Table of Contents

Have you ever wondered why we hear so much about cyber attacks on the news? Or why there’s such a buzz around protecting digital information? In today’s rapidly evolving digital landscape, the stakes have never been higher. As we increasingly intertwine our lives with the digital realm, from online banking to social connections, the risks also surge. Fundamental to navigating this digital expanse is understanding the language of cybersecurity. Terms like “Threat,” “Risk,” “Exploit,” and “Vulnerability” are not just jargon but the foundation upon which our entire digital defense stands. By grasping these terms and the nuances behind concepts like the CIA Triad, we arm ourselves with the knowledge to decipher complex cyber challenges. Recognizing the difference between a Threat Actor and an Adversary or understanding what a zero-day exploit signifies can be the difference between safeguarding our assets and facing a cyber calamity. This lesson is more than just definitions; it’s about equipping you with the essential tools to comprehend and counteract the myriad cyber threats we face in our connected world. Dive in, and let’s demystify the intricate tapestry of cybersecurity together.
What is Cybersecurity?
Cybersecurity is the practice of defending our computers, servers, mobile devices, electronic systems, networks, and data from malicious digital attacks. It’s akin to a digital guardian, ensuring that our information remains confidential, our systems are integral, and our digital interactions are available when we need them. As we transfer most of life businesses into cyberspace, understanding and implementing cybersecurity becomes not just a best practice, but a necessity for all.
Imagine, a world where we left our homes, cars, or treasured possessions unlocked and unprotected. Sounds risky, right?
Similarly, in the vast realm of the internet, ignoring cybersecurity is like leaving your digital “doors” wide open. If we were to sidestep cybersecurity, we risk unauthorized access, data breaches, financial losses, and even potential threats to critical infrastructure. It’s not just about protecting files and data; it’s about safeguarding our digital way of life. We are not protecting computers anymore, but we protect the whole society’s structures (national security, healthcare, finance, and more). This has become the main objective of cybersecurity even though at first glance it seems we deal with technical problems. Without robust cybersecurity, our personal information, bank details, and even national secrets could be at stake. In an interconnected world, cybersecurity isn’t a luxury; it’s a lifeline to ensure trust, safety, and harmony in our digital interactions. Let’s pledge to not only understand its significance but to actively prioritize it, ensuring a resilient and trustworthy digital future for all.
A common question people use to ask is what is the difference between Information Security and Cybersecurity?
Let us answer this key question!
Information Security, often shortened to InfoSec, is the broader practice of preventing unauthorized access, use, disclosure, disruption, modification, or destruction of information, irrespective of its format. It encompasses not only electronic data but also physical data. Imagine you have a confidential paper report; securing that report in a locked cabinet is an act of information security.
On the other hand, Cybersecurity is a subset of InfoSec that specifically focuses on protecting electronic data from cyber threats, primarily on internet-connected systems. Consider your online bank account: Using strong, unique passwords and two-factor authentication to protect it from hackers exemplifies cybersecurity.
While all cybersecurity measures are a part of information security, not all information security measures fall under cybersecurity. Both are crucial, serving as protective layers for our data—be it on paper, in a computer, or floating in the vast cyberspace. As stewards of our own information, it’s essential for each of us to appreciate the differences and ensure we’re adequately protected in every scenario.
CIA Triad – Cybersecurity Core Principles
The CIA Triad stands for Confidentiality, Integrity, and Availability, representing the three core principles essential to ensuring cybersecurity. Like the sturdy legs of a tripod, each principle supports the structure of a robust and resilient cybersecurity posture. By diligently upholding these principles, organizations and individuals can effectively safeguard their digital assets, ensuring that information is kept secret from unauthorized eyes, remains unaltered unless legitimately modified, and is accessible when needed.
