Table of Contents

Welcome to a journey through the invisible yet indispensable world of Wi-Fi and wireless security. If you wonder how confidential information remains secure when sent through the air? or what measures do you need to know to make your Wi-Fi communication private so that no one can access it? This lesson is your gateway to understanding these marvels.
In 1997, the world saw the birth of Wi-Fi technology, a game-changer in the realm of digital communication. Fast forward to today, and Wi-Fi is as ubiquitous as the air we breathe, powering connections in homes, offices, and public spaces across the globe. But with great convenience comes great responsibility – the responsibility of safeguarding data.
This lesson examines the key components that make Wi-Fi networks function and the sophisticated security protocols that protect them. You’ll journey through the evolution of security standards from WEP to WPA3, uncovering their strengths, weaknesses, and the continual advancements made to counteract emerging cyber threats.
Introduction to Computer Wi-Fi
Wi-Fi, is a technology that has become as essential to our daily lives as electricity and running water. Wi-Fi is the wireless technology that allows computers, smartphones, and other devices to connect to the Internet and communicate with each other without the need for wired connections.
Wi-Fi is a term that originally stood for “Wireless Fidelity” a play on the long-established term “Hi-Fi” or “High Fidelity” used in the audio industry. Over time, Wi-Fi has evolved beyond its original name to become a universal term for IEEE 802.11 wireless network protocols. It refers to a family of wireless networking technologies that use radio waves to provide high-speed network and Internet connections.
The development of Wi-Fi technology began in the late 1990s. In 1997, the Institute of Electrical and Electronics Engineers (IEEE) created the first Wi-Fi standard; 802.11, which was capable of supporting bandwidths up to 2 megabits per second. It was a breakthrough but not quite enough for practical wireless local area networking (WLAN). However, the technology quickly advanced, and in 1999, the 802.11b standard was released, which increased speeds to 11 megabits per second, making it widely popular.
Prior to Wi-Fi, connecting devices to a network or the internet meant using physical cables. Not only did this restrict where devices could be located, but it also limited the mobility and ease of connecting new devices. Cables were, quite literally, the chains that tied down our devices. Wi-Fi offered a solution to these limitations. It provided the convenience of connecting to the Internet while moving freely around a space, untethering computers from their wired confines. With Wi-Fi, setting up a network became simpler, and the scalability of these networks increased dramatically. Users could connect multiple devices without the need for additional wiring, changing the landscape of how we interact with our devices.
This wireless revolution brought forth a new wave of technological innovation. Offices could now be free of the clutter and hazard of wires, students could access resources and collaborate from anywhere on campus, and home entertainment systems could stream content without cumbersome cabling.
More importantly, Wi-Fi has been the backbone of the mobile revolution. It enables smartphones, tablets, and laptops to access a vast wealth of online information and services without the need for cellular data. The development of public Wi-Fi hotspots also made it possible for people to stay connected on the go without relying on their mobile network, ushering in a new era of mobility.
It’s important to note that “Wireless” is an umbrella term, and Wi-Fi is just one of the many wireless technologies that fall under this broad category. Here are brief descriptions of some other common wireless technologies:
Bluetooth: Exchange data over short distances between devices.
Cellular Networks (3G/4G/5G): Provide mobile communication and data transfer.
Near Field Communication (NFC): Enables close-proximity device communication.
Infrared (IR): Transmits data using infrared light waves.
ZigBee: Offers low-power, low-data rate wireless networking.
Li-Fi: Transmits data through visible light communication.
In this lesson, we will talk and discuss Wi-Fi Security.
The Role of Radio Waves
Wi-Fi technology mainly uses radio waves to transmit data. These are a type of electromagnetic wave, like light waves or X-rays, but with a much longer wavelength. Radio waves are ideal for wireless communication because they can travel through the air, penetrate walls and other non-metallic objects, and cover a decent range without requiring direct line-of-sight.

While radio waves are the most common medium for wireless communication, there are alternatives. For instance, Infrared (IR) is used in remote controls, Li-Fi uses visible light for data transmission, and microwave communication is employed in satellite and long-distance communications. However, these alternatives have limitations. IR requires line-of-sight, Li-Fi can be disrupted by light interference, and microwaves are more suited for point-to-point communication over long distances.
Radio waves are preferred for Wi-Fi due to their ability to provide a good balance between range, penetration through obstacles, and data carrying capacity. They don’t require line-of-sight and can cover larger areas, like homes or offices, making them suitable for local area networking. Apart from Wi-Fi, other technologies that use radio waves include cellular networks (like 3G, 4G, 5G), Bluetooth, and broadcast radio and television. Each of these technologies operates at different frequency bands and serves different communication needs.
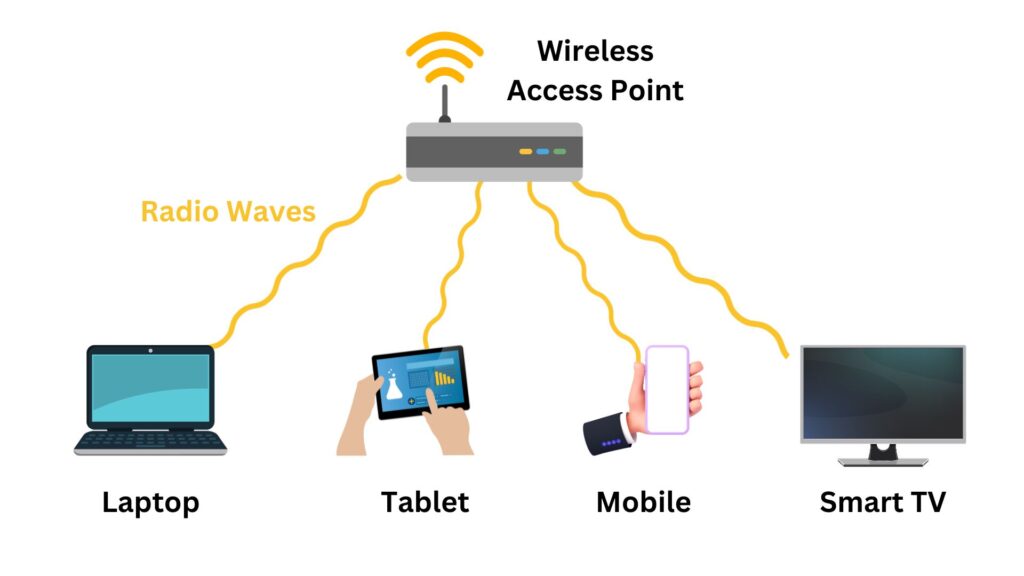
The depiction of radio waves as circles emanating from a point (like a Wi-Fi router) is a simplified way to represent how these waves propagate. In reality, radio waves spread out in all directions from the source, creating a coverage area. When a device like a laptop is within this area, it can receive the signals sent by the Wi-Fi access point (WAP).

In Wi-Fi networks, a router broadcasts radio signals in all directions from its antennas, creating an omnidirectional spread of the same signal, which ensures wide area coverage. This means that any device, including those of potential hackers, within the Wi-Fi’s coverage area can receive these signals. Therefore, the signals intended for a specific user can also be intercepted by others nearby. Unlike wired networks where physical connections restrict signal access, the open nature of radio wave propagation in Wi-Fi makes it accessible to any receiving device in range. Consequently, this necessitates the use of robust encryption protocols which are crucial for ensuring the security and privacy of the data being transmitted over these wireless networks.
Wireless Local Area Network (WLAN)
A WLAN, or Wireless Local Area Network, is a type of local area network that uses high-frequency radio waves rather than wires to communicate and transmit data between devices. It provides wireless network communication over short distances and is often used in homes and businesses alike. Wi-Fi is the most common technology used to implement a WLAN.
Utilizing radio waves, a WLAN is typically centered around a wireless router or access point that broadcasts the signal devices connect to. It provides the flexibility and mobility to access network resources without the limitations of physical cables. WLANs are based on the IEEE 802.11 standards, which define the protocols for transmitting data and ensuring secure communications. Users can seamlessly access the internet, share files, and print documents wirelessly. WLANs support various security protocols like WEP, WPA, and WPA2 to protect data and maintain privacy. With the proliferation of Wi-Fi-enabled devices, WLANs have become ubiquitous in modern life, offering convenient and efficient connectivity in both personal and professional settings.
