Table of Contents

Imagine a scenario where an employee at a major corporation inadvertently shares their login information, potentially exposing sensitive data to malicious entities. As the digital landscape expands, the maze of usernames, passwords, and permissions becomes an ever more critical fortress. It’s the shield that guards an organization’s most valuable assets. But how is this fortress built? How do businesses ensure that the right person has the right access at the right time? This lesson dives deep into the world of Identity and Access Management (IAM). Prepare to journey through its layers, understanding its importance, principles, architecture, and the steps to implementing a successful IAM project. So, are you ready to master the craft of safeguarding digital identities? Let’s embark on this exploration together.
What is Identity and Access Management (IAM)?
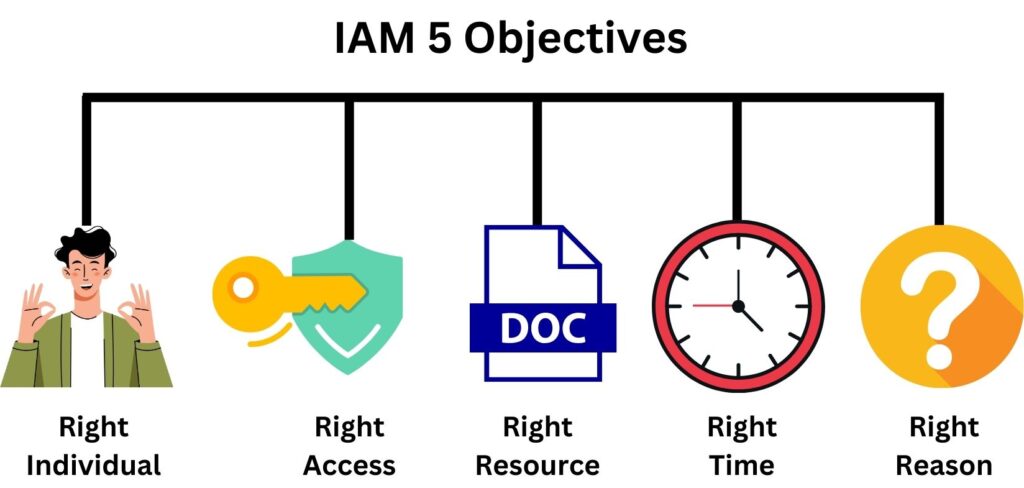
Have you wondered how organizations manage to keep their digital assets secure, especially when hundreds or thousands of employees access these resources daily? How do they ensure that only the right people access the right information at the right time for the right reason? The magic lies in a process known as Identity and Access Management, or IAM for short. Let’s today in this lesson explore deeper into what IAM is, its evolution, and its relevance even to everyday individuals.
At its core, IAM is a framework that allows businesses to manage electronic identities. Think of it as a digital passport system. Just as you’d need a passport to enter another country, with IAM, you need to verify your identity to access specific digital resources.
The name “Identity and Access Management” is quite descriptive. It tackles two critical aspects:
- Identity – Confirming that you are who you claim to be. It’s the unique representation of a user through attributes like username, email, or employee ID. This validation can be supplemented using credentials such as passwords, security tokens, or biometric data like fingerprints and facial recognition.
- Access – After establishing identity, the system determines what resources you’re permitted to interact with. This involves evaluating permissions based on roles, groups, or specific user privileges. Access ensures you can only reach data, applications, or tools that align with your responsibilities and purpose
So, it’s like a two-step dance: first proving your identity, and then receiving the appropriate access permissions.
Is IAM a Hardware or Software Solution?
IAM is primarily a software-based solution. While certain authentication methods (like smart cards or biometric scanners) involve hardware, the IAM system itself is software that integrates with various parts of an organization’s IT infrastructure.
IAM, as a term and concept, has been around since the early days of digital computing. However, as technology has evolved, so too have IAM systems. Before dedicated IAM systems came into play, organizations relied on manual processes and simpler authentication mechanisms, like basic passwords. As the digital landscape grew more complex, and security breaches became more costly, the need for a comprehensive solution like IAM became evident.
While IAM is a critical component for large enterprises, its principles are applicable even in our daily lives. Think about how you access your email, social media account, or online banking. Isn’t it essential that only you can access your personal data? That’s a form of IAM in action!
Imagine you’re studying in a global university with students from all over the world. This university has a large digital library. As a student, you’re granted access to this library. But should you be able to access the financial records of the university or the personal data of other students? Absolutely not! That’s where IAM framework ensures that while your identity as a student is acknowledged, you only access what’s relevant to you.
IAM’s principles affect us daily, ensuring our digital identities are protected and correctly utilized. As the digital world advances, understanding and appreciating the role of IAM becomes crucial, not just for IT professionals but for anyone navigating this interconnected world.
IAM vs IdM
Identity and Access Management (IAM) and Identity Management (IdM), while they might sound similar, each has distinct functionalities, histories, and purposes. Let’s uncover the differences and the evolution of these solutions.
Identity Management (IdM)
IdM focuses on managing individual identities within a system. It’s all about ensuring that the right individuals have the appropriate profiles set up within a network environment. This includes creating, modifying, and deleting user profiles and ensuring that each user profile corresponds to the individual it represents.
Identity and Access Management (IAM)
IAM, on the other hand, encompasses a broader range of functionalities. While it includes all the features of IdM, it goes a step further by adding the layer of “access.” This means, after managing identities, IAM ensures that these identities have the correct permissions to access specific resources. It merges two important elements as we defined previously (Identity and Access)
Historically, IdM solutions were the first to emerge. As computer systems began connecting more people and resources, there arose a need to manage individual identities, ensuring that John from Accounting wasn’t mistaken for John from HR.
However, as these systems grew in complexity, it became evident that managing identities wasn’t enough. It was equally crucial to manage what these identities could access and do. For instance, while both aforementioned Johns should be recognized individually, they shouldn’t have access to each other’s specialized tools or data. That’s when the broader IAM solutions came into play.
IdM can be thought of as a subset of IAM. As technology evolved and organizational needs became more intricate, simple identity management wasn’t sufficient. The necessity to integrate identity management with access controls led to the birth of IAM. Imagine a building where IdM provides badges to all employees to prove their identity. Now, should every employee be allowed to enter any room with their badge? Not quite. That’s where IAM steps in. It’s the sophisticated lock system that ensures employees can only enter rooms pertinent to their roles.

The shift from IdM to IAM is primarily driven by growing security concerns and the complexities of modern organizational infrastructures. With cyber threats looming large and companies hosting an array of applications and sensitive data, there was a dire need to not only identify users but also control their access to various resources. Hence, while IdM was the foundation, IAM became the fortified structure built upon it.
Principles of IAM
Identity and Access Management (IAM) is a cornerstone of modern cybersecurity, acting as the gatekeeper to an organization’s critical systems and information. But like any formidable fortress, its strength is derived from the foundational principles upon which it stands. These principles, each significant in its own right, collectively provide a roadmap for creating a resilient and effective IAM strategy. They guide organizations in ensuring that the right individuals have the right access at the right time, all while balancing security with usability. Moreover, these principles serve as a compass, helping businesses navigate the complexities of an ever-evolving digital landscape, rife with both opportunities and threats. As you read and explore deeper into each principle, you’ll discover the detailed fabric they weave, seamlessly integrating aspects like user lifecycle, access controls, monitoring, and more. These principles aren’t just theoretical constructs; they are actionable guidelines that, when implemented correctly, fortify an organization’s digital defenses and streamline its operations. Let us dive in to understand, embrace, and implement these foundational tenets of IAM.
Principle 1: Principle of Least Privilege (PoLP)
The Principle of Least Privilege (PoLP) dictates that users should be granted only the minimum permissions necessary to perform their tasks. This approach minimizes potential damage if an account is compromised, as malicious users or programs can’t access information or functionalities beyond the account’s permissions. Consider a bank teller; while they need access to view a client’s account balance, they don’t necessarily need the rights to modify the bank’s core software. By adhering to PoLP, organizations ensure that each individual or application only has the access it genuinely requires, thus offering security and reducing risks.
