Table of Contents

Welcome to the unseen war of the digital world, a place where safety and danger coexist in the form of codes and clicks. Every day, we interact with technology that simplifies our lives, yet beneath this convenience lurks the shadow of malware or malicious software designed to harm and disrupt.
Do you know that one of the first recorded pieces of malware was the Brain virus, which appeared in 1986, not to destroy, but as a prank?
It spread from floppy disk to floppy disk, subtly marking its presence. This historical anecdote marks the beginning of what is now a global concern in the age of the internet.
In this lesson, we dive into the world of malware. We will uncover what it is, why it concerns everyone who uses technology, and how it has become a sophisticated tool in the arsenal of cybercriminals. Through an engaging case study, we will see how these digital threats are not just launched but are crafted to breach defenses in a multi-stage attack.
Our discussion will also equip you with the understanding of anti-malware measures, the frontline defense in this ongoing battle. By the end, you will be prepared to answer important questions about this domain, ready to protect not just your data but that of the wider community.
Let us get started!
Introduction to Malware
Malware stands for Malicious Software. As the name implies, it’s a type of software intentionally designed to perform unauthorized actions and exploit, or otherwise inconvenience any computer, server, client, or network. It encompasses a range of threats including viruses, worms, trojans, ransomware, spyware, and other malicious programs. Malware can steal, delete, or encrypt data, monitor user activities, or enlist devices in botnets without the user’s knowledge. It is typically distributed via malicious email attachments, compromised websites, or infected software downloads.
Now, let’s hop into a time machine and trace the footsteps of malware’s evolution. The first known computer virus that spread in the wild, infecting PCs, was called “Brain” and was detected in the 1980s. It was relatively harmless and primarily sought to replicate itself on floppy disks. It means if an attacker wants to infect a computer in another country, he has to travel and physically carry the infected floppy disk and manage somehow to insert it into the target computer. This might sound antiquated today, but back then, it was groundbreaking (and not in a good way). When an infected disk was inserted into a computer, the virus would transfer itself to the system’s boot sector which is the section of a storage device (like a hard drive or floppy disk) containing instructions executed during the computer’s startup process. It’s essential for system initialization and loading the operating system. When Brain transferred itself to a system’s boot sector, it would become the first code executed upon startup. The virus would then replicate and install itself, often marking the storage space as “bad” to avoid detection. While it operated, Brain displayed an altered disk label, signaling its presence on the infected system. This is the behavior of early computer malware. As users shared or transferred data using these contaminated floppy disks, Brain propagated from one computer to another, demonstrating early malware’s ability to spread through physical means.

As computers and internet technologies evolved rapidly, so did the sophistication of malware. By the 1990s, the rise of the internet provided fertile ground for malware to spread. Worms like “ILOVEYOU” and “Code Red” not only demonstrated the vulnerabilities in global systems but also introduced the world to the significant potential havoc malware could wreak.
As the tendrils of internet technology began to interconnect and bind the world together, it didn’t take long for the darker elements of society to recognize the potential of this new frontier. Traditional crimes, once confined to physical spaces and tangible interactions, found a new space in which to thrive, the digital landscape. The allure was undeniable. Cybercrimes became a potent tool for those with malicious intent, offering effectiveness paired with a degree of separation from the crime scene. No longer did one need to be physically present to commit a crime; a keyboard and a connection sufficed. What made this transition even more enticing was the affordability of online malfeasance. For minimal investment, significant harm could be inflicted. Perhaps most chillingly, the digital domain offered a cloak of anonymity, making cybercrimes not only effective but also often deniable, reshaping the very nature of criminal activity in our interconnected age.



From 2000 to today, the malware landscape has dramatically evolved. In the early 2000s, we saw basic viruses and worms causing mischief or crashing computers. Soon after, cybercriminals eyed money-making opportunities, leading to the rise of ransomware, which locks files unless a ransom is paid. Spyware and trojans also emerged, secretly stealing personal information. As technology advanced, so did malware, with attacks targeting smartphones and even smart devices in our homes. State-backed cyberattacks became more common, with nations using malware for espionage and sabotage. Today’s threats are sophisticated and varied, emphasizing the importance of strong cybersecurity for everyone.