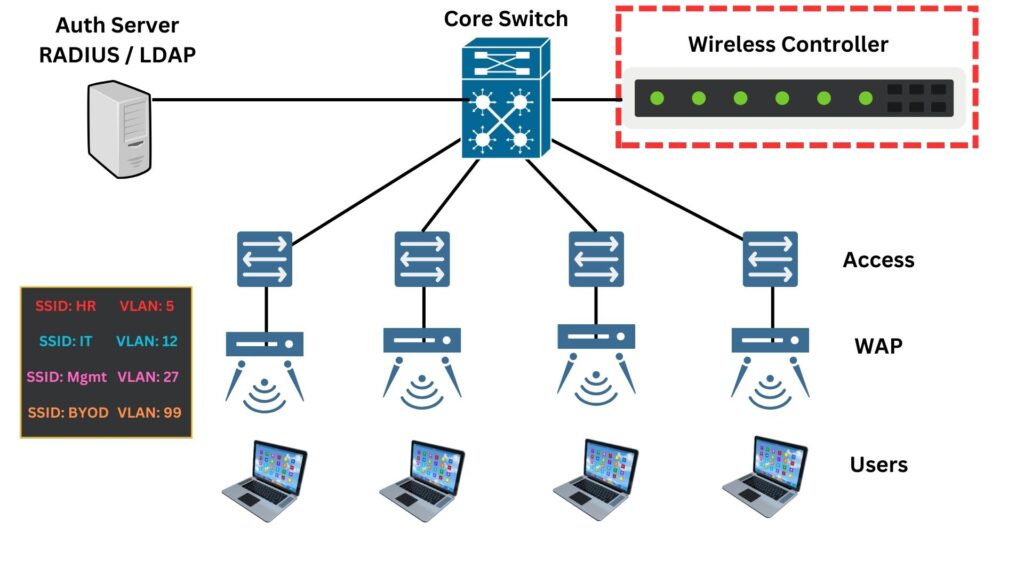
A typical WLAN architecture in an Enterprise network looks like the following:
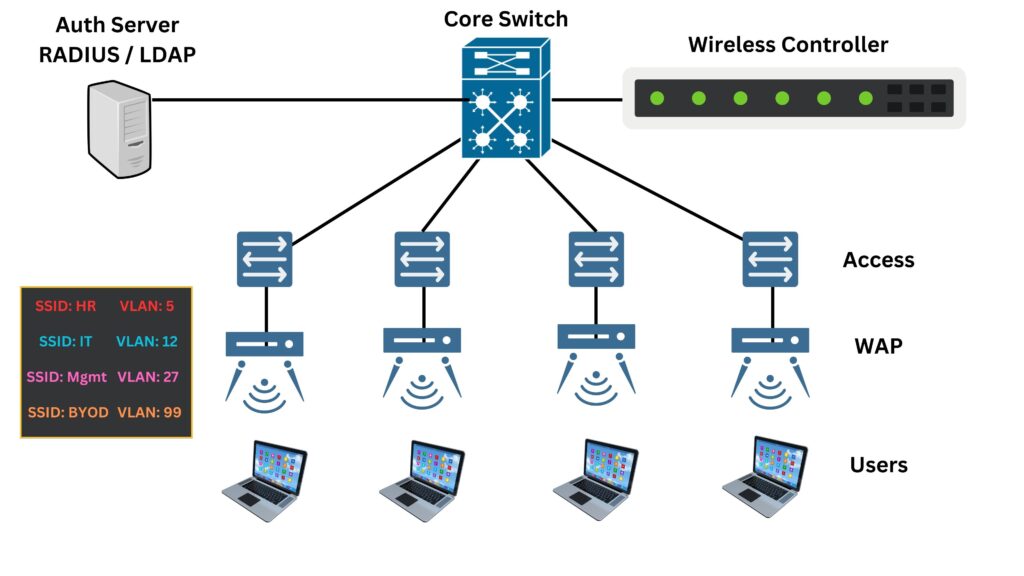
WLAN has several key components that make wireless networking possible:
- Wireless Access Points (WAPs): These are the heart of the WLAN. WAPs connect to the wired network and serve as the central transmitter and receiver of wireless signals.
- Wireless Controllers: Often used in larger WLANs, wireless controllers manage multiple WAPs, handle connections, and enforce security policies.
- Authentication Server: Often using protocols like RADIUS or LDAP, this server verifies user credentials before granting access to the WLAN. It ensures that only authorized users can connect to the network.
- WLAN network cards: Allow client devices like laptops, phones, tablets, IoT devices to connect to the Wi-Fi network through the APs. It may be USB adapters or built into devices.
- Antennas and Signal Boosters: These can extend the range and improve the quality of wireless signals.
- Network Switches and Routers: These are the backbone of the wired network that supports the WLAN, routing traffic and providing connectivity to the wider internet.
The core layer can be one or two tiers (Core and Distribution) depending on how large the network is. However, this layer includes switches and routers that form the backbone of the enterprise network. It’s where the main data processing happens.
The Access Layer switches should have a direct cable (wired) connection to the WAPs that provide wireless connectivity to end-user devices.
The workflow of a WLAN in an enterprise setting typically follows these steps:
- Your device, like a laptop or smartphone, connects wirelessly to a Wireless Access Point (WAP).
- When you try to access the internet or a network resource, your device sends the data to the WAP.
- The WAP forwards this data to the network’s core via a wired connection or a wireless controller (depending on the setup).
- The core network, which includes routers and switches, directs the data to its final destination, such as a server or the internet.
- Any data sent back to your device from the internet or server takes the reverse path: from the core network to the AP, and finally to your device.
Note that, in traditional enterprise WLAN architectures, the wireless controller often plays a central role, but it does not necessarily have to be inline for all wireless network traffic. The role of the wireless controller can vary based on the network design:
- Centralized Deployment: In a centralized WLAN architecture, the wireless controller is indeed in the path of the traffic. Wireless Access points (WAPs) forward user traffic to the controller, where policies are applied, and then the controller sends the traffic to the wired network. This setup allows for easier management and tighter security controls.
- Distributed Deployment: With the evolution of wireless technology, there’s a shift towards more distributed architectures, like controller-less (or virtual controller) deployments. In these cases, WAPs handle traffic directly after initial configuration and management from the controller. The controller manages the WAPs, but the data traffic may bypass the controller entirely after the WAPs establish the connection with the devices.
- Hybrid Deployment: Some modern enterprise WLAN setups use a hybrid approach, where some traffic is processed locally at the WAP, while other traffic is sent to the controller. For example, internal traffic might be routed locally within the WAP to avoid unnecessary load on the controller, while traffic destined for external networks may go through the controller for security and policy enforcement.
Let Us Connect to Wi-Fi Network
A User Connects to SSID
An SSID (Service Set Identifier) is the name assigned to a wireless network. When you set up a Wi-Fi network, you give it a name to distinguish it from other networks in range. This name is the SSID. Whenever a Wi-Fi-enabled device searches for available networks, the SSID is what appears in the list of network options. SSIDs are case-sensitive text strings, and can be up to 32 characters long. They serve as the primary identifier for a network and can be hidden or broadcasted. If broadcasted, the SSID allows users to see and select the network to attempt a connection.
Imagine you’ve just arrived at the office, opened your laptop, and you’re ready to start your day by connecting to the company’s Wi-Fi network. Here’s a step-by-step look at what happens when you connect to the HR SSID:
- Your laptop uses its wireless network adapter to search for available Wi-Fi networks. It sends out a signal asking for any nearby access points (WAPs) to respond.
- You see a list of available SSIDs on your laptop’s screen. SSIDs are like network names. You find and select “HR” from the list, which is the Wi-Fi network set up for your department.
- After selecting the “HR” SSID, your laptop sends a request to the corresponding WAP asking to join that network.
- The WAP asks for credentials to make sure you’re authorized to access the HR network. You enter your username and password. This information is sent securely to the WAP.
- Your login details are forwarded by the WAP to an Authentication Server through the controller. This server checks your credentials against the company’s records.
- If your details are correct, the Authentication Server tells the WAP to grant your laptop access to the network.
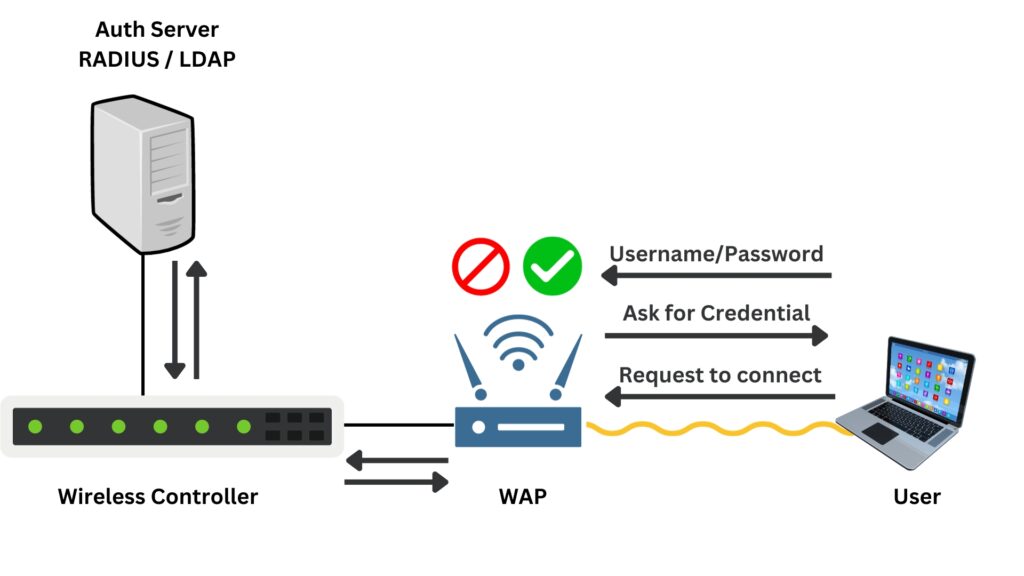
WAP acts as an enforcer in the network, implementing the policies set by the wireless controller, ensuring that only authorized users are allowed access, and managing network resources to maintain a secure and efficient wireless environment.
- Once access is granted, the WAP assigns an IP address to your laptop. This IP address is unique to your device and is used to identify it on the network.
- Since you’re connecting to the HR SSID, the WAP knows to assign your laptop to VLAN 5. VLANs are like separate lanes on a highway; they keep network traffic organized and secure. Your laptop is now on the HR department’s private network lane.