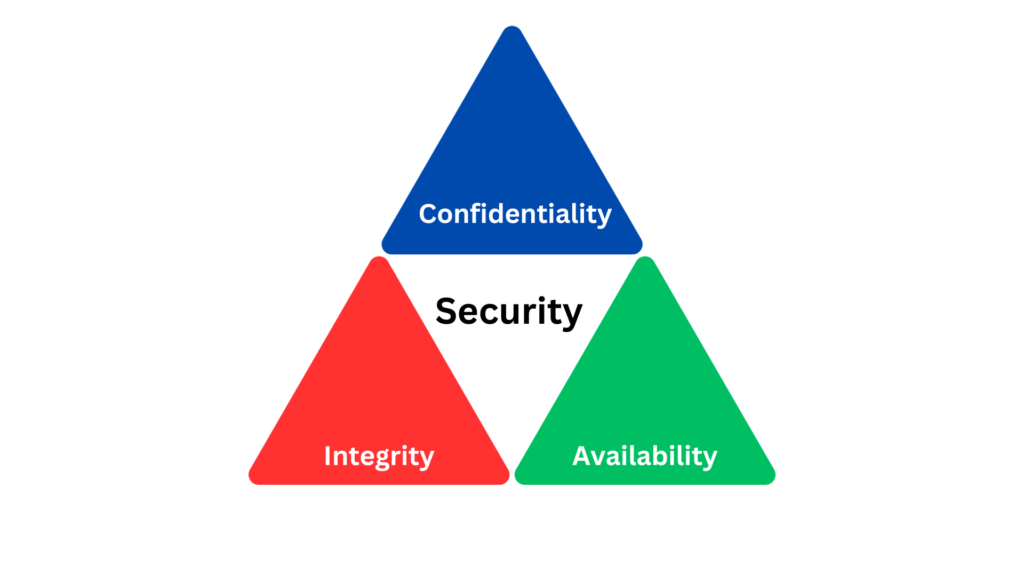
What is Confidentiality?
Confidentiality pertains to the protection of information from unauthorized access or disclosure. It ensures that only those who are meant to see certain data can access it. Envision it as a secret whispered only to a trusted friend; nobody else, no matter how close they stand, should be able to hear it. Implementing strong encryption, access controls, and authentication mechanisms helps in maintaining confidentiality.
What is Integrity?
Integrity ensures that data remains consistent, accurate, and trustworthy throughout its lifecycle. It’s the guarantee that the information has not been altered in unauthorized ways. To draw a parallel, imagine signing a contract; you’d want to be certain that no one has made any changes to it without your knowledge. Mechanisms like checksums, digital signatures, and hashing algorithms are often employed to preserve data integrity.
What is Availability?
Availability ensures that information and resources are accessible to authorized users whenever they need it. Just like expecting water from a tap when turned on, users expect systems and data to be available when they require them. To ensure availability, organizations implement redundant systems, backup solutions, and disaster recovery plans to counteract potential outages or interruptions.
Together, these three principles form the foundation for building and evaluating security policies and practices in the realm of cybersecurity.
Note that, these principles can be represented with DAD Triad, standing for Disclosure, Alteration, and Denial, represents the direct threats opposing the principles of the CIA Triad.
Disclosure is the unauthorized access or revealing of information, countering Confidentiality.
Alteration pertains to unauthorized changes made to data, challenging Integrity.
Denial represents the prevention of legitimate access to resources or information, opposing Availability.