Today, the reach of malware extends far beyond individual computers. Its ramifications have swelled to societal dimensions. Businesses, irrespective of size, face crippling outages due to ransomware attacks. Factories, pivotal for manufacturing and production, can grind to a halt, disrupting supply chains. Financial institutions and government entities, the backbones of societies, aren’t exempt either. They can face severe breaches, undermining public trust and causing economic repercussions. Malware today doesn’t just compromise devices; it challenges the very fabric of societies, underscoring the important role of cybersecurity measures in all sectors.
Motives for Writing Malware
Why bad people are bad? why do they persist to be bad? what motivates them to write malware and commit cybercrime?
Before diving deep into the technicality of malware, it’s crucial to comprehend the human element behind it. After all, machines don’t act on their own; people drive them. So, a pressing question arises; Why do some individuals choose the path of crafting malicious software and committing cybercrime?
People turn to “bad” behaviors for various reasons, often shaped by a mix of personal experiences, environment, and sometimes, personal gain. Some may have faced tough circumstances, like poverty or neglect, pushing them to find shortcuts or wrong paths to success. For others, it’s the thrill of breaking rules, a desire for power, or simply the challenge of outsmarting others. Additionally, societal pressures and the quest for acceptance can influence behavior, leading some to adopt negative habits or attitudes. A few might be seeking revenge or validation due to past hurts or perceived injustices. The human psyche is complex, and motivations can intertwine, making it difficult to pinpoint a single reason. Peer influence, longing for recognition, or an upbringing where negative actions were normalized can further contribute to these choices.
Many malware attacks originate outside of first-world countries. In developed nations, numerous job opportunities and the potential for wealth often deter experts from illegal activities. They can use their skills in legitimate ways to achieve success. However, in parts of the world where opportunities are limited, talented individuals might find themselves cornered. The lack of legitimate avenues to capitalize on their expertise might push them towards cybercrime as a means to secure financial gains. This disparity in opportunities highlights the broader issue of global inequality and the extent people might go to in their pursuit of a better life.
As you can see, there isn’t a singular, straightforward answer. Just as human motivations are diverse in other areas of life, the reasons behind creating malware are manifold and complex. Let us explore the most common motives for hackers:
- Financial Gain
The most notable motive behind many cybercrimes is financial profit. Cyberspace offers numerous avenues to pilfer money. From stealing banking details to launching ransomware attacks that lock out users from their data until a ransom is paid, the online world provides lucrative opportunities for those willing to breach ethical and legal boundaries.
- Power and Control
For some, the allure of malware isn’t just money; it’s the sense of power and control. Controlling large networks of computers or bringing down major websites provides a sense of dominance in the digital domain. It can be an overwhelming feeling, especially for those who might feel powerless in other aspects of their lives.
- Espionage and Information Gathering
In the world of geopolitics and business competition, information is power. State-sponsored actors and corporate entities might employ hackers to create malware to steal secrets, be it defense strategies or a company’s intellectual property.
- Ideological Reasons
Not all cybercriminals are in it for money or power. Some are driven by their beliefs. Whether political, religious, or philosophical, these individuals or groups use malware as a means to spread their message, protest against perceived injustices, or target groups they oppose.
- Challenge and Recognition
For a subset of malware creators, the motivation can be as simple as the thrill of the challenge. Bypassing security systems, crafting a new type of malware, or outsmarting experts offers them a sense of achievement. Moreover, within certain underground communities, there’s a level of prestige associated with successful cyberattacks.
- Retaliation or Personal Vendettas
Personal grudges or the desire for revenge can also be catalysts. Someone slighted in the real world might resort to cyber tactics to get back at an individual or an organization.
- Exploration and Curiosity
A handful of individuals dig deep into the world of malware out of sheer curiosity. They want to understand systems, explore vulnerabilities, and see what’s possible, even if it means breaking the rules.
Types of Malware
Virus
In malware, one term often stands out as emblematic of the entire field; the computer virus. Its moniker, inspired by biological viruses, is apt, considering its ability to replicate and spread. But what exactly is a computer virus, and how has it shaped our digital landscape?
In malware terms, “replicate” means the ability to make copies of itself. So, when malware replicates, it creates duplicate versions of its own code, allowing it to spread and infect more systems or files.