- With an IP address and VLAN assignment, your laptop can now communicate with other devices on the HR network securely.
- If you want to access the internet, the WAP routes your requests through the Access Switch, then to the Core Switch, and finally out to the internet.
From your perspective, all you did was select the HR network and enter your login details. Behind the scenes, the WAP, Authentication Server, and network switches work together to ensure you have a secure and seamless connection to the Wi-Fi network. Remember, all of this happens in just a few seconds! It’s a complex dance of signals and checks that allows you to get online quickly and securely.
Encryption in Wi-Fi Network
In a WLAN setup, the segment of network traffic between the laptop and the WAP is encrypted. This is designed to protect the data as it travels through the air, where it is most vulnerable to interception or eavesdropping.
When you connect your laptop to the Wi-Fi network and access resources or the internet, the data packets are encrypted before they leave your device. This encryption acts like a secure tunnel between your laptop and the WAP, ensuring that any sensitive information such as passwords, emails, or company data remains confidential.
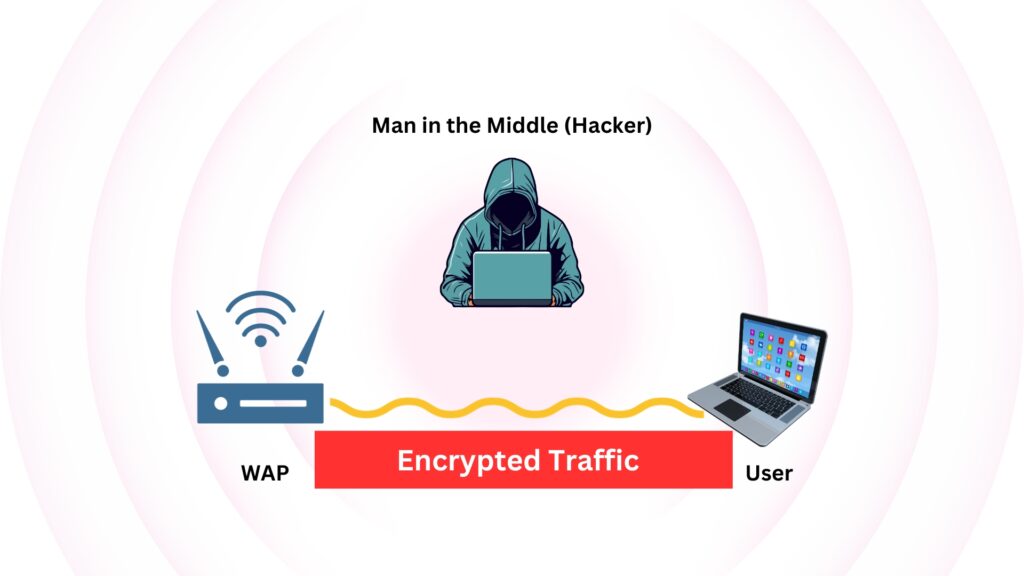
As these encrypted packets arrive at the WAP, they are decrypted for processing. The WAP needs to understand this data to do its job, which includes directing the packets to their proper destination within the local network or out to the internet. Once decrypted, the data packets are sent through the wired portions of the network (the internal LAN), where they are typically no longer encrypted by the Wi-Fi protocol. However, it’s worth noting that sensitive information can still be protected by other layers of encryption, such as those provided by secure websites (HTTPS), VPNs, or end-to-end encrypted services.
The encryption between the laptop and the WAP is crucial because wireless signals can potentially be intercepted by anyone within range. By encrypting this part of the communication, WLANs ensure a level of security and privacy akin to that of wired networks, despite the inherently open nature of wireless communication.
Quick Quiz
Let us examine the common security protocols used to secure Wireless Networks
Wired Equivalent Privacy (WEP)
Wired Equivalent Privacy (WEP) is a security protocol that was designed to provide a wireless local area network (WLAN) with a level of security and privacy comparable to what is usually expected of a wired LAN. It was introduced as part of the original IEEE 802.11 standard in 1997.
The primary aim of WEP was to safeguard wireless communication from eavesdropping and other types of attacks by encrypting data transmitted over the WLAN. WEP uses the stream cipher RC4 for encryption, which was considered strong at the time of WEP’s development.
Rivest Cipher 4 (RC4) is a stream cipher that encrypts data bits sequentially with a key stream. It encrypts data by mapping a pseudo-random key stream to the message’s bits. This key stream is a computer-generated sequence that simulates true randomness, with each bit of the sequence aligning with and encrypting each bit of the original message in a sequential process. The generated pseudo-random stream of bits (a key stream) has to be the same length as the plaintext message. This key-stream is then combined with the plaintext using the bitwise XOR operation to produce the ciphertext.
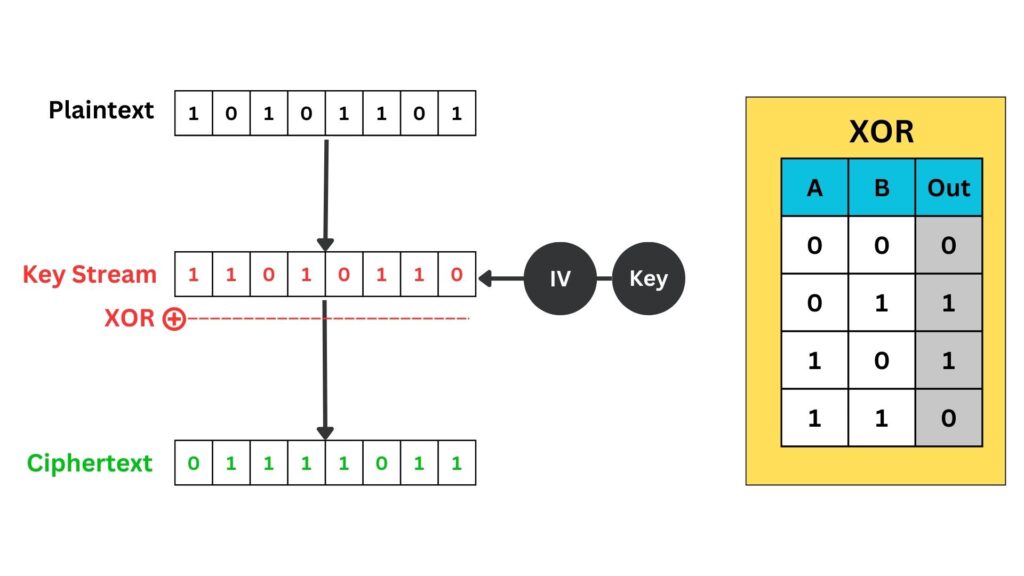
Each ‘1’ or ‘0’ in the key stream is generated pseudo-randomly and aligns with each bit of the plaintext. The XOR operation is then applied bit-by-bit to produce the ciphertext.
When a user connects to a WEP-protected SSID with a password such as “ABC123”, the initial exchange is an authentication and association process. First, the laptop sends an authentication request to the Wireless Access Point (WAP). The WAP replies with a clear-text challenge packet. The laptop then encrypts this challenge text using the RC4 stream cipher, with a key derived from the concatenation of the WEP password and a randomly chosen Initialization Vector (IV). This encrypted challenge is sent back to the WAP along with the IV value which is in clear text and it has to be publically shared. The WAP, which knows the WEP key, decrypts the challenge using the same IV to verify the encryption was successful. If the decrypted challenge matches the original, authentication is successful, and the laptop sends an association request to join the network. Upon approval, the WAP sends an association response, and the laptop is connected to the network, ready to start encrypted data communication using the established WEP key.
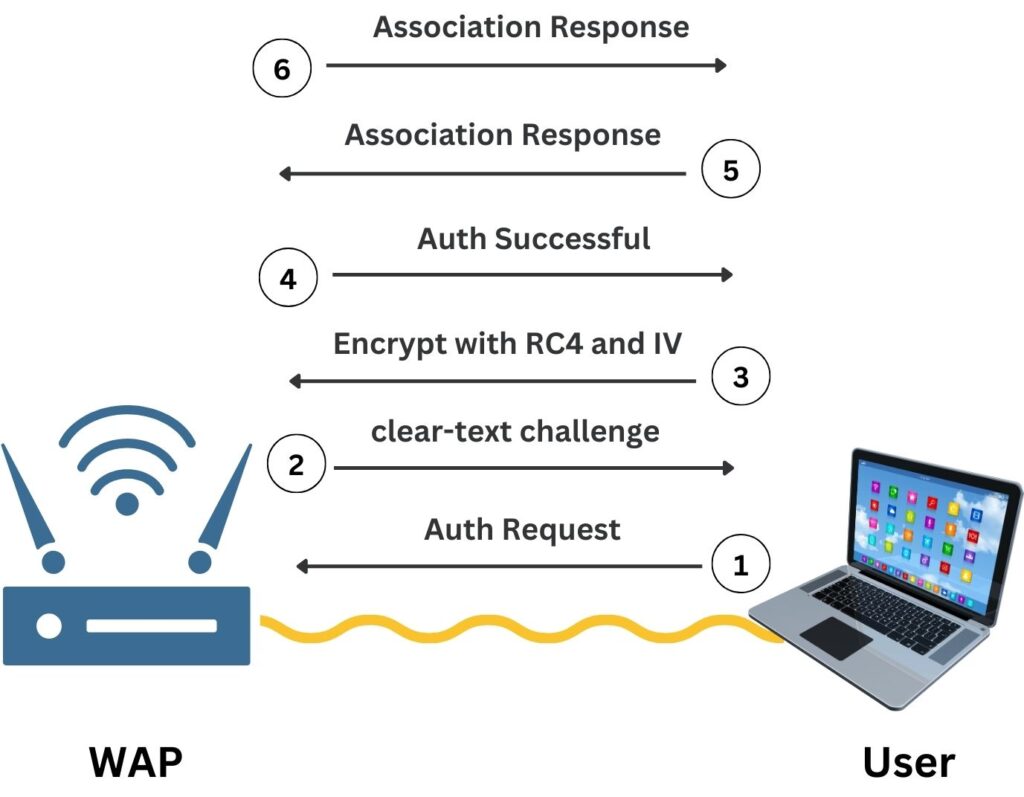
Note that, the purpose of the IV is to introduce randomness into the process so that the same plaintext does not result in the same ciphertext every time, which would be a significant security vulnerability.
