2. Thus, the ALE, or the yearly expected loss from these attacks, is $200,000 ($100,000 x 2).
In this example, when considering cybersecurity investment for Acme Bank Corp’s online transaction system, the ALE of $200,000 serves as a benchmark. Ideally, the investment should be less than the ALE, as spending more might be overprotective and not cost-effective. However, it’s crucial to strike a balance. Investing significantly less than the ALE could leave the system vulnerable. The optimal investment is one that significantly reduces the risk at a cost that is justified by the potential savings from preventing cyber incidents, while also factoring in other intangibles like reputation and customer trust.
Business Impact Analysis (BIA)
While BIA isn’t a formal component of ISO 27005, its relevance to holistic risk management cannot be understated. Given its significance in bridging the gap between technical risks and their business implications, it’s essential to discuss BIA alongside ISO 27005’s risk management processes.
Business Impact Analysis (BIA) is an analysis process that identifies and evaluates the potential effects of interruptions to critical business operations due to an incident or disaster. It gauges the potential consequences of these disruptions in terms of financial, operational, and reputational damage. BIA elevates Risk Analysis by adding a business-centric perspective, translating technical vulnerabilities into tangible business impacts and consequences.
BIA adds depth to risk management by ensuring that risks are viewed not just in terms of their likelihood and potential security impact but also in terms of their broader business consequences. By understanding the real-world implications of risks, organizations can better prioritize mitigation efforts.
Integrating BIA into the risk table matrix enriches it with a business-centric perspective. While our risk analysis highlights vulnerabilities and their potential security impacts, BIA provides insights into the broader business implications of these vulnerabilities. This dual lens ensures that risks are managed comprehensively, balancing both security and business continuity concerns.
| # | Vulnerability | Impact | Likelihood | Risk | BIA Consequences |
|---|---|---|---|---|---|
| 1 | Unpatched software in ATM systems | Unauthorized withdrawals, fraudulent transactions, compromise of customer financial data | High | Critical | Major financial loss |
| 2 | Weak employee password policies | Unauthorized access to sensitive data, potential data breaches | Very High | High | Data compromise, reputational damage |
| 3 | Outdated firewall configurations | Breach of internal network, potential data theft or malware introduction | Medium | High | Disrupted operations, data loss |
| 4 | Lack of encryption in mobile banking applications | Exposure of customer banking details, unauthorized transactions | High | Critical | Customer trust erosion |
| 5 | Inadequate employee cybersecurity training | Accidental data leaks, increased susceptibility to phishing attacks | Very High | Medium | Leaks, potential legal issues |
ISO 27005: Risk Evaluation
Risk Evaluation is the phase where the organization decides which risks are significant and must be addressed urgently. It involves comparing the results of the risk analysis against risk criteria set by the organization to determine the significance of the risk.
After the Risk Analysis phase, where the likelihood and potential impact of each vulnerability are assessed, and BIA gives a business-centric perspective, the table offers a comprehensive view of each risk. In Risk Evaluation, the CISO uses this table to prioritize risks based on the organization’s risk appetite, tolerance, and threshold. Let us identify each one of them.