Principle 2: User Lifecycle Management (ULM)
User Lifecycle Management revolves around managing a user’s digital identity from its inception (onboarding) to its termination (offboarding). This encompasses the entire journey; from initial account creation, and modifications during role changes (like promotions), to eventual deactivation upon the user’s exit.
ULM includes the process of Provisioning and De-provisioning which we will describe later.
For instance, when an employee joins a company, they’re provided with specific system access. If they transition roles, their access might be adjusted. Upon leaving the company, their account is deactivated, ensuring they no longer have access. This continual management safeguards the organization, ensuring the right people have appropriate access at all times.
Think of ULM as the entire life story of a user within an organization, from birth to retirement.
Principle 3: Access Control

Access Control governs how permissions are assigned to users within a system. There are a lot of access control methods, a few examples like role-based (RBAC) where permissions are granted based on a user’s job function, and attribute-based (ABAC) where access is determined by user attributes, like department, location, or time of access. Imagine a hospital, where RBAC would give all nurses certain access rights, while ABAC might grant specific access to a nurse in cardiology during daytime hours only. Both methods ensure the right people access the right resources.
Principle 4: Multi-Factor Authentication (MFA)


Multi-Factor Authentication (MFA) is a security measure that requires users to provide multiple forms of identification before granting access. Instead of just relying on a single password, MFA might ask for something you know (password), something you have (a phone or smart card), and something you are (biometrics like fingerprints or facial recognition). Think of it as multiple layers of a security door; even if a thief knows the door code (password), they can’t enter without the unique key (smart card) and their specific fingerprint. By demanding multiple authentication steps, MFA significantly heightens security, making it considerably harder for unauthorized users to gain access, even if they’ve compromised one of the authentication factors.
Principle 5: Single Sign-On (SSO)
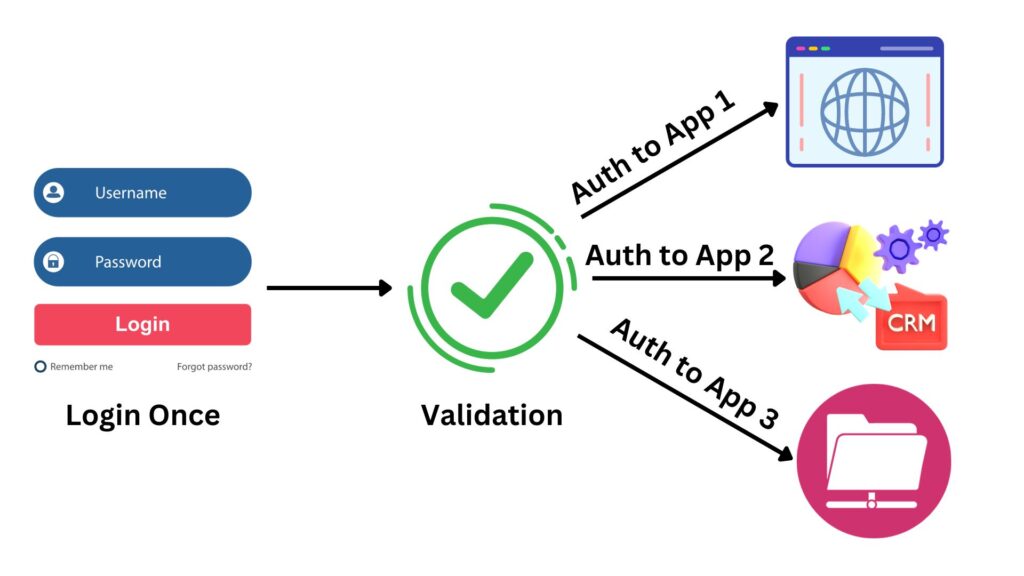
Single Sign-On (SSO) is a user authentication service that permits an individual to use one set of login credentials (like a username and password) to access multiple applications. The beauty of SSO is its convenience; instead of remembering numerous passwords for different services, a user only needs one. Picture it as a universal keycard for a large building. Instead of carrying a separate key for every room (each application), you have a single card (login credential) that grants you access to every room you’re authorized to enter. Not only does SSO streamline the user experience, but it also reduces password fatigue and minimizes the risks associated with managing multiple passwords, making both users and IT departments happier.
Principle 6: Provisioning and De-provisioning
Provisioning and de-provisioning are the yin and yang of the user access lifecycle in digital systems. Provisioning involves setting up and granting initial access permissions for a new user. When an employee starts at a company, provisioning ensures they receive access necessary to perform their role. Conversely, de-provisioning is the process of removing or limiting a user’s access when it’s no longer required, such as when an employee departs. Together, these processes maintain the integrity and security of an organization’s network environment, ensuring that only current, authorized individuals have access to the resources they genuinely need and reducing potential security vulnerabilities.
Note that Provisioning and de-provisioning are key events within User Lifecycle Management (ULM) which we explained previously.
Principle 7: Audit and Compliance

Audit and Compliance pertain to the evaluation and validation of an organization’s adherence to regulatory and internal standards, especially in the realm of IAM.
Audits ensure that only the correct individuals have appropriate access and that any deviations or violations are promptly identified.
Compliance, on the other hand, ensures that the organization aligns with industry regulations and standards, preventing potential legal and security pitfalls.
For instance, a company handling financial data might undergo an audit to verify that only authorized personnel can access sensitive information. If discrepancies are found, the company would need to rectify them to achieve compliance with financial data protection regulations.
Both Audit and Compliance processes safeguard the organization’s integrity, reputation, and data, while also ensuring they meet their legal and ethical obligations.
Principle 8: Federation
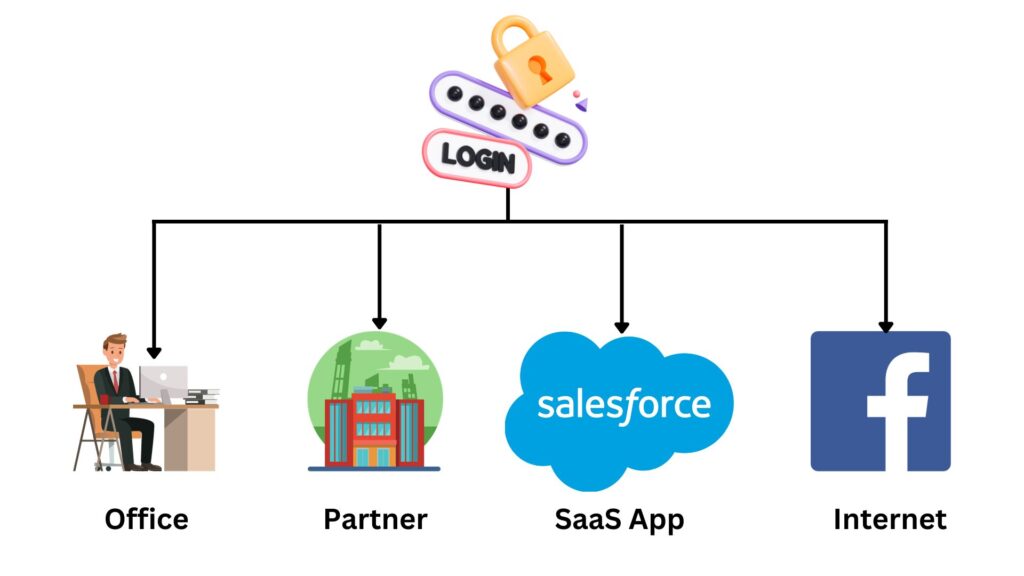
Federation refers to an arrangement where multiple organizations or services share and trust authentication credentials without exposing sensitive information to each other. It enables users to authenticate with one service and gain access to others without re-entering credentials. A classic example is using a Google account to sign into third-party applications. While Federation offers enhanced user convenience and reduces password fatigue, it’s not a one-size-fits-all solution.