Computer viruses bring us to the early days of personal computing. In the late 1980s and 1990s, as computers became more accessible, so did the platforms for these digital pests. Floppy disks, the primary means of software distribution, became a popular medium for virus transmission. “Brain”, as we discussed earlier, was one of the first to make headlines.
A computer virus is a type of malicious software that, once executed (typically when a user unknowingly opens it), replicates itself to other computer programs or files, thereby inserting its own code inside them. Just as a flu virus can’t reproduce outside of a host body, a computer virus requires a host file or document to spread. Upon execution, it becomes active and can proliferate, potentially corrupting or altering data in the process.
In Enterprise Local Area Network (LAN), a virus can spread by exploiting shared folders or drives. If an infected file is accessed or executed from another computer on the same network, that machine becomes infected.
One factor that differentiates viruses from other types of malware is their replication mechanism. Unlike standalone malicious software that might simply execute a harmful task, viruses embed themselves into legitimate programs or files and then spread when these files are shared or opened. Their sneaky, parasitic nature is their defining trait.
When an infected PDF file with a Virus is downloaded to the computer, the Virus within it remains dormant until you open the PDF. Upon opening, the Virus activates, executing its malicious code. Depending on its design, it may replicate by attaching itself to other files on the computer,
The impacts of viruses vary widely. Some are relatively benign, generating odd system behaviors or producing unexpected messages. Others, however, are much more malevolent, corrupting data, crashing systems, or even wiping entire hard drives. The metamorphic and polymorphic viruses, which can alter their code to evade detection, represent the evolution of these threats, showcasing the perpetual cat-and-mouse game between hackers and security experts.
You might be wondering why viruses are designed to not spread automatically unless a user executes it?
Viruses, by design, require user action to spread, like opening a file. This method offers stealth, as relying on human behavior can bypass some detection systems. Automatic spreading can raise red flags quickly. By leveraging curiosity or inattention, viruses can spread effectively without immediately revealing their presence, ensuring longer lifetimes.
Worm
Unlike its close counterpart, the virus, which requires human action to propagate, the worm operates on a more aggressive principle. A computer worm is a standalone malicious software that operates independently and doesn’t need to attach to a file or program to function. Unlike viruses, which embed themselves within documents or software, worms are self-contained entities. Modern Worms possess all the instructions and mechanisms within their own code to replicate, spread, and even execute their malicious intent without needing to latch onto other software.
Worms, given their nature, can cause extensive damage. They can consume bandwidth, causing network slowdowns or even failures. Beyond this, some are programmed to deliver a malicious payload, be it data theft, system corruption, or the creation of backdoors for future exploitation.
To shed light on Worms, let us take an example. Imagine a large organization, with thousands of computers interconnected. One day, an employee accidentally clicks on a link while browsing the web. This link initiates the download of a seemingly harmless application. However, once executed, it’s quickly evident that this isn’t a regular application, it’s a worm. The worm, having been designed to exploit a vulnerability in the Windows Server Message Block (SMB) protocol, immediately starts its silent rampage. Leveraging the SMB protocol, which is typically used for file sharing, the worm scans the network for other computers, particularly those with the same unpatched vulnerability. For every susceptible machine it identifies, the worm copies itself over. Being standalone, it doesn’t need to attach itself to other files; it simply operates from a hidden directory on the host computer. Once on a new machine, it continues its propagation process. Within hours, it has spread through a significant portion of the network. Beyond mere replication, the worm has other intentions. It begins exfiltrating sensitive data, and transmitting it to an external server. Simultaneously, the infected machines are co-opted to launch distributed denial-of-service (DDoS) attacks against other networks.
This is a typical example of worm infections, which by their nature, are crafted to be more autonomous than viruses, which often means they carry a more complex set of instructions. Indeed, some advanced worms may integrate functionalities similar to tools like Network and Vulnerability Discovery to scan networks and identify vulnerabilities. Such capabilities may also require integrating specific libraries or routines into the worm’s code, potentially making them larger in size compared to a typical virus. This self-sufficiency and the need to house all required functionalities within its code contribute to a Worm’s standalone nature. While viruses rely on host files to spread and execute, Worms are built as all-in-one packages, which can sometimes result in them having a heftier digital footprint.