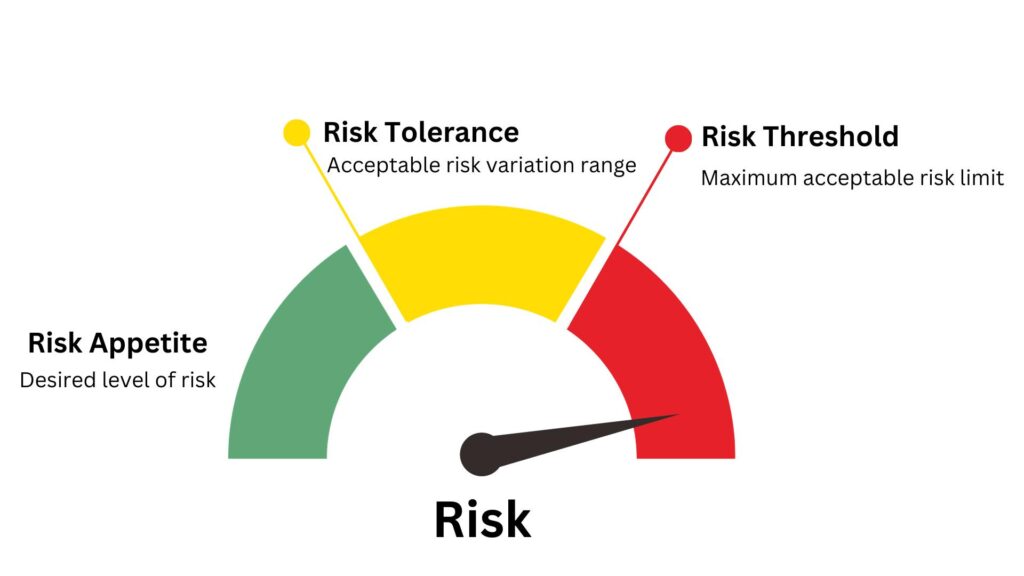
Risk Appetite refers to the total amount of risk an organization is willing to accept or take on in pursuit of its strategic objectives. For Acme Bank Corp, the risk appetite might be defined by the board or senior management. For instance, they may declare, “We aim to ensure no more than a 0.5% chance of data breaches resulting in a loss exceeding $1 million in any given year.”
Risk Tolerance, while appetite defines the overall boundary, tolerance gets more specific. It’s the degree of variance from the organization’s risk appetite that is acceptable. In our context, the CISO might determine that while the bank has a 0.5% appetite for major data breaches, it could tolerate minor breaches that don’t significantly affect the bank’s reputation or bottom line. For example, the CISO might decide that the bank has a 2% tolerance for unauthorized internal access to non-critical customer data, representing potential losses of up to $50,000 annually.
Risk Threshold is the actual “line in the sand” or the specific point at which risk becomes unacceptable. If a particular vulnerability, when analyzed, shows a potential loss of $1.5 million with a likelihood of 1%, it crosses the bank’s defined risk threshold and would be flagged for immediate attention by the CISO.
By using the table and understanding these concepts, the CISO of Acme Bank Corp can make well-informed decisions. They can prioritize risks not just based on their technical or business severity, but also in alignment with the bank’s strategic objectives and its predefined risk parameters.
Moreover, the CISO must assess the risks in the context of the organization’s objectives, operations, and external factors. For instance, a “high” risk for one organization might be a “medium” risk for another, based on their risk tolerance. The CISO, using the comprehensive table, will decide which risks to treat immediately, which ones to accept, and which ones to monitor or transfer. The CISO may also engage with stakeholders to get their input, ensuring that decisions align with business goals. In essence, this phase is about strategic decision-making, ensuring that the organization’s resources are directed toward the most critical risks.
ISO 27005: Risk Treatment
Risk treatment is the phase in the ISO 27005 risk management framework where clear-cut actions are developed to address and manage the identified risks. For our CISO at Acme Bank Corp, after having identified, analyzed, and evaluated risks using the table, it’s not enough to merely acknowledge these risks, but actions must be taken to address them.
Risk treatment is so important process in the risk management lifecycle because it aligns the identified risks with the bank’s risk appetite, tolerance, and thresholds, ensuring that the organization can achieve its objectives without undue risk. Untreated risks can materialize, leading to financial losses, damaged reputation, and even legal consequences. Simply identifying risks without treating them is considered as diagnosing an illness but not prescribing any medication or therapy; it doesn’t resolve the underlying issue.
Risk treatment is sometimes mistaken with risk response. While they are closely related, they are not the same. Risk response often refers to immediate actions taken to a specific risk occurrence, whereas risk treatment is a broader concept that encompasses developing strategies to manage risks over the long term.
Types of Risk Treatment Actions Based on ISO 27005:
- Risk Avoidance means choosing not to engage in activities that would result in the risk. For a CISO, this might involve deciding not to use a particular software known to have security vulnerabilities. In our context, if one of the vulnerabilities was tied to an outdated banking software system, the CISO might decide to avoid this risk entirely by not deploying that system. Avoidance is chosen when the potential consequences are too dire, or the cost of other treatments exceeds the benefit of the activity.