Quick Challange
The table below illustrates 10 Cybersecurity controls and how they are aligned to CIA Triad:
| Cybersecurity Control | Confidentiality | Integrity | Availability | Justification |
|---|---|---|---|---|
| Antimalware | Yes | Yes | Yes | Antimalware helps protect data from unauthorized access and alteration (maintaining confidentiality and integrity). It also ensures systems are free from malicious software that might disrupt services (ensuring availability). |
| Encryption | Yes | Encryption scrambles data, making it unreadable to unauthorized users, thereby directly supporting confidentiality. | ||
| Digital Signatures | Yes | Digital signatures ensure that a message or document remains unchanged (integrity) and verifies the identity of the sender. | ||
| Backup Solutions | Yes | By regularly backing up data, organizations ensure that critical information remains available, even after a data loss event. | ||
| Access Control Lists (ACLs) | Yes | Yes | Yes | ACLs define who can access data and what they can do with it, thus ensuring confidentiality, integrity, and availability by providing appropriate rights to users. |
| Firewalls | Yes | Yes | Firewalls prevent unauthorized access (supporting confidentiality) and ensure that services are available by blocking disruptive traffic. | |
| Multi-Factor Authentication (MFA) | Yes | MFA adds an additional layer of security, ensuring that only authorized users can access sensitive information, reinforcing confidentiality. | ||
| Intrusion Detection System (IDS) | Yes | Yes | IDS monitors network traffic for malicious activities, preserving data confidentiality and integrity by identifying potential breaches. | |
| Data Loss Prevention (DLP) | Yes | Yes | DLP tools prevent unauthorized data transfers, ensuring data remains confidential and that only authorized changes are made, supporting integrity. | |
| Patch Management | Yes | Yes | Yes | By regularly updating software, vulnerabilities are fixed, reducing risks of unauthorized data access, alterations, and service disruptions. |
Threats and Attacks
Let us proceed with our lesson. Let us highlight the main cyber threats we are facing today. Cyber threats are quite challenging and variant, we cannot cover all of them in one lesson, therefore we decided the spot the light for each one of them in a separate and dedicated lesson.
In the vast, interconnected expanse of the cyber domain, threats are evolving constantly. Just as our digital footprints expand, so do the methods and means by which malicious actors attempt to compromise, exploit, or damage our systems and data. These threats can originate from a lone individual, organized cybercriminal groups, or even state-sponsored entities. They range from exploiting software vulnerabilities to sophisticated phishing attacks and, if successful, can result in significant financial, reputational, and operational harm.
Below are the main cyber threats we are facing today:
Malware
A broad category that includes malicious software like viruses, worms, and ransomware. These are designed to infect and damage systems, steal data, or both.
Phishing
Deceptive attempts, often through email, to trick individuals into revealing sensitive information, like passwords or credit card numbers.
Man-in-the-Middle (MitM) Attacks
Unauthorized interception of communication between two systems to eavesdrop or impersonate one of the parties, making it seem as if a normal exchange of information is underway.
Denial of Service (DoS) and Distributed Denial of Service (DDoS) Attacks
Overwhelming a system, network, or service with traffic, rendering it inaccessible to legitimate users.
SQL Injection
A technique where nefarious SQL statements are inserted into an entry field, leading to unauthorized viewing of data, corrupting, or deleting it.
Cross-Site Scripting (XSS)
Injecting malicious scripts into websites which then run in the user’s browser, potentially stealing data or facilitating other attacks.
Zero-Day Exploit
An attack that targets software vulnerabilities before the developer has become aware and, thus, before a fix or patch has been released.
Drive-By Downloads
Unintentional download of malicious software onto a user’s system when visiting a compromised website.
Rogue Software
Malicious software that masquerades as legitimate and useful software, tricking users into downloading and installing it.
As we stated, these are not the full list of cyber threats, but they are the key to knowing about them.
Threat Actors, Threat Agents, and Adversaries
Threat Actors and Adversaries are terms frequently used interchangeably in the cybersecurity realm to describe individuals or entities responsible for incidents that can negatively impact or harm digital assets. These actors operate with various motivations such as financial, political, ideological, or even just for notoriety. While “threat actor” often refers to any entity that poses a potential harm, “adversary” connotes an antagonistic or competitive force against an organization. Whether it’s a lone hacker, an organized cybercriminal group, a disgruntled insider, or a nation-state entity, these actors represent the sources of potential cyber threats and challenges faced in safeguarding our digital domain.
Within the complex landscape of cybersecurity, adversaries emerge with varying motivations, skill sets, and resources. Their reasons to engage in cyber malfeasance can range from personal profit, espionage, and political motivations to sheer curiosity or chaos generation. Recognizing the typical players in this domain aids in understanding the multi-faceted nature of cyber threats and tailoring defense strategies accordingly.