Some Worms are easy to detect because they’re less sophisticated or are based on older, well-known templates, making them identifiable by security signatures. However, modern Worms present unique challenges in detection due to several inherent attributes and design choices made by their creators. Firstly, these Worms employ advanced evasion techniques, altering their code or behavior to sidestep traditional signature-based detection systems. They might use encryption or obfuscation to disguise their code, making it harder for security tools to recognize known malicious patterns. Secondly, Worms can be rapid in their spread, often exploiting known vulnerabilities before organizations have had a chance to patch or protect against them. The speed and scale of their propagation can sometimes overwhelm defenses. Additionally, worms often employ stealthy behaviors, such as operating in a system’s memory without writing to the disk or employing “low and slow” approaches to avoid generating noticeable network traffic.
When we talk about Worms and Viruses, it is important to note that the level of damage both of them can inflict is determined by their design and intent. This means a Virus can cause more havoc than a Worm and vice versa. Their destructiveness isn’t inherent to their classification but rather to the malicious intent behind their creation.
Similarities between Worms and Viruses:
- Both are types of malicious software.
- Can self-replicate and spread.
- Aim to compromise systems or data.
- Can exploit software vulnerabilities.
- Can evade certain security measures.
- Often require user interaction for activation.
- Both can exfiltrate or corrupt data.
Differences between Worms and Viruses:
- Worms are standalone, viruses need host files.
- Worms spread autonomously (faster), viruses rely on user action.
- Viruses embed their codes within existing files, worms don’t.
- Worms typically consume more network resources.
- Viruses can be dormant; worms are often aggressive.
- Worms often exploit network vulnerabilities.
- Viruses attach to and hide in host files.
- Viruses can be more persistent by embedding.
- Worms often have a larger digital footprint.
Attackers strategically choose their malware type based on the target environment. For networks that are isolated or heavily siloed, where data movement primarily happens through file sharing via emails, chat services, or removable media, viruses become the weapon of choice. Their reliance on user actions to propagate makes them effective in such settings. On the other hand, for networks with open and unrestricted connectivity, worms are particularly potent. Such environments often have network shares enabled and might use vulnerable protocols like SMB. Worms can exploit these vulnerabilities, autonomously propagate, and spread rapidly across the network without requiring user interaction. This distinction highlights the importance of understanding the nature of threats in different network configurations.
Trojan Horse
The tale of the Trojan Horse is as ancient as it is instructive. Rooted in Greek mythology, the Greeks used a giant wooden horse, ostensibly a peace offering, to stealthily infiltrate the fortified city of Troy. Little did the Trojans know that Greek soldiers hid within, ready to emerge under the cloak of darkness and lay siege to the unsuspecting city.

Similarly, in the realm of cyber threats, a Trojan Horse, often simply termed a “Trojan,” disguises itself as legitimate software, only to reveal its malicious intentions once inside the target system. At a glance, you might see a seemingly harmless software application, game, or even a document. But lurking beneath its benign exterior is a hidden agenda designed to harm, steal, or control.
Over the years, the sophistication and versatility of Trojans have evolved remarkably. Initially, they were straightforward malicious programs hiding behind innocent facades. Modern Trojans, however, often come equipped with a suite of tools that allow attackers to siphon off data, launch attacks, or even convert the infected machine into a zombie in a botnet.
The way Trojan malware works is intriguing. Unlike viruses or worms, Trojans do not self-replicate. Instead, they rely on the allure of their camouflage to trick users into downloading and installing them. This could be in the form of a cracked software version, a deceptive email attachment, or even a seemingly useful app. Once activated, they can deliver their payload, which might range from creating backdoor access to logging keystrokes or hijacking system resources.
Remember: Malware classification is about its behavior and propagation method, not the severity of its payload. Always be vigilant, as any malware type can carry destructive intent.
What sets Trojans apart from other malware types is their deceptive nature. They don’t exploit software vulnerabilities like worms or attach themselves to files like viruses. Their modus operandi is purely based on deception. They convince the user of their authenticity and harmlessness, capitalizing on human trust and sometimes, ignorance. Trojans play a psychological game and rely heavily on social engineering to achieve their objectives. By doing so, they persuade users to download, install, or execute them, often under the guise of something beneficial. The success of a Trojan often hinges on the user’s trust and curiosity. Hence, the art of deception is an integral part of the Trojan’s strategy, capitalizing on human behavior and decision-making. This is why it’s important to emphasize the importance of skepticism and caution when downloading or clicking on unfamiliar files or links.