Organizations must weigh the benefits against potential security concerns. For some businesses, particularly those collaborating across different domains or leveraging cloud services, Federation is invaluable. For others, especially those with very stringent security requirements or those not using multiple interconnected applications, it might not be a priority. Ultimately, its implementation depends on the organization’s needs and risk appetite.
Principle 9: Identity Propagation
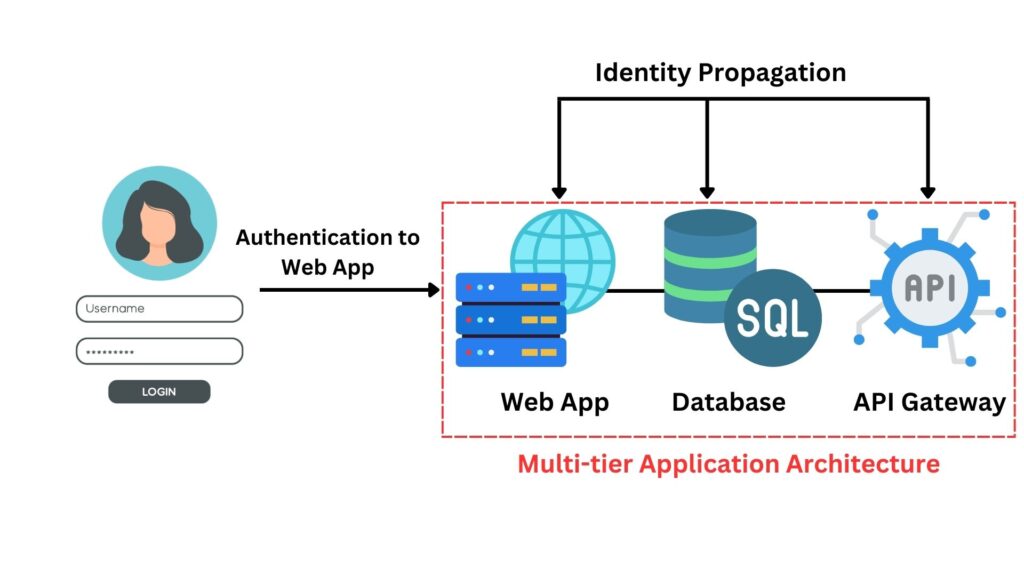
Identity Propagation refers to the forwarding or transfer of a user’s identity across multiple layers or components of a system. In complex network architectures, a user’s authentication might need to be communicated across various subsystems or services.
For instance, in an e-commerce platform, when a user logs into the frontend website, Identity Propagation ensures their authentication travels to the inventory system, payment gateway, and order tracking service. This allows seamless user experiences and secure transactions and status checks without the user re-authenticating for each subsystem.
How Identity Propagation is different from SSO?
Identity Propagation and SSO both deal with managing user identities, but in different contexts.
SSO lets users access multiple applications with a single set of credentials.
Identity Propagation, on the other hand, forwards a user’s identity across different system components, ensuring consistent identity recognition within a single application’s layered architecture.
Essentially, SSO focuses on multiple applications, while Identity Propagation emphasizes depth within a single application.
Principle 10: Password Policies


Password Policies are sets of rules established to enhance security by guiding users in creating strong, effective passwords and managing them responsibly. These policies often dictate minimum password lengths, require a mix of character types (uppercase, lowercase, numbers, and symbols), mandate regular password changes, and set rules against password reuse.
For instance, a policy might require a 12-character password with at least one uppercase letter, one number, and one symbol, changed every 90 days without recycling the last five passwords. Additionally, policies might include account lockouts after a number of failed login attempts, reducing the risk of brute-force attacks.
By setting and enforcing robust password policies, organizations drastically reduce vulnerabilities associated with weak or compromised passwords, ensuring a sturdier frontline defense against unauthorized access.
Important Note: even if you used a 50-character password, relying solely on it is risky. Strong passwords improve security, but they're not infallible. Multi-Factor Authentication (MFA) adds an additional layer of protection, ensuring that even if a password is compromised, unauthorized access remains challenging. Always pair strong passwords with MFA for optimal security. Research and studies show that MFA prevents 99.9% of automated identity compromise attempts.Principle 11: Self-Service Capabilities
In the realm of Identity and Access Management, Self-Service Capabilities empower users to manage certain aspects of their digital identity autonomously, without always relying on IT support. This includes tasks like resetting forgotten passwords, updating personal details, or even requesting access to specific resources. For instance, an employee might use a self-service portal to reset their password at 2 a.m., without waiting for IT’s working hours. Not only does this enhance user experience by offering immediate resolutions, but it also alleviates the burden on IT teams, freeing them from handling routine requests. As organizations grow, these capabilities become invaluable, ensuring scalability and operational efficiency while preserving security and compliance standards.
Principle 12: Segregation of Duties (SoD)
Segregation of Duties (SoD) is a fundamental principle in both IAM and broader organizational processes. At its core, SoD aims to prevent any single individual from having control over all aspects of any critical transaction to minimize risks of mistakes, misuse, or fraud. By dividing responsibilities among various personnel, SoD ensures that no single person has enough authority or access to exploit the system for malicious or erroneous purposes.
Imagine a procurement process within a company. One employee may have the authority to request a purchase, but they shouldn’t have the ability to both approve the purchase and process the payment. If the same person could execute all these steps, the door would be open for potential fraud or mistakes. Instead, by segregating these duties, a checks-and-balances system is created, where multiple individuals oversee the process, and each step is subject to scrutiny.
In the computer network, SoD becomes particularly crucial in IAM, ensuring that, for instance, the person who writes a piece of software isn’t the same person who reviews, approves, and deploys it. This approach not only deters insider threats and fraud but also helps in identifying genuine mistakes, ultimately upholding the integrity and security of an organization’s operations.
Principle 13: Centralized Management
Centralized Management in the context of IAM refers to consolidating the oversight and control of user identities, permissions, and security protocols under one unified system or platform. Instead of scattered, siloed systems each having their own user databases and access controls, everything is streamlined under a single, central hub. For example, an organization using multiple software solutions might integrate them into one centralized IAM platform, allowing uniform identity verification and access controls across all applications.
The advantages are manifold; it simplifies administration, ensures consistent policy enforcement, and offers a holistic view of user activities and security events. This unified approach not only enhances security by eliminating inconsistent or overlapping permissions but also improves operational efficiency. Admins can make swift, informed decisions, and users experience smoother, more consistent access processes across the board.
Principle 14: Logging and Monitoring

Logging and Monitoring are twin pillars in the IAM domain, ensuring that user activities and system operations are both recorded and actively observed.
Logging captures a digital “paper trail” of events, like who accessed what resource, when, and from where. This isn’t just about tracking; it’s about accountability. Should a breach or anomaly occur, logs serve as an invaluable resource for forensic analysis.
Monitoring, on the other hand, is the real-time surveillance of these logs and system activities. It’s the vigilant eye seeking patterns, anomalies, or suspicious activities. For instance, if a user who typically accesses the system from New York suddenly tries to log in from a remote location in another country, monitoring tools can flag this for investigation.
Together, logging and monitoring strengthen security by creating both a record for post-event analysis and a proactive defense mechanism against potential threats.
Principle 15: Integration with External Systems

In today’s interconnected networks, the ability of an IAM solution to integrate seamlessly with external systems is very important. As organizations adopt more software tools, applications, and platforms, ensuring that identity and access management capabilities extend across these disparate systems is essential for both operational efficiency and security.