For instance, an employee accidentally downloaded a malware from a phishing email, this employee is called the Threat Actor. While the cybercriminal group specifically crafted that email to infiltrate the company’s network is called the Adversary.
Also, do not get confused between Threat Actor and Threat Agent. A Threat Actor and Threat Agent are terms often used interchangeably, but subtle distinctions exist. As we defined Threat Actor specifically refers to an individual or entity responsible for an event that has the potential to harm an organization’s assets. On the other hand, a Threat Agent can be a person, group, or even a natural phenomenon (like a flood or fire) that has the potential to exploit a vulnerability, intentionally or unintentionally. Essentially, while all Threat Actors are Threat Agents, not all Threat Agents are necessarily Threat Actors. The differentiation often revolves around intent and agency.
With this definition, you might also get confused about the difference between Adversary and Threat Agent. Let us clarify that too!
An Adversary implies intent and typically refers to individuals, groups, or entities that act with a specific goal or malicious purpose in mind, such as hackers, nation-states, or competitors. In contrast, a Threat Agent can include natural phenomena because it’s a broader term that encompasses any source of potential harm, regardless of intent. Natural events, like floods or fires, are considered Threat Agents because they can exploit vulnerabilities (like a data center located in a floodplain) but don’t have intent and, hence, wouldn’t be categorized as Adversaries.
The below image illustrates that Threat Agent is a comprehensive label, capturing a diverse range of threat types, emphasizing its broad and complex nature in cybersecurity.
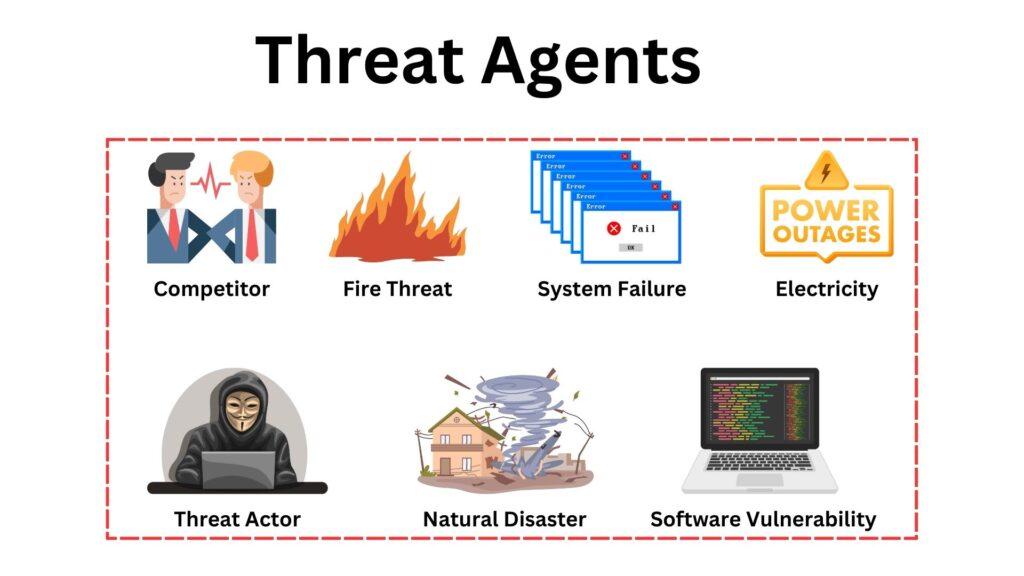
Let us talk briefly about Threat types:
Hacktivists
Individuals or groups who commit cyber-attacks primarily for political or social motives. Their intent often revolves around promoting a particular cause or message, sometimes leading to website defacement or data leaks.
Let us talk briefly about each type of Threat Actor
Cybercriminals
Individuals or syndicates engaged in cyber activities for monetary gain. They might be involved in activities like identity theft, financial fraud, or ransomware attacks.