The impact of a Trojan can be broad and diverse. For individual users, it might mean the loss of sensitive data, compromised online accounts, or even identity theft. For businesses, the implications are even more profound. Corporate espionage, massive data breaches, or operational disruptions can occur. Moreover, many Advanced Persistent Threats (APTs) leverage Trojans to gain an initial foothold in target networks, emphasizing their significant role in complex cyber-attack campaigns.
- Command-shell Trojans: Provide attackers with a command-line interface to control the victim’s system, allowing direct and often broad access.
- GUI Trojans: Offers a graphical interface to the attacker, simplifying remote system control.
- HTTP/HTTPS Trojans: Use web protocols to communicate, often bypassing firewalls by mimicking regular web traffic.
- Document Trojans: Embedded in documents. When the document is opened, the malicious code is executed.
- Defacement Trojans: Target websites, altering their appearance or content without permission.
- Botnet Trojans: Convert infected devices into ‘bots’. These bots can then be controlled collectively as a ‘botnet’ for various tasks, like DDoS attacks.
- VNC Trojans: Utilize Virtual Network Computing protocols to give attackers remote access to a victim’s desktop.
- Remote-access Trojans (RATs): Provide attackers with comprehensive remote control over a victim’s system.
- Data-hiding Trojans: Conceal data (could be the payload, C2, or operational data, etc), often by embedding it within other files (known as steganography technique), making detection challenging.
- Banking Trojans: Specifically target online banking users, aiming to steal credentials and funds.
- DoS Trojans: Designed to conduct Denial-of-Service attacks, overwhelming systems or networks with traffic.
- FTP Trojans: Use the FTP protocol to allow attackers to transfer files to and from the victim’s system.
- Software-disabling Trojans: Target and disable security software (like antimalware or firewall), paving the way for further attacks without detection.
- Covert-channel Trojans: Communicate or transfer information using non-standard channels or protocols to avoid detection.
Important Note: Malware classification (like ‘Trojan’ or ‘Worm’) refers to distinct characteristics or origin methods. However, a single malware can exhibit behaviors of multiple classifications. For instance, a malware could enter a system disguised as legitimate software (Trojan trait) and then autonomously spread to other systems (Worm trait). Thus, while classifications help us understand primary features, real-world malware might blur these lines by combining multiple behaviors.
Ransomware
Ransomware is a form of malicious software designed to encrypt a victim’s data, rendering it inaccessible. The attackers then demand a ransom, usually in cryptocurrency, for the decryption key. The primary intent isn’t data theft (as with many other malwares) but extortion.

The concept of ransomware isn’t exactly new. It roots trace back to the late 1980s with the “AIDS Trojan”. Victims received a floppy disk that claimed to determine one’s risk of AIDS based on a questionnaire. Post evaluation, the malware would hide directories and encrypt the names of files, followed by a ransom note demanding payment for a solution. Victims were instructed to pay the ransom by sending a cashier’s check or money order to a P.O. Box address in Panama. This means hackers’ addresses can be tracked because they are physically exposed addresses. This is the reason why they did not rely very much on ransomware as malware generates money for them until crypto currency reached out. Today, the advent of cryptocurrencies like Bitcoin provided hackers with an anonymous and decentralized payment method, reducing their risk of being traced. This anonymity catalyzed the surge in ransomware attacks, as cybercriminals found a safer means to monetize their exploits without revealing their identities or physical locations.
From these rudimentary beginnings, ransomware has evolved dramatically. The 2010s witnessed a significant upswing in its activity. With the ascent of Bitcoin and other cryptocurrencies, attackers found a secure and anonymous method to demand ransoms. The mid-2010s saw the emergence of Ransomware-as-a-Service (RaaS), where even non-tech-savvy criminals could launch attacks using platforms provided by developers in exchange for a share of the profit.
CryptoLocker in 2013 was a watershed moment. This ransomware used strong encryption standards, ensuring that without the decryption key, victims had little chance of recovering their files. It opened the door to numerous successors, with “WannaCry” in 2017 amplifying global awareness due to its widespread impact.