Integration with external systems means that the IAM solution can communicate, share data, and enforce access controls uniformly, whether it’s with cloud services, on-premises applications, third-party platforms, or even IoT devices. Consider an enterprise that uses cloud storage, an on-site Customer Relationship Management (CRM), and a third-party payroll system. Integration ensures that employees have appropriate, consistent access across all these platforms based on their roles, without the need for separate authentication processes for each.
Such integration also offers other benefits:
- Unified User Experience – Users encounter a consistent access and authentication process across tools.
- Operational Efficiency – Admins manage permissions from a centralized point, even if the underlying systems are diverse.
- Enhanced Security – Consistent policies and real-time data sharing can help in promptly detecting and responding to security threats.
Ultimately, as businesses continue to diversify their tech stack, the ability of IAM solutions to integrate broadly becomes not just advantageous but a necessity.
Principle 16: Scalability

Scalability in IAM ensures that as an organization grows in size and complexity, its identity and access management system can adapt and expand seamlessly. Whether it’s onboarding hundreds of new employees, integrating additional applications, or expanding into global markets, a scalable IAM solution can handle increased demands without performance drops or security lapses. Essentially, it’s about future-proofing IAM operations, ensuring consistent performance regardless of organizational evolution or growth.
Principle 17: Automation
In IAM, automation simplifies complex tasks and reduces manual intervention, which not only slows down the process but also introduces potential errors. By automating routine and repetitive processes like user onboarding, role assignments, and access provisioning, IAM systems can quickly respond to changes, reduce human errors, and enhance security. Automation not only ensures efficiency but also allows IT teams to focus on more strategic tasks, thereby optimizing resources and strengthening an organization’s overall security posture.
Imagine a new employee, joining a company. With IAM automation, as soon as his details are entered into the HR system, they’re granted default access rights, an email account is set up, and essential software licenses are activated, all without manual intervention.
Principle 18: Just-In-Time (JIT) Access

Just-In-Time (JIT) provisioning in IAM refers to creating or allocating resources as and when they’re needed, rather than in advance. This dynamic approach reduces unnecessary access rights, minimizes potential security vulnerabilities, and optimizes resource usage. JIT ensures users have access only when required, such as when they join a specific project or role, and the access is revoked once it’s no longer necessary. This methodology embraces a proactive security stance, providing the needed flexibility while maintaining airtight controls.
Consider a developer. Using JIT, when he temporarily joins a high-security project, he’s granted specific access rights just before he starts. Once he finishes his task, his elevated access expires, reverting him to his standard permissions, ensuring minimal exposure to potential threats.
In a JIT approach, provisioning can be either manually approved or automatically granted based on predefined criteria. Manual approval often involves managers or IT administrators giving the green light after receiving an access request. In contrast, automated processes use algorithms or workflows to decide, minimizing delay but still adhering to security protocols.
Just-In-Time and the Principle of Least Privilege together forge an advanced shield for information security. JIT ensures that access rights are granted only when truly necessary and for the minimum time required. Combine this with PoLP, which guarantees users only get the bare minimum privileges they need, and the result is a dynamic, adaptable system. For instance, if an employee requires elevated rights for a specific task, JIT provides that access promptly. PoLP ensures the rights are limited to just that task. Once completed, those rights evaporate, leaving no unnecessary access avenues open. This synergy narrows the window of potential exploitation, championing a proactive, minimal-risk environment.
Quick Quiz
The Architecture of IAM Solution
Once you get into the IAM world, you will quickly realize the breadth and depth of the concept. It’s an expansive field, with numerous components and modules working in tandem to deliver its promises. While we’re about to explore into essential architectural components of IAM, remember that this is not an exhaustive list. IAM’s vastness means that there are other components and parts beyond what we cover in this lesson.
Moreover, as we discussed the principles of IAM earlier, it’s essential to appreciate that behind each principle, there’s likely a system or component operationalizing it. As you read on, think of these principles and the technological gears turning behind the scenes to make them a reality.
The following diagram provides a high-level overview of the IAM architecture, capturing its essential components and interactions:
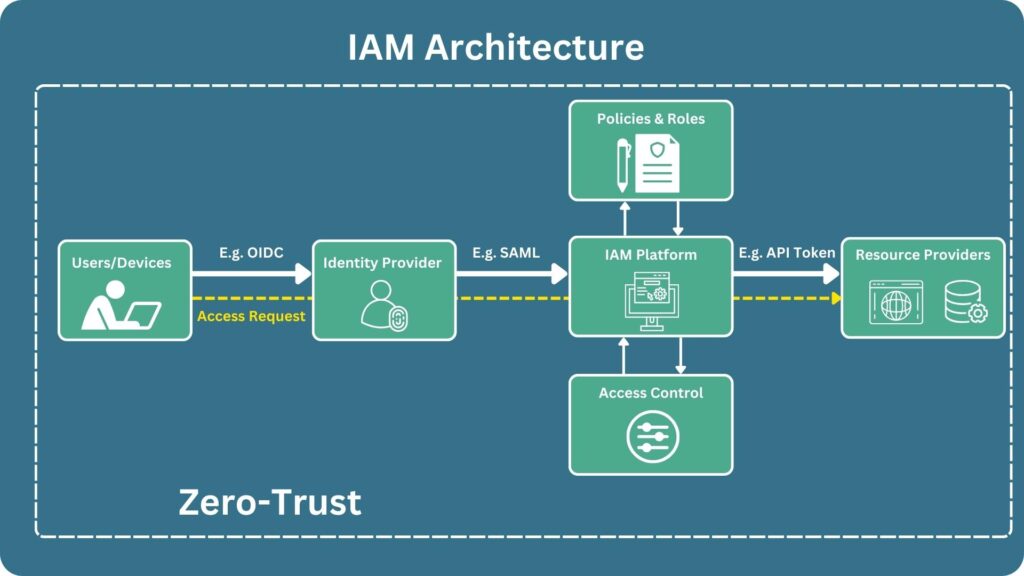
Component 1: Identity Repository
An Identity Repository is a database or datastore that holds user profiles, including attributes such as usernames, passwords, roles, and other related information. It’s the foundational “source of truth” for user identities in an organization. IAM systems frequently refer to this repository to authenticate users, determine their roles, and enforce appropriate access controls. By maintaining an organized and updated repository, organizations ensure that access decisions are based on current and accurate user data. In many instances, this repository may integrate with other systems or directories, such as LDAP or Active Directory, to centralize identity information.
Integrity in the Identity Repository is fundamental for ensuring accurate authentication and authorization decisions. A compromised repository can lead to unauthorized access. To safeguard integrity, measures include encryption of stored data, hashing of passwords, regular data validation checks, and using digital signatures or checksums to detect tampering. Implementing robust access controls and periodic backups further fortifies repository trustworthiness.
Microsoft’s Active Directory (AD) is a prevalent example of an Identity Repository used by enterprises today. It centralizes user data, streamlining authentication and authorization processes across various organizational resources and applications.
Component 2: AAA Service
The AAA Service, standing for Authentication, Authorization, and Accounting, forms a triad of crucial functions in IAM.
- Authentication is the act of confirming an entity’s identity, typically a user, based on valid credentials like passwords or biometric data.
- Once authenticated, Authorization takes over, stipulating what resources the user can access and the actions they’re allowed to perform, often guided by user roles or policies.
- Accounting, sometimes overlooked but equally vital, is about tracking and logging user activities. This not only helps in resource management (like bandwidth or time allocations) but also becomes crucial for audits, ensuring compliance, and investigating security incidents.
By encompassing these three areas, AAA Service provides a comprehensive approach to manage identities and their associated activities, ensuring both security and operational efficiency within an organization’s network and systems.
Component 3: Policy Lifecycle and Enforcement
This part orchestrates access decisions in IAM, encompassing a quartet of sub-components; PAP, PIP, PDP, and PEP that collaboratively manage, decide, and enforce access controls. Each plays a distinct role in ensuring optimal security practices.