Nation-State Actors
Sponsored by national governments, these highly-skilled adversaries aim to gather intelligence, disrupt enemy networks, or achieve strategic geopolitical goals. Their targets often include critical infrastructures, corporations, or government networks.
Insiders
These can be disgruntled employees, contractors, or business partners who misuse their access rights to harm an organization, either for revenge, profit, or other personal motivations.
Script Kiddies
Novice attackers, often young individuals, who use existing hacking tools and scripts to launch attacks without fully understanding their mechanics. They’re typically driven by curiosity or the desire for notoriety.
Competitors
Business entities that engage in cyber espionage or other malicious activities to gain a competitive advantage. They might seek to steal trade secrets, intellectual property, or other proprietary information.
Terrorist Groups
Organizations that deploy cyber tactics as part of their broader mission, which could involve spreading propaganda, disrupting infrastructure, or conducting cyber-financed operations.
Cybersecurity Terminology
In this section, we are going to highlight the key terminology that everyone should be aware of. you must be quite familiar with each of the following terms and understand its meaning and context.
In the next section, we are going to talk about key terminologies such as Risk, Exploit, Threat, and more. But why is understanding these terms so critical?
As an analogy, navigating the digital realm without grasping these foundational concepts is similar to sailing the seas without a compass. Each term provides a unique lens through which we decipher the complex world of cybersecurity. Recognizing what a “Threat” is, or understanding the “Risk” associated with a certain action, empowers individuals and organizations to make informed decisions. Just as a doctor must understand medical terms to diagnose and treat patients, anyone looking to protect their digital assets should be well-versed in cybersecurity lingo. By grasping the nuances of terms like “Exploit” or “Vulnerability,” we can pinpoint weaknesses in our systems, anticipate potential dangers, and enact effective defense measures. This knowledge not only equips us to better anticipate and counteract cyberattacks but also fosters a culture of proactive defense. In essence, understanding this language is our first line of defense, arming us with the awareness and comprehension needed to navigate the intricate and often perilous cyberspace.
Asset
Anything of value to an organization that needs to be protected. Assets can be digital, like databases and software; physical, like hardware; or intangible, like brand reputation. For instance, a company’s customer database containing personal and financial details of all its clients.
Threat
A potential cause of an undesirable event that may result in harm to a system or organization. Threats can be both intentional, like cybercriminals trying to breach a network, or unintentional, such as an employee mistakenly deleting crucial data. For example, phishing emails sent by hackers intending to trick employees into revealing sensitive information.
Likelihood
The probability or chance that a particular threat will exploit a specific vulnerability. It assesses how probable it is for a given threat to take advantage of a vulnerability, considering various factors like the threat actor’s capability and intent. For example, considering the rise in ransomware attacks globally, an unprotected server might have a high likelihood of being targeted.
Vulnerability
A weakness or gap in a system’s design, implementation, or operation that could be exploited by a threat. Vulnerabilities can emerge from flawed software design, misconfigurations, or even inadequate security policies. For example, a software application that hasn’t been updated and contains a known security bug.
Exploit
A method or technique used by a threat actor to take advantage of a vulnerability in a system or network. An exploit can be a piece of software, a set of commands, or even a technique aimed at triggering a vulnerability’s adverse effects. For instance, a script that a hacker uses to gain unauthorized access by leveraging a software vulnerability.
Impact
The magnitude of harm that can be caused if a threat exploits a vulnerability. Impact can be assessed in terms of financial loss, reputational damage, operational downtime, and other negative consequences. For instance, a hospital system getting breached might have a severe impact, potentially compromising patient data and endangering lives.
Risk
The potential for loss or damage when a threat exploits a vulnerability. Risk combines the potential damage (impact) of an event and the likelihood of that event occurring.

An example, consider an online store having a high risk of significant financial loss if its payment gateway has a vulnerability that’s likely to be exploited and result into the hackers gaining the full credit cards information of the customers.