The RC4 Input Key is created by appending the secret key to the IV. This concatenated key initializes the RC4 cipher, generating a unique key stream for encrypting data, ensuring that each packet gets a different encryption, even with the same secret key.
Here’s how it breaks down in the RC4 encryption process used by WEP:
- Secret Key: This is the static encryption key that is derived from the password you enter (e.g., “ABC123”). In WEP, this is typically a 40-bit or 104-bit key.
- Initialization Vector (IV): A 24-bit value that changes for each packet to avoid encrypting two packets with the same key. It is transmitted in plain text.
- RC4 Input Key: This is a combination of the IV and the secret key. It is fed into the RC4 algorithm to generate the key stream.
- Key Stream: This is the output of the RC4 algorithm, a pseudo-random sequence used to encrypt the data by XORing it with the plaintext.
The standard WEP encryption key sizes are 64-bit and 128-bit, with 40 and 104 bits being the actual key size, respectively, and the remaining bits reserved for the Initialization Vector (IV) which is a 24-bit value.
A 24-bit initialization vector has 16,777,216 unique values before duplication or collisions.
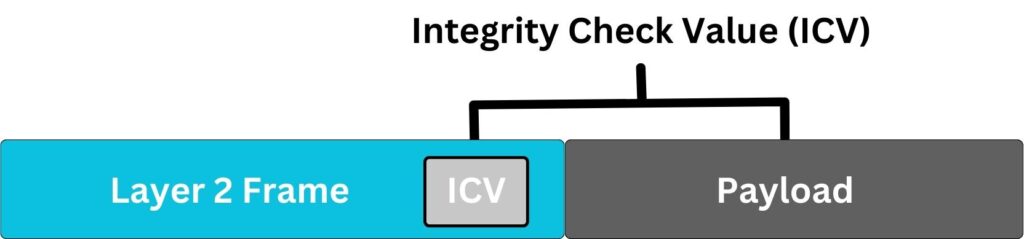
Note that WEP encryption occurs at the Data Link Layer (Layer 2) of the OSI model. When a frame is prepared for transmission, the payload which includes the Layer 3 IP packet is encrypted. The header of the Layer 2 frame remains unencrypted to allow proper forwarding and handling by wireless network devices. Essentially, WEP encapsulates and encrypts the IP packet (Layer 3) and any higher-layer protocols it contains, but the metadata in the frame header, necessary for delivering the frame to the next network device, is sent in clear text.
If you try to capture this traffic in Wireshark, you would see a standard IEEE 802.11 wireless frame with an encrypted data payload. The WEP header, which includes the IV and key index, is visible before the encrypted payload, while the WEP ICV (Integrity Check Value) is appended after the encrypted data.
Why Wired Equivalent Privacy (WEP) become obsolete?
WEP’s reputation as a weak wireless security protocol stems from several inherent design flaws. The protocol relies on a single static key for encryption and authentication, shared among all users on the network. This key, unless regularly changed—which in practice is a cumbersome process, becomes a vulnerability as it is exposed to all users and can be compromised.
The most pronounced flaw in WEP is the small 24-bit space for Initialization Vectors (IVs). This limited range leads to the frequent reuse of IVs, especially in networks with high traffic. The reoccurrence of IVs means that the same encryption key is utilized multiple times, making the network susceptible to statistical attacks as patterns emerge over time. Moreover, some IVs can be used to infer parts of the key because of predictable flaws in the RC4 cipher that WEP employs.
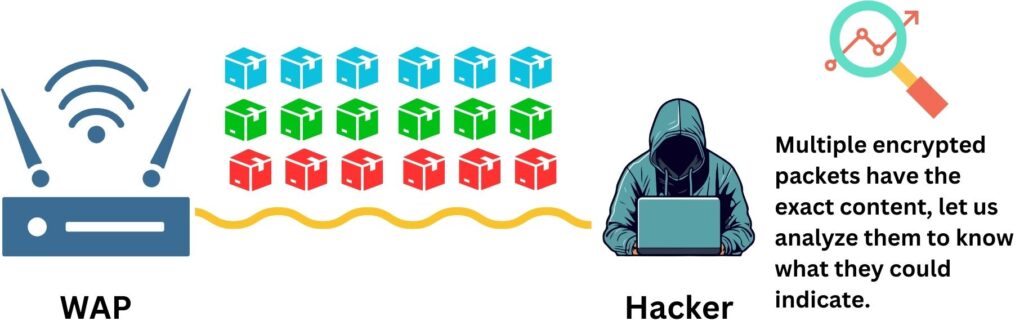
In cryptography, a statistical attack involves analyzing encrypted traffic to find patterns caused by the reuse of initialization vectors (IVs). Since WEP encryption with reused IVs produces patterns, attackers use statistical methods to compare these and deduce the encryption key, exploiting the inherent weaknesses in the WEP protocol.
Furthermore, WEP’s approach to data integrity is fundamentally flawed. It uses the CRC-32 checksum, a method that is not secure against intentional alterations, allowing attackers to modify and retransmit packets with a valid checksum.
Attackers exploit these weaknesses through passive and active means. In passive attacks, they collect WEP-encrypted packets over time, waiting for IVs to repeat. Once enough data is gathered, statistical techniques can reveal the encryption key. The exact number of packets required to crack WEP varies, but due to the weakness in the IV implementation, it can be surprisingly low. On average, with weak IVs, it may take between 20,000 to 40,000 packets to deduce a WEP key with 64-bit encryption, and around 500,000 for 128-bit encryption, though these numbers can be higher or lower depending on the network traffic and the tools used. The cracking process works by capturing a large number of packets and analyzing them for IV collisions, instances where the same IV is used more than once. Remember that IV values are sent in clear text because they are meant to be public. These collisions can be exploited to make educated guesses about the content of the key. Tools like Aircrack-ng implement sophisticated statistical algorithms that compare the intercepted data to derive the key. They look for anomalies and use the flaws in the RC4 cipher combined with the repeated IVs to reduce the number of possibilities for the key until the correct one is found.
In active attacks, attackers inject artificial packets to generate more traffic, which speeds up the process of collecting data. With sufficient data, attackers can use dictionary attacks with precomputed tables to crack the encryption key.
The cumulative effect of these vulnerabilities is that with enough data and some analysis, the WEP key can be cracked in a matter of minutes using readily available tools. This alarming weakness led to the introduction of more secure protocols like WPA and WPA2, which addressed these issues with improved key management protocols and stronger encryption methods, providing a much more robust defense against the types of attacks that so easily defeated WEP.
Before moving to the next wireless security protocol, let us recap the fundamental flaws in WEP design:
- Static Key Usage: WEP uses a single static key for both encryption and authentication, shared among all users on the network. This key must be manually updated to maintain security, which is impractical and often neglected.
- Initialization Vector (IV) Reuse: WEP’s IV space is small (24 bits), leading to the rapid reuse of the same IV. With enough traffic, IV collisions occur, meaning the same encryption key is used more than once.
- Flawed IV Implementation: Certain IV combinations can reveal information about the key due to weak cryptographic practices in RC4, making some packets more vulnerable.
- Lack of Key Management: WEP does not provide a method for safe key distribution or dynamic key changes, leaving the static keys vulnerable to exposure.
- Predictable IVs: WEP’s IV generation is predictable, allowing attackers to collect IVs more efficiently.
- Weak Integrity Checks: WEP uses the CRC-32 checksum for data integrity, which is not cryptographically strong and can be manipulated by attackers.
Attackers exploit these vulnerabilities using several methods:
- Passive Attacks: By passively capturing traffic, attackers can wait for IV collisions and use statistical attacks to deduce the key.
- Active Attacks: Attackers inject packets into the network to generate traffic, which speeds up the capture of vulnerable IVs.
- Dictionary Attacks: After collecting enough packets, attackers can use precomputed databases (rainbow tables) of IVs to find keys.
In summary, while WEP was pioneering in offering encryption for WLANs, its numerous security issues quickly made it obsolete in practice. The static nature of its keys, weak IVs, and the vulnerabilities to multiple forms of attack mean that WEP cannot provide a level of security sufficient for today’s wireless networks. Its use today is strongly discouraged, and it has been superseded by more secure protocols like WPA and WPA2.
Wi-Fi Protected Access (WPA)
In response to the significant security vulnerabilities discovered in Wired Equivalent Privacy (WEP), Wi-Fi Protected Access (WPA) was introduced in 2003 by the Wi-Fi Alliance as a stopgap solution to enhance wireless network security.