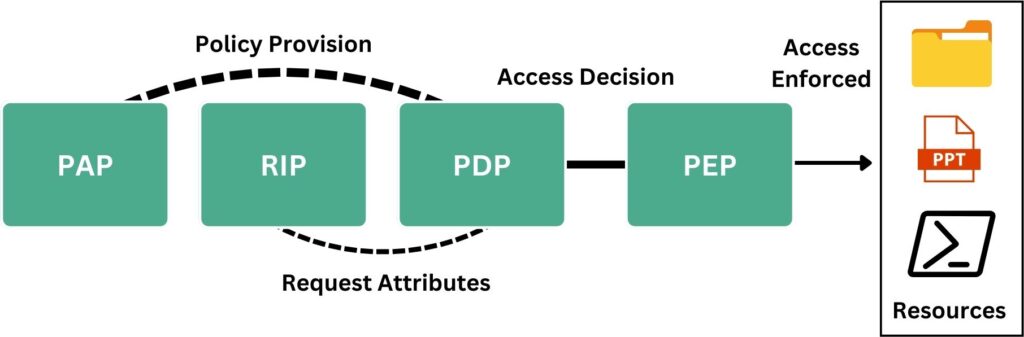
- Policy Administration Point (PAP) is a list of rules set by the administrator that the PDP later evaluates. PAP defines and manages access control policies. It is the mastermind where these complex rules are birthed and refined. Think of it as the drafting table where architects (or administrators) design the blueprint. This is why it has to come first, as without a clear set of policies, subsequent stages would have no base to operate upon.
- Policy Information Point (PIP) is responsible for providing additional contextual information about the identity to make informed decisions. Now, imagine a scenario where a user attempts to access a resource. The system needs to understand the context fully, who is the user? What’s their role? Do they have any specific attributes or conditions that should be considered? PIP is the detective in this story, pulling together all necessary pieces of information from various sources to paint a comprehensive picture before any enforcement action is considered.
- Policy Decision Point (PDP) is the heart of this lifecycle process in access control. When a user attempts to access a resource, the PDP evaluates the user’s attributes against a set of policies to determine if access should be granted. It doesn’t enforce the decision but merely makes it. With a clear set of policies from PAP and the context from PIP, we move to the courtroom drama. The PDP is the judge, weighing the evidence (user attributes and context) against the law (policies). It deliberates and reaches a verdict; should access be granted or denied? This step is crucial. Without the prior groundwork of PAP and PIP, the PDP would either operate in a vacuum or make uninformed decisions, neither of which is desirable in a security setting.
- Policy Enforcement Point (PEP) is the final act in our play; the enforcer. After the PDP’s judgment, the PEP acts as the bailiff, ensuring the judgment is carried out to the letter. If access is granted, the doors open; if it’s denied, they remain firmly shut. The enforcement has to be the concluding step to ensure that the decided action (based on policies and context) is executed in the real world.
Component 4: Application Programming Interface (API)
In IAM, APIs act as the bridges that allow different software solutions to communicate with each other. They define the methods and data formats that applications can use to request and exchange information. APIs are crucial in IAM because they enable the integration of various services and components, making it possible to manage identities and enforce policies across a diverse technological landscape.
For instance, an IAM solution might leverage APIs to integrate with an organization’s HR system, ensuring that when an employee’s role changes, their access permissions are automatically updated across all systems. Or, when a user attempts to login, an API might be used to fetch their authentication details from an identity repository. Essentially, APIs provide the flexibility and extensibility for IAM solutions to work in complex, multi-platform environments. They ensure that identity and access management processes are consistent, seamless, and efficient across the board.
Component 5: Directory Service
Directory Services act as the central address books, maintaining detailed information about users, their roles, attributes, and other pertinent data. Think of them as sophisticated phonebooks, but instead of just names and numbers, they offer a wealth of structured data about users and resources in an organization.
Directory Services not only store this information but also facilitate quick and efficient lookups. For example, when a system needs to authenticate a user, it might query the Directory Service to verify the user’s credentials. Or, when assigning access rights, the Directory Service can provide details about a user’s role, group memberships, or other attributes.
One of the most commonly recognized Directory Services is Microsoft’s Active Directory (AD). It’s used in numerous enterprises to manage user accounts, roles, and access rights, and to enforce policy configurations.
These services are indispensable for IAM because they centralize user and resource data, ensuring consistency and accuracy across systems. By having a single source of truth, organizations can streamline access management processes, avoid redundancies, and improve overall security.
Directory Service vs Identity Repository
While both are involved in storing user information, an Identity Repository primarily focuses on raw data storage of credentials and attributes. In contrast, a Directory Service, like Microsoft's Active Directory or OpenLDAP, offers organized, hierarchical access to this data, optimized for rapid retrieval and management. Think of the repository as the back-end database, and the directory service as the structured, user-friendly phonebook. In some systems, they might overlap or be tightly integrated, but their core purposes differ; simple storage vs. structured access.Component 6: Dashboard
A dashboard provides administrators and security professionals with a centralized visual interface to oversee, manage, and analyze user access and activities across various systems. By aggregating data from multiple sources, an IAM dashboard can display real-time metrics, alerts, and detailed reports, facilitating quicker decision-making and proactive management. Whether it’s tracking unauthorized access attempts, monitoring user activity patterns, or ensuring compliance with organizational policies, a well-designed dashboard becomes an invaluable tool for effective IAM management.
Component 7: Self-Service Portal
This portal empowers users by allowing them to perform certain IAM-related tasks on their own, without the need to contact IT or administrative support. Common functionalities include password resets, access requests, updating personal details, and viewing access logs. A Self-Service Portal not only enhances user experience but also reinforces security by minimizing the time windows where access issues might be exploited.
Component 8: Notification Service
This service is responsible for sending alerts and notifications to users, administrators, and other stakeholders based on specific IAM-related events. For instance, when there’s an unusual access attempt, a user’s role changes, or when a password is about to expire, notifications are dispatched. These alerts can be in the form of emails, SMS, or even system pop-ups. A robust Notification Service enhances security by ensuring timely awareness of critical events, accelerates compliance, and provides better communication and prompt action within the IAM environment.
Component 9: Identity Bridge
Identity Bridge is an essential component in the IAM architecture, especially in hybrid environments. An Identity Bridge acts as a connector or liaison between on-premises identity systems (like Microsoft Active Directory) and cloud-based services or applications. This bridge ensures that identity data and access policies are consistently applied and synchronized across both local and cloud environments. By using an Identity Bridge, organizations can maintain a unified identity management approach even as they transition to or incorporate cloud-based resources, ensuring seamless user experiences and consistent security policies regardless of where the application or data resides.
Component 10: Token Transformation
Tokens are digital representations of a set of claims or assertions (statement of identity that verifies user attributes) about a user. Think of them as an electronic ID card, just as your ID card has your photo, name, and other attributes, a token contains information about a user, digitally signed for authenticity. In Identity Management, tokens play a vital role by providing a way to prove one’s identity electronically, without continuously sending sensitive credentials, like passwords.
For instance, when you log into a social media platform, instead of constantly verifying your username and password every time you access a feature, the system generates a token after your initial login. This token, which vouches for your identity, is presented as you navigate, ensuring a smooth experience. In more complex environments, like accessing a cloud application from a corporate network, tokens can also include details about your permissions or role, ensuring you only access what you’re allowed to. Tokens help strike a balance between user convenience and robust security in digital realms.
Token Transformation is implemented in the IAM domain especially when integrating disparate systems or platforms. Token Transformation is the process of converting an identity token or credential format from one type to another to ensure compatibility between different systems or applications.
For instance, a user might authenticate against one system that issues a Security Assertion Markup Language (SAML) assertion, but the target application might require a JSON Web Token (JWT). The token transformation service steps in to convert the SAML token into a JWT, ensuring seamless and secure access. It plays a crucial role in federated identity scenarios and cross-domain authentications, bridging the gap between varying identity token standards.