Control
Measures or safeguards that are designed to manage, mitigate, or eliminate specific risks. Controls can be technical, like firewalls or encryption; organizational, like policies; or even physical, like locked doors. Implementing multi-factor authentication to add an extra layer of security beyond just passwords is an example of cybersecurity control implementation.
Quick Challange
The Importance of Training and Awareness

In cybersecurity, vulnerabilities present themselves in two primary forms: technical and human. While technical vulnerabilities can often be addressed through software patches or system updates, human vulnerabilities stand distinct. There exists no ‘patch’ for human errors or lapses in judgment. The most effective remedy for this human susceptibility is consistent training and raising awareness. By empowering individuals with knowledge and vigilance, we transform potential weak points into robust lines of defense in our overarching cybersecurity strategy.
The landscape of cybersecurity isn’t static; it evolves rapidly. Every day, new vulnerabilities are discovered, and fresh threats emerge, posing challenges even for seasoned technical professionals. For instance, a malware analyst who was adept at handling threats a year ago might find themselves unprepared for the latest ransomware variant if they haven’t kept up with recent developments. Similarly, a CISO or CIO’s strategy built on last year’s threat intelligence might be insufficient to address the current cyber risks. As the infamous 2017 Equifax breach illustrated, even a missed update on a single software patch can lead to massive data compromises. With such dynamics, regular training becomes imperative not just to stay ahead but simply to keep up.
Cybersecurity is not just a technical concern. While it’s intuitive to think of cybersecurity as a purely technical domain, in reality, human factors play an equally, if not more, significant role. Many high-profile breaches, like the 2016 DNC email leak, began with a simple phishing email. An unaware employee, irrespective of their role – be it a manager, CEO, or even a non-technical staff member – can inadvertently become the weak link, granting adversaries a foothold into secure systems. Every individual in an organization, from the mailroom to the boardroom, interacts with digital systems and data. This universal digital interaction means that everyone, without exception, must be equipped with at least basic cybersecurity knowledge. For home users, the stakes are personal; a lack of awareness can lead to identity theft, financial loss, or unauthorized access to sensitive personal data.
Training and awareness aren’t merely about reactive measures but fostering a culture of proactive defense. Regular training sessions underscore the importance an organization places on cybersecurity, making it a shared responsibility rather than a segregated IT concern. When a security engineer is equipped with the latest threat intelligence, they can better design secure systems. When a CEO understands the ramifications of a potential data breach, they can allocate resources more judiciously towards cybersecurity measures. Even at home, when parents are aware of digital threats, they can guide their children in safer online behaviors. Real-world examples abound, such as the WannaCry ransomware attack of 2017, which affected thousands of organizations, including hospitals. Here, outdated systems and a lack of awareness compounded into a global crisis. Regular training could have mitigated, if not entirely prevented, such widespread havoc.
Conclusion
Cybersecurity is more than just protecting computers; it’s about safeguarding every part of our lives and businesses in today’s interconnected world. When we talk about terms like ‘Threats’, ‘Risks’, and ‘Exploits’, we’re trying to understand the challenges we face in the world of cyberspace. We’ve seen that tools like Antimalware are crucial to protect the key principles of cybersecurity, embodied in the CIA Triad. However, even with the best tools and technology, there’s a human side to all of this. Mistakes can happen, and sometimes a simple error can lead to big problems. This is why understanding the difference between roles, like Threat Actors and Adversaries, is important.
Yet, the most critical lesson is understanding the role each of us plays in keeping the digital world safe. Our computers and devices are all connected, so a problem in one place can quickly spread to another. We must work together, learn regularly, and stay aware of the threats around us. Whether you’re a computer expert or just someone using a phone, you have a part to play. Because in cybersecurity, every device and every user matters. It’s about building trust and safety for everyone in our shared cyberspace. So let’s take cybersecurity seriously, learn together, and make sure we’re all protected.
If you learned something new today, help us to share it to reach others seeking knowledge.
If you have any queries or concerns, please drop them in the comment section below. We strive to respond promptly and address your questions.
Thank You