Here are some of the most globally impactful and well-known ransomware variants from recent years:
- WannaCry (2017) – One of the widest ransomware attacks. Used NSA exploits to spread quickly through networks. Crippled systems like UK’s NHS.
- NotPetya (2017) – Posed as ransomware but was designed as data wiper. Caused over $10 billion in damages globally.
- Cryptolocker (2013) – One of the first to use crypto ransom payments. Infected hundreds of thousands of computers.
- Locky (2016) – Prolific ransomware frequently updated to improve extortion capabilities. Spread via phishing emails.
- Cerber (2016) – Prevalent ransomware-as-a-service allowing customized campaigns. Targeted 150 countries.
- Ryuk (2018) – Targeted enterprises and critical infrastructure. Disrupted major organizations like newspapers and hospitals.
- Maze (2019) – Double extortion tactics by threatening to leak data. Compromised numerous companies.
- REvil (2019) – A ransomware gang disrupted meat production with attack on JBS foods. Demanded $11 million.
- Conti (2020) – Ransomware used in the attack against Ireland’s health service. Caused major care disruptions.
In most of the known ransomware attacks over the last decade, attackers have employed asymmetric encryption. Asymmetric encryption, also known as public-key cryptography, involves two keys; a public key, which is used for encryption, and a private key, used for decryption. The strength of asymmetric encryption lies in the fact that, even if an attacker makes the encryption key public, the decryption key remains private, ensuring that only the attacker can decrypt the data. When a ransomware infects a system, the malicious software usually generates a unique pair of public and private keys. Files are encrypted with the public key, rendering them inaccessible to the victim. The attackers then demand a ransom in exchange for the private key, which is the only means to decrypt and regain access to the locked files. This method is more secure and efficient in the opinion of the attackers than symmetric encryption, where the same key is used for both encryption and decryption, as any potential exposure or mishandling of a single key in symmetric encryption would compromise the entire process.
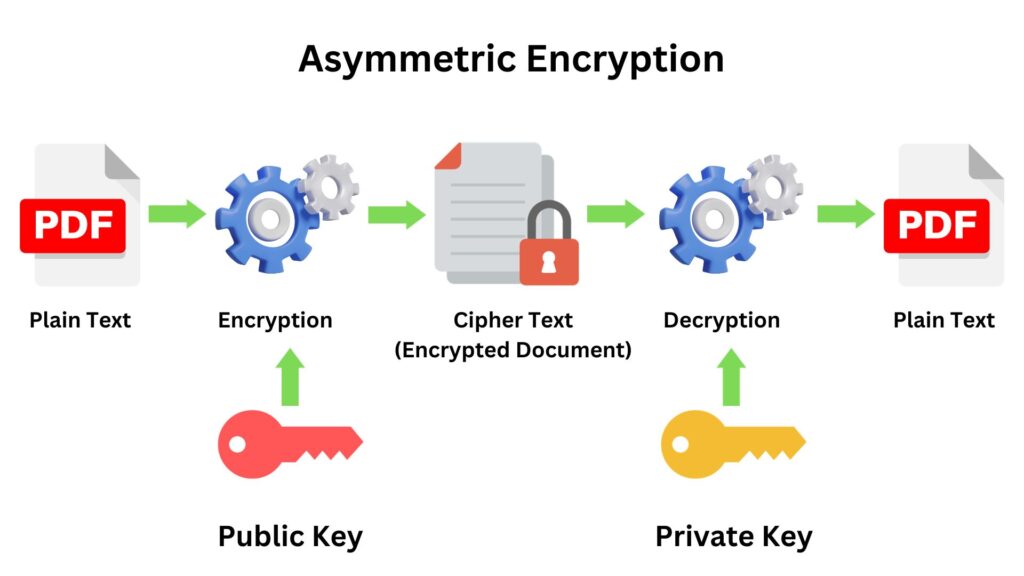
Here’s a glimpse into how a typical ransomware attack unfolds:
Infiltration
Often, ransomware infects systems through phishing emails or by exploiting software vulnerabilities. A user might receive an email masquerading as an important document, but once opened, the malicious payload is delivered.