WPA was invented to address the immediate security issues of WEP without requiring a complete overhaul of the existing hardware. It was part of an effort to strengthen the encryption and authentication features of wireless networks while manufacturers worked on a more secure and robust solution, which would eventually become WPA2.
WPA improved upon WEP’s weak points through several key enhancements:
- Improved Data Encryption:
Temporal Key Integrity Protocol (TKIP) was introduced with WPA as a stopgap security protocol in the wake of the WEP vulnerabilities. TKIP is an encryption protocol that was designed to provide more secure encryption than WEP without requiring the replacement of legacy hardware. It works by generating a unique 128-bit key for each packet. This key is derived from mixing multiple factors, TKIP uses a combination of the root key (or base key), the IV, and the MAC address to produce what’s known as the “per-packet key”. Here’s a breakdown of how it works:
- IV (Initialization Vector): TKIP uses a 48-bit IV, which is much larger than WEP’s 24-bit IV, making the key space larger and reducing the chance of IV reuse (281,474,976,710,656 unique values).
- MAC Address: The MAC address of the sending network card is included in the key mixing function to add an additional layer of uniqueness to the key.
- Root Key (Encryption Key): This is the pre-shared key or the key derived from the 802.1X authentication process.
- Key Mixing Function: TKIP combines these elements (IV + MAC + Root Key) using a key mixing function to produce a unique 128-bit per-packet key for each packet.
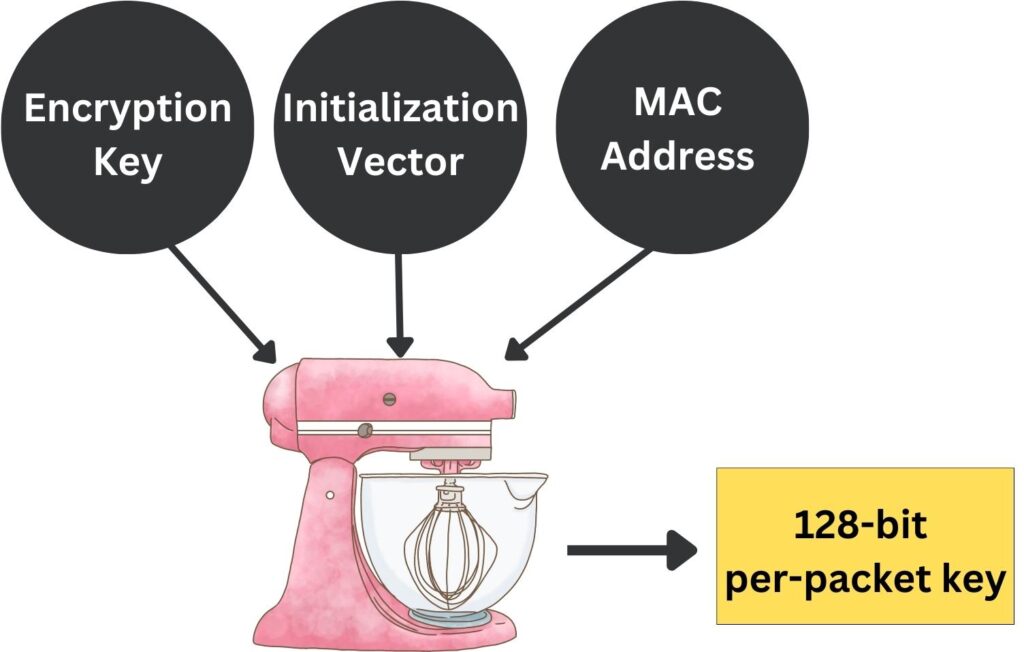
This per-packet key is then used to encrypt the data payload of the packet with RC4, similar to how WEP uses RC4, but with significant differences in key generation that make TKIP more secure and difficult to predict patterns in encrypted packets than WEP. The frequent change in the encryption key, along with the added complexity in key generation, makes TKIP resistant to the statistical attacks that compromised WEP. However, because TKIP still uses the RC4 cipher, which itself has vulnerabilities, it was eventually succeeded by AES-based encryption in WPA2.
Furthermore, TKIP implements a sequence counter to protect against replay attacks, where an attacker might try to resend a captured packet, and a 64-bit Message Integrity Check (MIC), named Michael, to protect against tampering. While TKIP was a significant improvement over WEP, it has since been superseded by more secure encryption protocols like those used in WPA2 and WPA3, as it was eventually found to have vulnerabilities of its own.
- Stronger Integrity Checks:
A Message Integrity Check (MIC), known as Michael, was introduced to prevent attackers from altering and resending data packets (Replay Attack). This feature helps mitigate one form of man-in-the-middle attacks.
We mentioned WEP using Integrity Check Value (ICV) which is a simple Cyclic Redundancy Check (CRC32) that’s computed on the plaintext data and then appended to the frame before encryption. CRC is a straightforward algorithm used to detect accidental changes to raw data. However, CRC32 is not cryptographically secure. It doesn’t protect against intentional tampering with the data because an attacker can alter the data and then recalculate and replace the ICV to match the changes, making the modifications undetectable.
In contrast, WPA’s Message Integrity Check (MIC), is designed to prevent both accidental data corruption and intentional tampering. MIC uses a stronger algorithm than CRC32, adding security by checking the integrity and authenticity of the packets. MIC involves the encryption key while computing the integrity value, this means in the wireless network the sender uses the encryption key to calculate the integrity value, and the receiver likewise uses it to verify the packet integrity. If the MIC fails, it indicates that the packet was tampered with or corrupted and should be discarded. WPA’s MIC also includes a countermeasure against replay attacks by implementing a sequence number that must always increase, making it significantly more secure than WEP’s ICV. For example, in a WPA-protected network, tampering with a packet’s contents would invalidate the MIC, as the attacker would not be able to compute the correct MIC without knowing the secret key. This would result in the packet being rejected by the receiving station.
- Enhanced Authentication Protocols:
WPA’s support for Extensible Authentication Protocol (EAP) marks a significant advancement over WEP’s limited authentication mechanisms. EAP facilitates a variety of sophisticated authentication methods that can operate within the framework of a RADIUS server, allowing for dynamic and centralized management of user credentials and keys. This is particularly vital in enterprise settings, where security demands go beyond simple pre-shared keys and necessitate a robust, scalable authentication infrastructure. By using EAP, WPA is able to leverage a RADIUS server to authenticate users individually, which not only enhances security through better key management but also provides detailed accounting and audit capabilities. WEP, with its static key approach, lacks this level of flexibility and security, making WPA’s integration of EAP a crucial development for enterprises that require stringent access controls and the ability to enforce complex security policies across their wireless networks.
Extensible Authentication Protocol (EAP) is a framework widely used in wireless networks and Point-to-Point connections. It provides a standard mechanism for supporting various authentication methods, such as passwords, tokens, and certificates, to secure network access and enable flexible authentication upon which additional authentication protocols can be built.
- Pre-shared Key (PSK) for Home Users:
For home users, WPA could be configured easily with a pre-shared key (WPA-PSK), simplifying the setup process compared to the complex key management WEP required.
If you have tried to configure Wi-Fi Protected Access (WPA), you must have noticed that there are two options WPA-Enterprise and WPA-Personal.
They refer to two different modes of WPA security tailored to different environments. WPA-Personal, also known as WPA-PSK (Pre-Shared Key), is designed for home and small office networks and uses a shared key to authenticate devices. This mode is easier to set up but less secure because all devices use the same key. On the other hand, WPA-Enterprise is intended for larger organizations and provides a higher level of security by using an authentication server (such as RADIUS) to authenticate each user individually. This means that each user has unique credentials, which enhances security by making the system less vulnerable to unauthorized access if a single set of credentials is compromised. WPA-Enterprise also offers additional management and control capabilities crucial for organizations managing a large number of users with varying access needs.
The implementation of WPA did not typically require new hardware, which was a significant advantage for consumers and businesses that had already invested in Wi-Fi technology. Most existing equipment could be updated to WPA with firmware updates provided by manufacturers.
While WPA was a significant improvement over WEP, it was not without its vulnerabilities. Temporal Key Integrity Protocol (TKIP) was introduced with WPA as an interim security protocol while the more secure Advanced Encryption Standard (AES) was being prepared for future use in WPA2. TKIP was essentially a patch to improve upon WEP’s encryption without requiring new hardware. However, TKIP inherited some limitations due to its design. For instance, researchers discovered that the way TKIP mixed encryption keys could be vulnerable to sophisticated statistical attacks. If an attacker collected a sufficient amount of data packets encrypted with the same key, they could perform analysis to uncover patterns and eventually deduce the encryption key. One notable exploit, named the “Beck-Tews attack” could partially crack TKIP by using this method to inject arbitrary packets, although it couldn’t decrypt the data. This vulnerability was significant enough that TKIP is no longer considered secure, leading to its deprecation in favor of stronger encryption protocols. Additionally, the use of PSK in WPA made it susceptible to brute force attacks if a weak passphrase was chosen.
So to sum up, WPA represented an essential step forward in wireless security at a time when WEP’s flaws had become a substantial concern. It provided stronger encryption and better user authentication, which were critical in maintaining users’ trust in wireless networks. WPA allowed the Wi-Fi industry to maintain security standards while developing the more secure and sophisticated WPA2 protocol, which eventually replaced WPA due to its stronger security measures. Despite its limitations, WPA was crucial in the transition from the flawed WEP to the more secure protocols we rely on today.