Component 11: Identity Provider (IdP)
An Identity Provider (IdP) is an entity within the Identity and Access Management (IAM) system that authenticates users and issues identity assertions or tokens. In simple terms, it confirms that “you are who you say you are” and then provides proof of this assertion in a format that other systems can understand and trust.
In today’s large and complex enterprise network, a single user often needs access to multiple applications, perhaps spread across different domains or platforms. Re-entering credentials for each application is cumbersome and raises security concerns. An IdP streamlines this by authenticating a user once and then providing tokens or assertions, enabling Single Sign-On (SSO) across multiple applications. This not only enhances user experience but also centralizes authentication mechanisms, making it easier to manage and more secure.
Let us have an example, imagine you’re an employee at a large corporation, “GlobalTech.” Every morning, you need to access your email, the company’s internal portal, a CRM system, and a cloud storage platform. Without an IdP, you’d be entering your username and password four times, for each system, every day. But with GlobalTech’s IdP, you log in once in the morning, and then seamlessly access all these systems without re-authenticating, all because these applications trust the assertions provided by the IdP.
IdP primary functions include:
- User Authentication
- Token or Assertion Issuance
- Single Sign-On (SSO) Enablement
- Multi-Factor Authentication (MFA) Support
- Identity Federation
- Profile Management
- Session Management
- User Lifecycle Management
- Attribute Management
- Integration with Directory Services and Identity Repositories
- Logging and Audit Trail Creation
- Account Recovery and Self-Service Functions
- Consent and Privacy Management
- Policy Enforcement
- Identity Delegation and Brokering
IdP, Directory Service, and Identity Repository? Are You Confused?
The potential confusion among these three crucial IAM components – IdP, Directory Service, and Identity Repository can be likened to the relationship between a librarian, a library’s card catalog, and the library’s database of member information. Let us simplify it with the following analogy:
- Directory Service (The Library’s Card Catalog)
This is similar to the card catalog at a library, where you can quickly look up books by their title, author, genre, etc. Similarly, a directory service, like Microsoft Active Directory (AD), is optimized for reading and searching, storing information such as usernames, roles, and other attributes. It tells the system where to find specific details but doesn’t authenticate the user.

- Identity Repository (The Library’s Database of Member Information)
If the Directory Service is the card catalog, the Identity Repository is the library’s database of members. It’s where all detailed member information, such as borrowing history, fines, and personal data, is stored. In the IAM world, this repository holds comprehensive identity data and, depending on its design, might even manage credentials.

- Identity Provider (IdP) (The Librarian)
The IdP acts like our librarian. When you approach the counter to borrow a book, the librarian verifies your identity (maybe checks your library card and photo ID). Once authenticated, they use the card catalog to locate your record and ensure you’re in good standing. Here, the IdP does the same; it authenticates users by checking credentials against the Identity Repository or Directory Service and then provides tokens or assertions to other systems, vouching for the user’s identity.

Component 12: Communication Protocols
The following protocols establish standardized methods for secure interactions and data sharing between systems. These protocols do not only support security but also streamline user experiences, ensuring consistent, efficient, and safeguarded access.
These protocols are essential to understanding the details of a comprehensive IAM framework:
- Security Assertion Markup Language (SAML)
SAML is an XML-based protocol specifically designed for exchanging authentication and authorization data. Its core strength lies in enabling single sign-on (SSO) for web-based applications, simplifying user experience in the IAM world of web-based application access. Imagine the cumbersome scenario where users have to remember multiple credentials for a variety of apps. This would undoubtedly lead to an upsurge in support tickets and potential security vulnerabilities. A real-world application of SAML can be visualized in the corporate landscape where workers access several cloud tools like a CRM, a marketing dashboard, and an HR system. With SAML, a single login grants seamless access to all these tools, eliminating the need for multiple logins.
- OAuth 2.0
At its essence, OAuth 2.0 is a protocol that allows third-party applications to have limited access to user resources, ensuring that user credentials remain uncompromised. Its main utility is in the realm of delegated authorization, particularly for cloud services and APIs. The challenge here is significant; without the safety net of OAuth, sharing user data between platforms and applications would be a hazardous endeavor, as apps might demand full user credentials for access. Consider a fitness app that wants to retrieve data from your hospital health statistics profile. Instead of needing your direct login, OAuth ensures that the app only fetches specific data, keeping your credentials safe (assume that both the Fitness App and Hospital App support OAuth protocol).
- OpenID Connect (OIDC)
OIDC is more than just a protocol; it’s an identity layer atop OAuth 2.0, with a laser focus on user authentication. This protocol plays a significant role in user authentication across a diverse array of platforms. Without OIDC, users might encounter inconsistent authentication due to fragmented development. This can lead to heightened security risks from varied access methods, password reuse, and potential vulnerabilities in individual app securities. A practical manifestation of OIDC is seen when users log into an e-commerce site using their Google account credentials, all the while ensuring that the user’s identity is kept intact and secure.
- System for Cross-domain Identity Management(SCIM)
SCIM stands as a beacon for automating the exchange of crucial user identity information. The protocol’s significance is in the sphere of user provisioning, ensuring smooth synchronization across a range of platforms. Not considering SCIM, the heavy responsibility would fall on IT teams to manually synchronize and manage user identities, a process fraught with potential errors. Picture this; upon joining a company, an employee’s details are entered into the HR system. With the magic of SCIM, these details can be automatically integrated into other systems such as email or access portals, eliminating manual data entry.
- Lightweight Directory Access Protocol (LDAP)
LDAP is like a digital phone book for networks. It helps organizations keep track of users, computers, and other resources, making it easier to manage and locate them. Instead of using pages like in a phone book, LDAP uses directories which are structured hierarchically. It’s often used in big companies for things like email systems or user logins to ensure the right people have access to the right resources. Think of it as a centralized way to store and fetch information about networked items and people.
- Remote Authentication Dial-In User Service (RADIUS)
RADIUS is like a gatekeeper for networks. It checks if users trying to connect (often remotely) are who they say they are and then decides what they’re allowed to do once they’re in. When someone tries to log in, RADIUS asks for a username and password. It then checks these against its records or asks another system if they’re right. If the credentials are correct, RADIUS sets up the connection, often deciding things like how long you can stay on, what network features you can use, and monitoring your activity. It’s widely used by Internet Service Providers (ISPs) and companies to manage access to Wi-Fi, VPNs, and other networked services. Think of RADIUS as a bouncer at the door, ensuring only authorized guests get in and enjoy the party safely.
- Kerberos
Kerberos is a network authentication protocol that uses secret-key cryptography to provide strong authentication for client-server applications. After you log in, Kerberos vouches for you to various services (like email or file storage) using encrypted tickets. This way, you don’t need to re-enter your password for each service. It’s designed to ensure that both the user and the service are genuine, making things more secure.
IAM Case Study
Acme Corp, a leading international manufacturer and distributor of medical equipment, has solidified its standing in the healthcare sector, boasting 10,000 employees across 200 branches in 120 countries. Their extensive reach demands a sophisticated technical infrastructure, blending on-premise and cloud-based solutions and incorporating OT environments like ICS and SCADA for real-time production factory oversight.
Over decades, through diligent research, significant investment, and hands-on implementation experience, Acme Corp has shaped and tailored its Identity and Access Management (IAM) requirements by adopting principles and customizations for every case and scenario. Acme has seamlessly integrated a fortified user experience for its extensive global workforce.
Robert James, a senior marketing executive at Acme Corp. Robert is the epitome of today’s global employee. His role is multifaceted; on a daily basis, Robert:
- Accesses the centralized database to fetch sales and distribution data, necessitating the Principle of Least Privilege.
- Uses integrated social media platforms like Facebook and Instagram for campaigns, made seamless through Single Sign-On.