Encryption
Upon execution, the ransomware scans the system for files, and then employs strong encryption algorithms to lock them. Modern ransomware often connects to a remote server to generate encryption keys for each infected system, ensuring that the necessary decryption key remains with the attacker. This means even if you get one decryption key, you will only be able to unlock files on that specific computer. This is a typical practice conducted by hackers.
Ransom Note
Post encryption, a ransom note is displayed, instructing victims on payment. It often threatens data deletion or price escalation if the ransom isn’t promptly paid.
Decryption
If the victim pays, they receive a decryption key. However, payment doesn’t guarantee data recovery, and often funds further illicit activities.
From an ethical standpoint, paying a ransom to hackers isn’t advised. When you pay, you’re directly funding their criminal activities. This not only empowers them but also encourages them to develop even more potent ransomware and target more innocent people and businesses. By refusing to pay, you’re taking a stand against this form of cybercrime. Moreover, there’s no guarantee that after paying, your files will be safely returned. The more people resist paying, the less lucrative and appealing this malicious activity becomes for cybercriminals.
What makes ransomware distinct from other malware types is its direct focus on immediate financial gain for the attacker. Instead of silently stealing information or compromising system integrity, ransomware loudly announces its presence by locking out users from their data. It’s a digital hostage situation where the victim’s files or entire system are encrypted, and a ransom is demanded for their release. This aggressive tactic combines both malicious software and psychological manipulation, as victims are put under immense pressure with countdown timers and escalating ransom amounts. Ransomware’s immediate and visceral impact on its victims is what makes it particularly notorious in the realm of cyber threats.
Ransomware’s impact extends far beyond technical disruptions; it profoundly affects our daily lives and the very fabric of society. Imagine a hospital where critical medical systems are encrypted, surgeries could be delayed, patient records inaccessible, and life-saving treatments halted, risking lives. If water or electricity providers fall victim, entire cities could face blackouts or water shortages, disrupting basic necessities and potentially causing widespread panic. Financial institutions hit by ransomware might freeze transactions, rendering people unable to access their funds, pay bills, or conduct business. Such attacks not only cause immediate chaos but can erode public trust in vital institutions. Ransomware today has the potential to destabilize societal structures.
In recent ransomware attacks, cybercriminals have adopted a two-pronged extortion strategy. Before encrypting a victim’s files, they first exfiltrate the data. Even if an organization can restore its systems from backups, attackers then threaten to leak or sell the stolen information on the dark web. This dual-threat approach increases the pressure on victims to pay the ransom. It addresses the improved resilience that some organizations have built against encryption-only attacks. By threatening to expose sensitive data, hackers exploit concerns over reputational damage, legal consequences, and loss of competitive advantage, adding a potent layer to their extortion tactics.
Rootkits
The term “rootkit” combines “root,” the highest level of system privilege, with “kit,” implying a set of tools or utilities. It is designed to gain unauthorized access to a computer system and hide any traces of their presence. Unlike typical viruses or worms, rootkits embed themselves deeply within a system’s software, often at the kernel level, manipulating its functions to remain undetected. Their primary goal is not damage, but covert control, enabling them to conceal other malicious activities, such as data theft or system monitoring. The deceptive nature of rootkits makes them challenging to detect and remove, often requiring specialized tools that operate outside the potentially compromised operating system. They represent one of the most covert and dangerous cyber threats.
Historically, the concept of rootkits can be traced back to the early days of computing. Initially, these were benign tools for Unix systems, helping administrators with system maintenance. However, it didn’t take long for malicious actors to recognize their potential. As the technological landscape evolved from Unix to Windows and beyond, so did rootkits, adapting to the changing environments and becoming more sophisticated.
Rootkits, by design, are not casual malware. They are typically deployed in targeted attacks, where attackers have a specific interest in the victim, such as corporate or state espionage. Unlike many other malware types that seek to cause visible disruption or demand ransoms, rootkits are all about stealth and persistence, allowing attackers to covertly gather intelligence or monitor the infected systems over long periods.
Rootkits can infiltrate systems via phishing emails, malicious downloads, or exploiting software vulnerabilities. Once on the system, they work to elevate their privileges and embed deeply within the OS. In some cases, they can be introduced via physical access, like when an attacker has brief access to a system or through infected USB devices. They employ techniques like password cracking to gain elevated privileges. Once they achieve this higher-level access, they can modify system settings, disable security software, and embed themselves more deeply to maintain control.