Wi-Fi Protected Access 2 (WPA2)
Wi-Fi Protected Access 2 (WPA2) is the second generation of WPA security protocol and the successor to the original Wi-Fi Protected Access (WPA) standard. Officially ratified by the IEEE as 802.11i in 2004, WPA2 enhances Wi-Fi security by providing a more robust method of encrypting data on wireless networks.
WPA2 was developed to address the security shortcomings of its predecessor, WPA, which was only a temporary solution to the problems with WEP. Although WPA improved wireless security, its reliance on the Temporal Key Integrity Protocol (TKIP) left it vulnerable to certain types of attacks. WPA2 emerged to establish a more secure encryption method that could withstand the advances in attack techniques and computing power that exposed vulnerabilities in WPA.
Here are some of the advanced attack techniques and computing power issues that contributed to WPA becoming less secure over time:
- TKIP Shortcomings: TKIP, used in WPA, was susceptible to cryptographic attacks due to its relatively small Initialization Vector (IV) space and key reuse.
- Brute-Force Attacks: Improved computing power made it feasible to attempt brute-force attacks on WPA’s pre-shared keys, especially if the keys were not complex enough.
- Key Recovery Attacks: Techniques that exploited weak keys or the predictable way that keys were generated in TKIP made key recovery possible.
- Injection Attacks: Vulnerabilities in TKIP allowed for packet injection, where an attacker could send unauthorized packets to a network client.
- Dictionary Attacks: The use of common or simple passwords led to the success of dictionary attacks against WPA-PSK.
- Deauthentication Attacks: Sending disassociate packets could disrupt communications, allowing for potential session hijacking or brute-force attacks when the user reconnects.
How did WPA2 address these security challenges:
- Advanced Encryption Standard (AES):
WPA2 mandates the use of AES (Advanced Encryption Standard), a more secure and sophisticated encryption algorithm, to replace TKIP. AES is a symmetric block cipher chosen by the U.S. government for securing classified information and is widely used across the globe for its robustness and efficiency. In the context of WPA2, AES replaces TKIP to provide stronger data protection. It encrypts data in fixed-size blocks (128 bits) using cryptographic keys of 128, 192, or 256 bits in length, far exceeding the security that TKIP offered. AES’s strength lies in its multiple rounds of data scrambling, which effectively shields against attacks that exploited vulnerabilities in WEP and TKIP. When implemented in WPA2, AES works with the Counter Mode with Cipher Block Chaining Message Authentication Code Protocol (CCMP) replacing the Michael Message Integrity Check (used in WPA) to not only encrypt wireless data but also provide stronger data integrity and authentication, offering a comprehensive security framework that effectively secures modern wireless networks.
- Enhanced Key Management:
WPA did include key management, but it was less sophisticated and less secure. WPA2 introduced an improved key management system with the 4-way handshake and the use of AES, offering stronger security and a more dynamic method of distributing and managing the encryption keys.
Key Management in cryptography refers to the processes and protocols by which cryptographic keys are generated, distributed, stored, used, and replaced. Its purpose is to maintain key security and integrity, ensuring that only authorized users can access the encrypted network communication.
The password entered by the user to connect to an SSID is known as a pre-shared key (PSK). This PSK is used during the initial authentication process to establish a connection between the device and the network. Once authenticated, the 4-way handshake process generates a new, unique set of encryption keys used for securing the actual data transmission. These keys are different from the PSK and are dynamically generated to encrypt the communication between the user’s device and the wireless access point (WPA), providing a fresh encryption for each session.
Security protocols like WPA2 safeguard the encryption keys by executing a secure 4-way handshake that creates unique session keys, which are never actually disclosed over the network. This handshake is protected using a master key derived from the user’s password, ensuring that the key exchange process is encrypted. The combination of the master key with securely exchanged nonces during the handshake results in the derivation of these strong, unique keys. Moreover, the temporal nature of these session-specific keys, which change with each user session, further reduces any risk of exposure. All of this complex key management occurs seamlessly in the background, without any visibility to the end user, ensuring that only the authenticated device and the access point know the active encryption keys.
The 4-way handshake in WPA2 key management ensures that both the client and Wireless Access Point (WPA) have the correct credentials and establish a fresh encryption key. When the client attempts to connect to the wireless network through a WPA and inserts the SSID password, get authenticated, the following process occurs to generate the encryption keys:
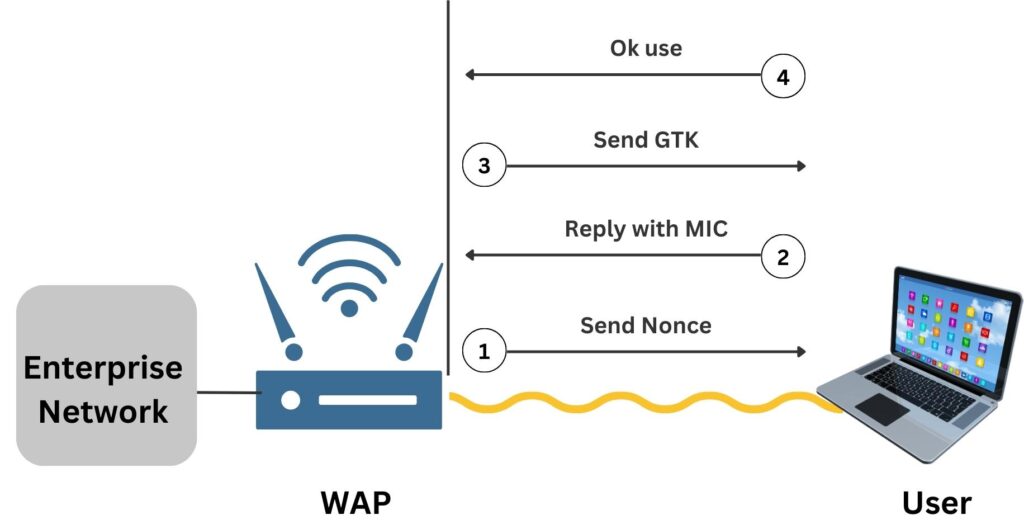
- The WPA sends a nonce (a number used once) to the client, starting the handshake.
- The client responds with its own nonce and a Message Integrity Check (MIC), confirming it has the correct password.
Note: in WPA2, MIC is part of the CCMP used in the AES encryption algorithm. WPA also uses MIC but with the Michael algorithm as part of TKIP suite - The WPA sends back the Group Temporal Key (GTK) and a sequence number for the client to use, encrypted with the established key.
- The client acknowledges the GTK and confirms to the WPA that it is ready to start secured communication.
It is worth noting that if a laptop maintains a connection to a WAP for a week without interruption, it will still use multiple encryption keys. WPA2 is designed to periodically refresh encryption keys through a process called “Rekeying“. This happens automatically at set intervals to enhance security, even within a single, uninterrupted session. So, while the session remains the same, WPA2 ensures that the encryption keys are regularly updated behind the scenes to protect against potential vulnerabilities, such as key cracking attempts over time. In WPA2, the key management process does not have a standard or default rekeying interval. Instead, the rekeying interval is configurable and can be set by the network administrator based on the network’s security requirements. Typically, it’s adjusted to balance between performance and security needs.
- Backward Compatibility:
While WPA2 introduced new security measures, it maintained backward compatibility with WPA, meaning that devices capable of WPA could be updated to WPA2 through firmware updates, though they would not benefit from the enhanced security features of WPA2 when operating in WPA mode. The access point can be configured to support both WPA2 and WPA, allowing devices that only support WPA to connect using the older security protocol.
- Prevention of Pre-shared Key (PSK) Guessing:
WPA2-PSK (Pre-Shared Key) mode incorporates improved key management that, along with AES encryption, provides significant resistance to brute-force attacks. AES is a computationally complex cipher with a large key space, especially with keys of 128 bits or more, making it incredibly difficult to crack through brute force. The key itself undergoes a series of transformations that expand it into numerous round keys, further complicating any attack. As a result, attempting to decrypt WPA2-PSK traffic by guessing the key is impractical due to the time and computational power required, thereby enhancing the security of wireless networks over the previous WPA-PSK standard.
- Required for Wi-Fi Certification:
The Wi-Fi Alliance made WPA2 certification mandatory for all new devices wanting to use the Wi-Fi trademark, ensuring that WPA2’s security features would be universally adopted within all compliant wireless devices.
WPA2 represents a significant advance in wireless network security. By incorporating AES, WPA2 delivers a level of security that meets the requirements for government and business applications. It addressed the vulnerabilities found in WPA by introducing more secure encryption and authentication methods, thus setting a new standard for wireless network security. While no system can be completely immune to security threats, WPA2 has stood the test of time and remains a reliable security protocol for protecting wireless networks, until the introduction of WPA3, which aims to provide even stronger protections.
Wi-Fi Protected Access 3 (WPA3)
Wi-Fi Protected Access 3 (WPA3) is the latest security protocol for wireless networks, introduced in 2018 by the Wi-Fi Alliance. As the successor to WPA2, WPA3 was developed to address emerging security challenges and provide enhanced protection for Wi-Fi users.
WPA3 was invented to counteract the evolving security threats that had begun to challenge the robustness of WPA2, particularly in the face of increasing computing power and sophisticated attack techniques. Despite WPA2’s effectiveness, vulnerabilities such as KRACK (Key Reinstallation Attack) exposed weaknesses in its protocol, necessitating a more secure and future-proof alternative.