- Collaborates with international teams via shared cloud storage and project management tools, requiring effective User Lifecycle Management and Access Control mechanisms.
- Logs into the partner portal to co-ordinate on joint marketing strategies, which is facilitated by robust Federation principles.
One day, Robert planned a new marketing strategy involving a collaboration with a renowned medical influencer. For this, he needed access to additional platforms and data analytics tools. Utilizing Acme’s Self-Service Capabilities, he swiftly requested access. Given the sensitivity of some tools, Robert was prompted for Multi-Factor Authentication, ensuring an added layer of security.
Once his need was identified, the Just-In-Time (JIT) provisioning ensured Robert got access for a specific timeframe. Concurrently, the Automation principle meant that all of Robert’s permissions were set up without manual intervention. The centralized management system kept track of these changes, ensuring Robert’s access level adhered to the segregation of duties which means that he couldn’t both initiate a promotional campaign and approve its budget himself.
During the campaign, Robert collaborated with external agencies, sharing patient usage statistics and feedback to tailor marketing strategies and improve product functionality. Acme’s IAM employed federated authentication, using SAML assertions, to vouch for Robert’s identity on partner platforms, ensuring secure, traceable access without additional logins. Identity Propagation is configured to seamlessly extend Robert’s authenticated identity to partner platforms, ensuring clear access boundaries and granting him appropriate data-sharing privileges without security lapses. Moreover, the password management policy prompted Robert to periodically change his password to keep his access secure, with periodic auditing to compliance checks against international standards, making sure there is no flaw or chance of breaches.
However, halfway through the campaign, Robert identified a potential integration requirement with an external data visualization tool for detailed analytics on campaign reach and engagement. Thanks to Acme’s IAM API capabilities, the integration with external systems was implemented with API connectors making this a hassle-free experience. The IAM system transformed tokens to match the external tool’s expected format, using a predefined API integration protocol (OAuth 2.0), ensuring seamless authentication and data exchange between the disparate systems without exposing user credentials directly. Robert’s team could scale up their operations, signifying the importance of scalability in urgent business scenarios.
At the campaign’s conclusion, Robert had to provide metrics to the top management. He accessed historical data, analytics tools, and social media metrics. Each step was recorded meticulously with the help of Acme’s IAM logging and monitoring features.
Post-campaign, Robert’s special access was automatically revoked, emphasizing the de-provisioning process that Acme policy considers. Reflecting on the campaign’s success, Robert realized the unsung hero was Acme’s comprehensive IAM system. Not only did it facilitate his multifaceted role, but it also ensured that all operations were secure, efficient, and compliant.
The intent behind illustrating Acme Corp’s journey was to showcase the complex design of the IAM system implementing these principles in action within a large and dynamic organization. Robert James’ experiences provide a microcosm of how foundational IAM elements intertwine, ensuring efficient and secure operations. Each principle, while significant on its own, achieves its true potential when harmoniously integrated with others. It’s similar to a symphony where each instrument contributes to a collective melody. Through this case study, we hope to emphasize that a holistic approach to IAM, rooted in robust principles, can elevate both user experience and organizational security to unparalleled heights.
IAM and Zero-Trust
Zero-Trust is a security concept (model) centered on the belief that organizations should not automatically trust anything, whether inside or outside its perimeters, but rather verify everything trying to connect to its systems before granting access. The essence of Zero-Trust is “Never Trust, Always Verify.”
This model is deeply intertwined with the identity world. In traditional network security, once a user’s identity was verified and they were inside the organization’s network, they were generally trusted to access various resources. However, as cyber threats evolved, this approach became inadequate. With Zero-Trust, the identity of every user and device is continuously validated before granting access to resources, ensuring that compromised credentials alone cannot provide access.
Enterprises that Ignore Zero-Trust adoption in their business network in today’s landscape can have grave consequences. As cyber threats grow more sophisticated, relying on perimeter-based security can lead to significant breaches. For example, a malicious actor with stolen credentials could traditionally move laterally across a network undetected. But with a Zero-Trust model, even after entering the network, they’d face consistent checks, preventing unauthorized access to critical data.
Thus, while Zero-Trust isn’t mandatory, it represents a forward-thinking approach to cybersecurity that aligns with the evolving threat landscape. Implementing it significantly boosts an organization’s security posture.
IAM for Zero-Trust or Zero-Trust for IAM?
When discussing the implementation of the Zero-Trust model and the IAM framework, a perplexing dilemma often arises; should we incorporate the Zero-Trust model into our IAM framework, or should we leverage the IAM framework to embrace the Zero-Trust model? This debate echoes the classic chicken-and-egg conundrum. Which foundational principle should organizations prioritize or begin with?
At its core, Identity and Access Management (IAM) is about ensuring the right individuals have the right access to the right resources at the right time for the right reasons. Zero-Trust, on the other hand, operates on the premise that no entity (user or system) should be implicitly trusted, regardless of its location relative to the organization’s perimeter.
So, how do they fit together?
Think of Zero-Trust as a guiding philosophy and IAM as one of the primary tools to realize that philosophy. The Zero-Trust model demands continuous verification of identity and strict enforcement of access controls. IAM provides the mechanisms to execute these demands. In this perspective, implementing Zero-Trust in an organization would involve leveraging IAM (among other tools and practices) to provide consistent identity verification and stringent access controls.
On the flip side, modern IAM frameworks often incorporate Zero-Trust principles inherently. As organizations implement IAM, they naturally move towards a Zero-Trust posture. After all, central to both IAM and Zero-Trust is the concept of ensuring only validated identities get the appropriate level of access.
Consider the following two examples:
- Zero-Trust within IAM Operations
At Globex Corp, when an administrator logged in to the IAM management console, while he was working, his computer got infected with malware. Despite being an administrator and having valid credentials, the Zero-Trust model integrated within IAM processes detected this attack in real-time. Immediately, the administrator was isolated from the network, and a secondary notification was sent to another administrator to investigate the issue, ensuring that potential threats were mitigated swiftly.
- IAM Framework Adopting Zero-Trust
At Globex Corp, the Zero-Trust model continuously ingests data feeds from the IAM platform, along with other security sources. When a sales executive accessed a sensitive financial application from an unusual location, the Zero-Trust system correlated this information with the IAM platform’s identity posture metrics. Recognizing potential risks, it instantly enforced multi-factor authentication, alerted the security team, and triggered other protective actions across various security products in real-time, ensuring an all-encompassing, layered security approach.
In conclusion, it’s not so much a debate of precedence but one of symbiotic coexistence. Implementing Zero-Trust involves adopting robust IAM practices, and a comprehensive IAM framework naturally inclines an organization toward a Zero-Trust posture. They complement and reinforce each other. Rather than viewing it as a chicken-and-egg scenario, consider them two sides of the same coin, both vital in the pursuit of a secure digital environment.
Project IAM
Remember, an IAM system is not just about technology. It involves people, processes, and technology working in harmony to provide secure and efficient access to systems and data. Proper planning, stakeholder involvement, and ongoing review are key to a successful IAM project.
I want you to imagine that you’ve been recruited as the Solution Architect for Acme Oil and Gas Corporation, tasked with the massive mission of instating a robust Identity and Access Management (IAM) system from scratch. Embrace the challenge, Architect. Let us see how you could achieve this project:
1) Mission Briefing – Aligning Business Vision
Your first task is understanding the battlefield. Understand the business requirements. What challenges do they face? Why do they believe IAM is their silver bullet? This isn’t just an IT or Cybersecurity mission; it’s an organization-wide transformation. Engage key stakeholders: IT, HR, legal, and crucial business units. Their insights are invaluable. As you gather intelligence, critically evaluate the current identity infrastructure and tools. This will give you a bird’s eye view of the gaps, redundancies, and potential pain points.