- Risk Mitigation (or Reduction) involves implementing controls to decrease the potential impact or likelihood of a risk. The CISO might apply patches, add firewalls, or conduct staff training. If, for instance, the bank faced risks due to weak staff cybersecurity awareness, a mitigation action would be regular training sessions to reduce human error. Mitigation is often chosen when the risk can’t be entirely avoided but can be brought down to an acceptable level.
- Risk Transfer involves offloading the risk to a third party. Typically, this is seen in the form of insurance. If Acme Bank Corp identified the potential for a significant financial loss due to cybercrime, the CISO might opt to purchase cyber insurance to transfer the financial risk. This strategy is often used when the potential loss is too large for the organization to bear alone.
- Risk Sharing divides the risk among several parties. In a bank scenario, the CISO might enter a partnership where both organizations share a particular software platform, thereby sharing the associated risks. This is often chosen in scenarios where collaboration or partnerships are essential, and both parties can shoulder some of the risk burden.
ISO 27005: Risk Acceptance
In the realm of risk management, particularly within the framework of ISO 27005, Risk Acceptance plays a pivotal role. It signifies a conscious decision to tolerate the presence of a specific risk without taking further mitigation actions. The decision is generally based on comprehensive assessments and an understanding that the cost of mitigation might outweigh the potential impact, or that mitigation might not be feasible.
Let’s break this down further:
ISO 27005 emphasizes the idea that not all risks need to be treated. Some can be accepted as they are, especially if the cost or effort to mitigate them would be disproportionate to their potential impact. It’s a structured approach to decide which risks are worth taking.
Residual Risk is the risk that remains after risk treatment measures have been applied. In essence, it’s the “leftover” risk. Even after implementing certain controls or treatments, there’s often some level of risk that persists. This is expected, as it’s almost impossible to eliminate all risks entirely. Instead, the goal is often to reduce risk to an acceptable level, which is where the concept of residual risk comes into play.
In the Acme Bank Corp Scenario, considering our ongoing example of Acme Bank Corp and its CISO’s dilemma, let’s examine the “Unpatched software in ATM systems” risk. Post the initial risk assessment, a modern Machine Learning-based Antivirus (AV) solution was implemented. However, the residual risk was still beyond acceptable levels. This emphasizes that sometimes a single mitigation strategy isn’t enough, and risks may still loom large.
In response, the CISO introduced a Next-Generation Intrusion Prevention System (NGIPS), further shrinking the residual risk. Post this two-pronged approach, the residual risk reached a level that was deemed acceptable by the bank’s risk criteria.
But what is the best strategy to decide whether the residual risk is accepted or not?
The decision to accept a risk is multifaceted. It often involves evaluating the risk’s potential impact on the business, the feasibility and cost of mitigation, and the organization’s risk appetite. In Acme Bank Corp’s scenario, it was only after deploying two layers of defense that the risk became acceptable.
This iterative approach underscores an essential lesson as risk management isn’t a one-size-fits-all process. It requires careful deliberation, understanding of the threat landscape, and a willingness to re-evaluate decisions based on new data or changing circumstances. Risk acceptance is a strategic move, not a sign of negligence, and it has to be dynamic. It’s about understanding the landscape, evaluating the potential impacts, and making informed decisions.
Good Job!
Our CISO at Acme Bank Corp has effectively navigated this landscape, applying various risk treatment measures that have significantly reduced vulnerabilities. Through his strategic and proactive measures, he has updated the risk table to show the Before and After, reflecting the current state of risks. As a result, all previously identified risks have now been brought to an acceptable level, showcasing the CISO’s commitment to securing the organization and adeptly managing its risk environment.
ISO 27005: Risk Communication, Consultation, Monitoring, and Review
Risk Communication and Consultation is about ensuring that relevant stakeholders are informed about the risk management activities and decisions. It facilitates a shared understanding of risks, reasons for decisions taken, and the broader risk context. This continuous dialogue ensures that everyone involved is aligned, promoting informed decision-making and fostering a culture of transparency.