WPA3 was introduced to address several security challenges and limitations inherent in WPA2. These challenges include:
- Vulnerability to Offline Dictionary Attacks: WPA2-PSK was susceptible to offline brute-force attacks. If attackers captured the WPA2 handshake, they could try to crack the pre-shared key offline by testing possible passwords against the captured data.
- Weak Passwords: WPA2’s security was significantly reduced with weak, easily guessable passwords, making it vulnerable to dictionary attacks. We will see how WPA3 addressed this issue using Simultaneous Authentication of Equals (SAE).
- KRACK (Key Reinstallation Attack): a vulnerability in the WPA2 protocol that allows attackers to intercept and decrypt Wi-Fi traffic. It exploits weaknesses in the WPA2’s 4-way handshake, a process used to establish a key for encrypting traffic. By manipulating and replaying the cryptographic handshake messages, attackers can trick a victim into reinstalling an already-in-use key. This reinstallation resets the encryption key’s nonce and replay counter, allowing the attacker to replay, decrypt, or forge packets. This vulnerability doesn’t expose the Wi-Fi password itself, but it enables attackers to eavesdrop on the traffic between the device and the wireless access point, potentially accessing sensitive data.
- Lack of Forward Secrecy: In WPA2, if an attacker managed to crack the network’s encryption key, they could decrypt all historical traffic they had captured.
- Weak Initial Key Exchange: WPA2’s initial key exchange mechanism was not as strong as it could be, making it more vulnerable to certain types of attacks.
- Lack of Protection for Public Networks: WPA2 did not offer specific protections for users on public Wi-Fi networks. These networks often use WPA2-Personal (with a shared password) or no encryption, leaving users vulnerable to various attacks, such as eavesdropping or man-in-the-middle attacks. Public networks needed a way to provide individualized encryption to each user, something WPA2 did not inherently support.
- Insecure IoT Devices: The proliferation of IoT devices introduced new challenges. Many IoT devices have limited processing capabilities and cannot handle the computational requirements of robust security protocols. As a result, they often rely on weaker security settings or outdated protocols, making them a soft target for attackers. WPA2, being a bit older, did not address the unique security needs of IoT devices, which often require lightweight yet secure protocols.
WPA3 acknowledges and addresses all these security concerns in WPA2:
- Enhanced Encryption:
WPA3 utilizes 192-bit encryption in its enterprise version, a significant step up from the 128-bit encryption in WPA2, offering stronger protection against brute-force attacks.
How does AES key length help if the SSID password is cracked?
The key point here is that the strength of the SSID password and the AES key length serve different purposes. If an attacker cracks the SSID password like “Summer123” they gain network access. However, the AES key length (128-bit in WPA2, 192-bit in WPA3 Enterprise) refers to the complexity of the actual encryption used for data transmission, not the password itself. A longer key length (192-bit) means that even if an attacker has the SSID password, deciphering the encrypted data directly is significantly harder due to the increased complexity of the encryption algorithm.
- Improved Public Wi-Fi Security:
WPA3 introduces Wi-Fi Enhanced Open, a feature that enhances security on public Wi-Fi networks that are not protected with passwords. With this feature, even without a password, data transmitted over such networks is automatically encrypted on a per-user basis. This means each user’s connection is uniquely protected, significantly reducing the risk of eavesdropping or data interception, a common concern in open, unsecured Wi-Fi environments.
The mechanism uses Opportunistic Wireless Encryption (OWE), which provides individualized encryption for each user. The access point and user device automatically negotiate the encryption keys during the connection process, ensuring a unique, encrypted link for each user.
- Robust Protection Against Brute-Force Attacks:
WPA3 enhances security against brute-force attacks through Simultaneous Authentication of Equals (SAE). Unlike WPA2’s Pre-Shared Key (PSK) method, SAE creates a more complex interaction between the device and the wireless access points during the authentication process. This complexity makes it much harder for attackers to guess the network password using offline dictionary attacks, as each attempt requires direct interaction with the network, significantly increasing the effort and time needed to potentially compromise the network.
In WPA3, SAE uses a method named Dragonfly Key Exchange to enhance security. Imagine two parties, like a phone and a Wi-Fi router, wanting to establish a secure connection. Each of them creates a secret code without telling the other. Then, they exchange a sort of “promise” or “commitment” (as a public value) about their secret codes. They don’t share the actual secrets yet, just a clue or proof that they have them. Next, they check each other’s clues through a complex cryptographic process to make sure they are legitimate. Then, each device uses its secret and the other’s public value to compute a shared key. If both computations match, it confirms that the exchanged clues are legitimate.
How Does SAE Solve The Man-in-the-Middle Problem?
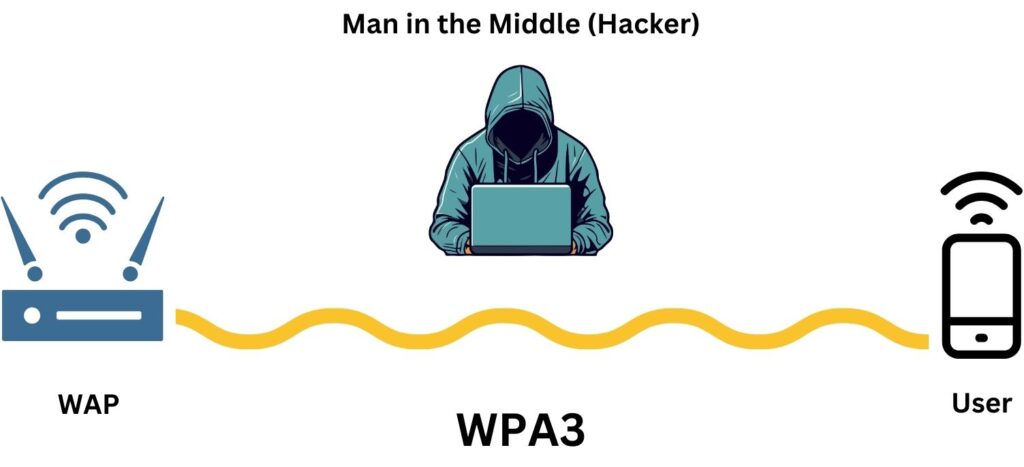
If a hacker intercepts the public values in WPA3’s SAE and replaces them with their own, the devices (phone and router) would end up using the hacker’s values to compute the shared key. However, since the hacker doesn’t have the original secrets of the devices, they can’t correctly compute the shared key. This mismatch in the key computation would alert the devices that something is wrong, preventing a successful connection and maintaining security.
The solution to the man-in-the-middle attack in WPA3’s SAE lies in its unique commit-exchange mechanism and cryptographic safeguards. Here’s how it addresses the MitM problem:
- Commitment Exchange: In SAE, the exchange isn’t just about public values. Each device sends a “commitment” which includes the public value and additional cryptographic data (e.g. SSID password, scalar and element values). This makes it difficult for a hacker to simply replace these values without being detected.
- Cryptographic Validation: After the exchange, each device performs cryptographic checks to validate the commitment from the other device. This involves using their private secrets and the received public data to perform specific calculations.
- Detection of Tampering: If a hacker replaces the public values, the cryptographic validation fails because the calculations won’t match up. The hacker won’t have the correct private secrets to create valid commitments that pass the validation checks.
- Security Reinforcement: SAE also uses a password-based key derivation function, which further secures the process against brute-force attacks, making it hard for a hacker to guess the passwords or secrets involved.
This system enhances security by requiring a hacker to actively engage with a real device, such as a router or phone, for each password guess. This approach renders offline brute-force attacks impossible, transforming them into a slower, online process. By necessitating direct interaction with the hardware for every attempt and incorporating rate-limiting mechanisms, the system effectively thwarts brute-force attacks, making them impractical and far more time-consuming. This significant shift in the attack process substantially increases protection against such threats.
The process in WPA3’s SAE is somewhat reminiscent of Diffie-Hellman. Both involve parties exchanging public values derived from private secrets to securely compute a shared key, without the need to directly exchange the secret keys themselves.
Homework: in a public WIFI network like airports, hotels, events, etc, both the user and the hacker know the SSID password, how does WPA3 SAE prevent the hacker from being man-in-the-middle between the user’s device and the WIFI Access Point (meaning the hacker is conducting two parallel handshakes)?


- Forward Secrecy:
Forward secrecy, as implemented in WPA3, is a crucial security feature that protects past network sessions from being compromised, even if the network password is later cracked or exposed. This is achieved by ensuring that each session uses a unique set of encryption keys that are not derived from the main network password and are not reused in future sessions. When a device connects to a WPA3-secured network, the encryption keys used for that session are generated during the initial handshake process in a way that they depend on some randomly chosen values that are unique to that session. These keys are used to encrypt and decrypt the data transmitted during that particular session. Once the session ends, the keys are discarded.
If an attacker were to discover the network password at a later time, they could not use it to retroactively decrypt previously captured traffic from past sessions because those sessions used different, independently generated keys. This feature significantly enhances data privacy and security, as it protects historical data transmissions from being decrypted and accessed by unauthorized parties.