2) Setting the Parameters – Defining Boundaries
After you’ve gathered the business requirements information, it’s time to set the scope. IAM is a wide topic. Do you plan to cover every little detail on the first day? Define which systems, applications, and user populations fall under this phase. This clarity will arm you for the next crucial stage: budgeting. Resources aren’t infinite. Allocate funds judiciously for software, consulting, training, and unforeseen operational costs.
3) Choosing Your Arsenal – Product & Architecture
The market is inundated with IAM solutions, each with its set of promises. Your mission is to go carefully through this and select the tool that resonates with the business needs, aligns with the budget, and scales for the future.
Selecting the right IAM solution can be a maze, especially if you’re just stepping into the field. Start by diving into datasheets of leading products; they’re goldmines of feature lists and technical specifications. Compare solutions side-by-side to align with your requirements. Don’t shy away from seeking insights from seasoned consultants; their experience can guide your choice. But remember, nothing beats hands-on testing. If possible, run a Proof of Concept (POC) with your top choices. Set clear criteria for evaluation, and see how each product fares in a real-world scenario. Your perfect fit is out there; it’s all about methodical exploration.
Once you’ve considered the right IAM system, dive deep into the architecture. Consider redundancy, high availability, and disaster recovery. A robust system is one that remains unyielding even when battered by unforeseen calamities.
4) Laying the Foundation – Integration & Data Management
Your chosen IAM isn’t an island. It needs to communicate, integrate, and play well with existing systems and applications. Identify these touchpoints.
Remember, in the IAM (or any data-driven system), the accuracy, consistency, and quality of the data you work with are most important. When discussing identity data, this could include information such as usernames, email addresses, job roles, permissions, and more. If this data is messy, inconsistent, or outdated, it can lead to several challenges such as; incorrect access, operational inefficiencies, and security Risks.
5) Crafting the Rulebook – Access & Policies
In a large and detailed IAM project, defining the rules and guidelines is the key to success. This revolves around establishing a robust Access Control mechanism. Don’t just pin everything to one model. While Role-Based Access Control (RBAC) is popular, it’s just one of many approaches. There are also Attribute-Based, Mandatory, and Discretionary models, among others. Your aim? Choose a mechanism that seamlessly aligns with your company’s structure, workflow, and security demands. Simultaneously, craft clear-cut policies for user onboarding, offboarding, password resets, and other IAM-centric processes. Remember, a rulebook not only guides but safeguards. It’s the backbone of a secure IAM infrastructure.
6) Compliance, Auditing & Lifecycle Management
Ensuring compliance isn’t optional. Your IAM should meet, if not exceed, all regulatory benchmarks. Auditing capabilities are your eyes and ears; they’ll alert you if something’s amiss. Alongside, design watertight processes for user lifecycle management, provisioning, de-provisioning, role changes, and imperative access reviews.
For instance, the ISO/IEC 27001 standard, A.9.2.6 mandates regular reviews of user access rights. Another example is NIST SP 800-53, under control AC-2 (Account Management), which necessitates the management of information system accounts, including establishing, activating, modifying, reviewing, disabling, and removing accounts.
7) Tools & Training – Empowering Users
Authentication methods are your first line of defense. Choose wisely. Will it be passwords, multi-factor authentication, biometrics, or a combination? Also, In a world where everyone wants things right away, consider self-service capabilities. But, empowerment without knowledge is dangerous. Train the end-users, system administrators, and the ever-critical support staff.
8) Field Testing & Roll-out Strategy
Before full deployment, test your system. Start small, maybe a unit or system test, scaling to integration, performance, and the critical user acceptance testing. The real world differs from the lab. Consider a phased roll-out, starting with a pilot group. This measured approach lets you gather feedback and finetune before the grand reveal.
9) Feedback, Monitoring & Anticipating Challenges
Your IAM system is now live. But the mission isn’t over. Establish feedback mechanisms; they’re your pulse on the ground. Implement monitoring tools to oversee health and usage. Remember, you’re guarding a fortress. Have an incident response plan ready for potential breaches. Document every strategy, policy, procedure, and configuration. This is your playbook.
10) Looking Ahead – Review & Continual Enhancement
In the Oil and Gas sector which is the case in this project example, stagnation is the enemy. Periodically review access rights, roles, and policies. Have backup procedures and disaster recovery tools in place. The goal is resilience. And as the dust settles post-implementation, never cease to assess and enhance your IAM system. Continuous improvement isn’t just a catchphrase; it’s your mantra.
Your task, Architect, is immense. Yet with this guide, you’re equipped not merely to traverse but to excel in the complexities of IAM within a vast enterprise. So Well Done!
Quick Quiz
Summary
IAM, at its core, serves as the Key piece in today’s enterprise digital infrastructure, ensuring that the right people have the right access at the right time for the right reason. It’s a discipline that encompasses the vast landscape of ensuring digital identities are managed, monitored, and maintained securely. At the onset of our exploration, we demystified the often conflated concepts of IAM and Identity Management (IdM). While the former is a broader framework focusing on policies and technologies for user management, the latter zooms in on individual identity lifecycles.
Our journey then led us to the foundational principles that underpin IAM. Each principle constructs a layer in the fortress that defends against breaches and misuse. Our case study breathed life into these principles, presenting a real-world scenario that illuminated how these layers work together to bolster security.
But IAM isn’t an island. Its evolving nature is deeply intertwined with the Zero-Trust model, a paradigm shift in security. Zero-Trust challenges the traditional trust but verify approach, instead advocating for a “never trust, always verify” mindset. Our discussion revealed the mutual relationship between IAM and Zero-Trust. On one hand, Zero-Trust measures can be implemented to safeguard the IAM framework, adding another layer of security. Conversely, a robust IAM framework can offer the data and intelligence necessary for a more streamlined operation of Zero-Trust protocols.
Drawing from these insights, we ventured into “Project IAM.” This segment was a testament to the idea that understanding IAM is only half the battle, implementing it effectively is where the challenge truly lies. From discerning business requirements to ensuring compliance, from crafting the right access policies to ongoing reviews and continuous improvement, a successful IAM project is a precise combination of strategy, collaboration, and technology.
The blueprint for a successful IAM project, as detailed in our mission guide, was designed to empower budding architects. With stages thoroughly charted out, it provided a roadmap for navigating the puzzling challenges of integrating IAM in a large enterprise. Selection of the right tools, engagement with stakeholders, diligent planning, and a commitment to best practices are all crucial to this journey.
In short, IAM isn’t just a toolset or a set of guidelines; it’s a philosophy. It underscores the importance of identity in the digital age, where boundaries are nebulous and threats are ever-evolving. As we stand on the precipice of more technological innovations, the role of IAM is set to become even more significant. The fusion of IAM with evolving paradigms like Zero-Trust signifies that the realm of identity and access isn’t static; it’s dynamic, demanding constant vigilance and evolution. As future architects in this realm, your role will be important in shaping, securing, and streamlining the digital identities of tomorrow.
Your Homework
- Explore a popular online service (e.g., Google, Microsoft) and list the IAM features you can identify (MFA, password policies, etc.).
- Find a recent news article or case study about a company that faced security issues due to poor IAM practices. Summarize the key points and lessons learned.
- Compare and contrast at least two IAM solutions available in the market. Create a pros and cons list for each.
- Set up a basic IAM solution using open-source software. Document your experience, challenges, and findings.
- Create a flowchart or diagram illustrating the lifecycle of a user identity in an enterprise from onboarding to offboarding.
- Identify your personal online habits and evaluate them in the context of IAM best practices. Draft a personal IAM improvement plan.
- Dive deeper into NIST or ISO regulations related to IAM. Summarize the key guidelines that were not covered in the lesson.
If you learned something new today, help us to share it to reach others seeking knowledge.
If you have any queries or concerns, please drop them in the comment section below. We strive to respond promptly and address your questions.
Thank You