While achieving risk acceptance is a significant milestone, the cybersecurity landscape is continually evolving. Risk Monitoring and Review involves regularly scrutinizing and updating the risk profile to address any new threats, vulnerabilities, or changes in the organization’s operations. It’s crucial to maintain an updated view of risks, ensuring that the bank remains proactive in its defenses and that past efforts don’t become obsolete in the face of new challenges.
Quick Quiz
Summary
First and foremost, I want to thank you for accompanying us on this enlightening journey through risk management in cybersecurity, using the compelling backdrop of Acme Bank Corp. This hasn’t just been a lesson, it’s been a story of leadership, strategy, and tactical execution amidst a challenging cybersecurity landscape in any organization.
In our narrative, we envisioned ourselves alongside a newly appointed CISO, stepping into an environment filled with the echoes of past cybersecurity incidents. The stakes couldn’t have been higher. Acme Bank Corp, with its sprawling operations, was under the spotlight, with stakeholders, customers, and regulators demanding more robust cybersecurity measures.
However, our CISO was not deterred. With seasoned expertise and a clear vision, he immediately gauged the prevailing atmosphere, understood the roles and concerns of his team, and cultivated a direct line of communication with the C-Executive team. His objective was clear: not just to protect Acme Bank Corp, but to restore faith among its stakeholders by addressing cyber risk concerns comprehensively.
In the practical realm, our CISO commenced with a thorough Audit, a step that proved instrumental in understanding the organization’s assets and their respective vulnerabilities. This meticulous Inventory laid the groundwork for subsequent measures. Recognizing the importance of a structured approach, he elected the Risk Management Framework (RMF) of ISO 27005. Yet, he didn’t just adopt it blindly. He tailored and scoped the framework, ensuring it was fine-tuned to Acme’s unique challenges and culture.
One of the most significant stages was Risk Identification. Here, the CISO orchestrated the creation of a detailed table, enumerating each identified cyber risk. This table wasn’t just an internal document, but it was a testament to transparency, shared with stakeholders to enhance collective understanding and responsibility.
Risk Analysis followed, diving deeper into each risk, unraveling their complexities, and measuring their potential impact on business operations. Our CISO wasn’t merely focused on technical ramifications; he stressed the importance of Business Impact Analysis (BIA), ensuring decisions were aligned with the bank’s operational and strategic imperatives.
The Risk Treatment phase was nothing short of a tactical masterclass. The CISO and his team, using their insights from the previous stages, devised targeted measures to mitigate each risk. The aim was not just mitigation but to bring each risk down to an acceptable level, in line with the bank’s risk appetite, tolerance, and threshold.
As we reflect on this story, let’s appreciate the multidimensional nature of cybersecurity risk management. Our journey, though set within the confines of Acme Bank Corp, holds lessons that resonate universally. Effective risk management is a dynamic process, requiring continuous communication, consultation, monitoring, and review.
Thank you again for investing your time and effort. We’ve tried to navigate the complex routes of ISO 27005, but remember, every organization has its own tale, its unique challenges. As we close this chapter, I hope you feel better equipped and inspired to pen your organization’s success story in cybersecurity risk management.
Your Homework
- Investigate a real-life cybersecurity breach in a financial institution within the past five years. Analyze the cause, the vulnerabilities exploited, and the aftermath. Suggest what risk management steps could have prevented it.
- Using a virtual environment, set up a basic network. Identify potential vulnerabilities and list them in a table format similar to the one in our lesson.
- Research the latest advancements in Intrusion Prevention Systems (IPS). How do they differ from traditional systems, and what added benefits do they offer?
- Explore the difference between Qualitative and Quantitative Risk Assessment in depth. Create a presentation showcasing your findings, complete with examples.
- Dive into Machine Learning-based Antivirus solutions. How do they function? And in what ways are they superior to traditional antivirus solutions?
If you learned something new today, help us to share it to reach others seeking knowledge.
If you have any queries or concerns, please drop them in the comment section below. We strive to respond promptly and address your questions.
Thank You