- Protection Against KRACK:
In WPA2, during the 4-way handshake, a unique encryption key (the session key) is established between the client device and the access point (AP). However, if an attacker could manipulate and replay certain handshake messages, they could force the reinstallation of an already-in-use encryption key on the client device. This reinstallation resets certain parameters (like the nonce and replay counters) associated with the key, potentially allowing the attacker to decrypt, replay, or forge packets.
WPA3 counters this by modifying the handshake process, ensuring that the key installation is secure and resistant to such replay attacks. It introduces new protocols and checks that prevent the reinstallation of encryption keys, thereby mitigating the risk associated with KRACK. With these enhancements, even if an attacker captures and replays handshake messages, they cannot force key reinstallation to decrypt or manipulate the data.
For more information, please refer to the Simultaneous Authentication of Equals (SAE) and Dragonfly Key Exchange we discussed previously.
- Easy Connect Feature:
WPA3’s Easy Connect feature simplifies the connection process for devices with limited or no user interface, like smart home appliances. Instead of manually entering a password, users can connect these devices to their Wi-Fi network by scanning a QR code. When you scan the QR code with a smartphone or tablet, it automatically communicates the network credentials and security settings to the device. This method is not only user-friendly but also maintains high security standards set by WPA3. It eliminates the common security risks associated with manually entering passwords on devices that lack a proper interface, ensuring a secure and effortless setup for a wide range of smart devices.
WPA3 adoption is steadily increasing but has not entirely replaced WPA2. The gradual transition is partly due to the need for both hardware and software upgrades to support WPA3. Newer devices and network equipment are increasingly supporting WPA3, and its usage is expected to grow as older devices are phased out and security standards become more stringent. However, the full potential of WPA3 is often realized in environments that prioritize security, such as government and corporate settings, where the latest security protocols are a necessity. Public Wi-Fi networks are also benefiting from the enhanced security features of WPA3, especially with the encryption of open networks.
Quick Quiz
WEP vs WPA vs WPA2 vs WPA3
Before diving into the comparison table, it’s important to understand how Wi-Fi security has evolved. Each protocol, from WEP to WPA3, represents a significant step in improving wireless network security. This table will help you see the advancements in encryption, authentication, and overall security across different Wi-Fi security standards.
| Criteria | WEP | WPA | WPA2 | WPA3 |
|---|---|---|---|---|
| Definition | Initial security protocol for wireless networks. | Enhanced protocol to address WEP's flaws. | Further advanced security protocol standard. | The latest and most secure protocol for wireless networks. |
| IEEE Standard | 802.11 (original) | 802.11i (draft), modified 802.11 | 802.11i, full standardization | 802.11ax, with enhanced security features |
| Year | 1997 | 2003 | 2004 | 2018 |
| Encryption Algorithm | RC4 stream cipher | TKIP (Temporal Key Integrity Protocol), an improvement over RC4 | AES (Advanced Encryption Standard), a significant step up | AES, with increased key size and stronger encryption in Enterprise mode |
| Encryption Key Size | 40-bit and 104-bit (with 24-bit reserved for IV) | 128-bit TKIP keys | 128-bit keys for AES | 128-bit standard, 192-bit in Enterprise mode |
| Key Management Process | Manual setup with static keys | Dynamic key generation with 4-way handshake using TKIP | Enhanced 4-way handshake with AES, more secure key generation | Simultaneous Authentication of Equals (SAE) for more secure key establishment |
| Authentication Methods | Open System (no authentication), Shared Key Authentication | EAP (Extensible Authentication Protocol) for enterprise, PSK for personal | Same as WPA, with stronger encryption using AES | Continued use of EAP for enterprise, PSK for personal, with increased protection |
| Vulnerabilities | Weak encryption, IV collisions, easily crackable | Vulnerable to MIC attacks, some weaknesses in TKIP | Susceptible to KRACK, weaker PSK security | Significantly reduced vulnerabilities, addresses previous protocol weaknesses |
| Backward Compatibility | None, as it was the first protocol | Limited compatibility with WEP devices | Broad compatibility with WEP and WPA devices | Limited, mainly compatible with WPA2 devices |
| Resistance to MITM Attack | Low due to weak encryption mechanisms | Improved with TKIP, but still moderate | High, with AES providing better security against such attacks | Very high, with SAE and new encryption methods providing robust protection |
The Security Role of Wireless Controller
In enterprise wireless networks, a wireless controller plays a critical role in managing and securing wireless access points (WAPs) and their associated client devices. While wireless controllers have various functions like load balancing, AP management, and user authentication, their role in cybersecurity is particularly very important.
- Centralized Security Management:
Wireless controllers enable centralized management of security policies across all connected WAPs. This means administrators can implement uniform security configurations, updates, and patches from a single point, ensuring consistent security across the entire wireless network.
- Advanced Encryption and Authentication:
Controllers manage the encryption and authentication protocols used by the WAPs. They ensure that the latest and most secure encryption standards, like WPA3, are employed. This central management of encryption helps in maintaining a robust security posture against unauthorized access and eavesdropping.
- Intrusion Prevention and Detection:
Many wireless controllers are equipped with intrusion detection and prevention systems (IDS/IPS). These systems continuously monitor the wireless spectrum for unauthorized access points (rogue APs), unauthorized devices, or suspicious activities, alerting administrators to potential security threats.
- Network Access Control (NAC):
Controllers often integrate with NAC solutions to enforce access policies. They can allow or deny network access based on user credentials, device type, and compliance with security policies. This level of control is crucial in preventing unauthorized access and containing potential breaches.
- Guest Access Management:
In managing guest access, controllers segregate guest traffic from the main network, providing internet access while keeping the core enterprise network secure. This segregation is key in mitigating risks posed by external devices.
- Traffic Inspection and Analysis:
Wireless controllers can aggregate all of the WAPs logs, and inspect and analyze network traffic for threats or anomalies. They can identify potential security breaches by analyzing patterns and behaviors, which is essential in a landscape where threats are constantly evolving.
- Automated Responses:
On detecting security threats, controllers can automatically take actions like disconnecting or blocking devices, or alerting network administrators. This automation enhances the network’s ability to respond quickly to threats.
Wireless controller is a linchpin in the cybersecurity framework of modern wireless networks. Its ability to centrally manage, monitor, and respond to security threats makes it indispensable in protecting against a wide array of cyber risks. Understanding the multifaceted role of wireless controllers is key. They not only provide a technical solution but also a strategic approach to securing wireless networks, which are an integral part of today’s interconnected world. As technology evolves and wireless networks become more complex, the role of the wireless controller in cybersecurity will continue to grow, adapting to new challenges and threats.
Summary
Our journey began with an exploration of Wi-Fi, a key component of wireless networking. We understood that Wi-Fi is one of many wireless technologies, sitting alongside others like Bluetooth, Cellular Networks (3G/4G/5G), NFC, and more. Each of these serves a unique purpose in the vast landscape of wireless communication. Wi-Fi, in particular, has become integral to our daily lives, providing internet access without the constraints of physical wires. We explored how Wi-Fi uses radio waves to transmit data, making it a flexible and widely accessible means of communication, making it the backbone of Wi-Fi networking.
Since radio waves propagate in all directions and can be received by any device within range, this characteristic underpins the necessity for robust encryption in Wi-Fi networks. Without encryption, sensitive data transmitted over these waves would be vulnerable to interception by unauthorized users or hackers. Thus, the encryption between Wireless Access Points (WAPs) and user devices isn’t just an option; it’s a mandatory aspect of securing wireless communication.
Moving forward, we focused on Wireless Local Area Networks (WLAN) and their architecture. In this context, we highlighted the role of various components like Wireless Controllers, Access Points, and Authentication Servers. A typical enterprise WLAN architecture involves these elements working in unison to provide both seamless connectivity and security. The Wireless Controller, especially, plays a pivotal role in managing the network, ensuring efficient operation and enhanced security.
Our discussion advanced to the core of wireless security, the evolution of security protocols from WEP to WPA3. Each protocol was dissected to understand its strengths and vulnerabilities. WEP, once a pioneering standard, fell short due to its weak encryption, paving the way for WPA. WPA improved security but was eventually succeeded by WPA2, which brought in stronger encryption and better key management. Most recently, WPA3 has set new benchmarks in wireless security with features like enhanced encryption, resistance to brute-force attacks, and improved public Wi-Fi security. These protocols reflect the ongoing efforts to fortify wireless networks against evolving cyber threats.
Homework
- Research the Simultaneous Authentication of Equals (SAE) handshake used in WPA3. Explain its process and how it enhances security compared to previous handshake mechanisms.
- Set up a wireless network and configure it with different security protocols (WEP, WPA, WPA2, and WPA3). Document the steps and any differences you notice in the setup process.
- Investigate why security protocols like SAE and Dragonfly Key Exchange in WPA3 are not used as replacements for digital certificates. Discuss the role of Certificate Authorities and their importance in network security.
- Conduct a practical experiment to understand how Wi-Fi radio waves propagate. Use a Wi-Fi analyzer app to map the signal strength in various locations around a WAP.
- Assess the security measures in place in a public Wi-Fi network, such as in a cafe or library. Evaluate the risks and suggest improvements based on WPA3 features.
- Set up a Wi-Fi network with various protocols (WEP, WPA, WPA2, WPA3) and use network tools (like Wireshark and Airmon-ng) to observe and analyze the key management process for each.
If you learned something new today, help us to share it to reach others seeking knowledge.
If you have any queries or concerns, please drop them in the comment section below. We strive to respond promptly and address your questions.
Thank You