Due to their deep-level system integration, often at the kernel level, and their ability to manipulate system functions, rootkits can effectively hide their tracks. They can intercept and modify the system calls that tools use to list processes or files, rendering themselves invisible. This manipulation makes traditional detection mechanisms, like antiviruses, often ineffective. Technically, what sets rootkits apart is their stealth and persistence. Once installed, they can intercept and manipulate the OS’s operations. This can include hiding specific processes, files, system logs, or even other malware. By tampering with system calls and outputs, they can make malicious processes appear benign, or even invisible. For instance, while a regular malware might be visible in a system’s process list, a rootkit can mask its presence, ensuring it doesn’t show up in such lists at all. Furthermore, many rootkits possess self-defense mechanisms, neutralizing tools or processes that may threaten their discovery or removal.
Below are the common destructive actions and behaviors exhibited by rootkits:
- Intercept Operating System API calls.
- Conceal processes and files.
- Hide system network connections and activites.
- Mask unauthorized user accounts.
- Modify system configurations and settings.
- Disable security software.
- Exfiltrate sensitive data.
- Provide remote access to attackers.
- Log user keystrokes.
- Manipulate system logs to hide activity.
- Bypass authentication mechanisms.
- Install secondary malware payloads.
- Redirect web traffic.
- Modify or tamper with system binaries.
- Hijack application functions.
Below are the recommended defense strategies to countermeasure Rootkits:
- Application whitelisting: Only allow known good programs and block anything not explicitly whitelisted. Prevents unknown rootkit processes.
- Memory protections: Use protections like Data Execution Prevention (DEP) and Address Space Layout Randomization (ASLR) to make memory exploits harder that allow rootkit injection.
- Secure boot: Validate boot process integrity with UEFI secure boot to prevent bootloader rootkits.
- Firmware protections: Use signed firmware, firmware write protections, and other controls to block firmware rootkits.
- Anomaly detection: Monitor for irregular system behavior that could indicate rootkit presence.
- Isolation and minimalism: Run minimal processes/services to limit attack surface area for rootkits.
- Forensic analysis: Use advanced forensic examination of systems, sweeping with latest threat intelligence to thoroughly inspect for rootkit evidence.
- Behavioral-Based Detection: Instead of relying solely on signature-based methods, some tools focus on detecting anomalous behavior. For instance, unexpected system calls or unauthorized access attempts can signal the presence of a rootkit.
- Integrity Checking: Regularly checking the integrity of system files and the registry can identify unauthorized modifications, a hallmark of rootkit activity.
- Boot-Time Scans: Some antimalware tools offer boot-time scans, which examine the system before the full OS loads. This can catch rootkits that activate upon system start.
- Hardware-Assisted Security: Features like Intel’s Trusted Execution Technology (TXT) or AMD’s Hardware Validated Boot can prevent unauthorized code from running at boot-time.
- Rootkit-specific Tools: There are tools specifically designed to detect rootkits, such as GMER or TDSSKiller. Regular scans with these can be beneficial.
- Regular Updates: Keeping the OS and all software updated ensures that known vulnerabilities, which might be exploited by rootkits, are patched.
- System Hardening: Disabling unnecessary services and ensuring strong authentication mechanisms can reduce potential attack vectors.
- Network Monitoring: Observing outgoing and incoming network traffic can identify suspicious patterns indicative of rootkit communications.
- Regular Backups: Maintain up-to-date backups. In cases where a rootkit infection is suspected, restoring to a clean state might be the most reliable solution.
- Principle of Least Privilege: Limiting user permissions can deter rootkits from gaining the elevated privileges they need. Users should operate under standard permissions, with administrative rights granted only when necessary.
- User Education: Informing users about the dangers of downloading from untrusted sources or clicking on suspicious links can prevent many infection vectors.
Once a rootkit is detected, fully removing it without missing any component is extremely challenging because of its deep system integration. Any remnants can potentially allow the rootkit to reestablish itself. Thus, to ensure complete removal and system integrity, it’s commonly recommended to format or wipe the infected computer, then reinstall the operating system and applications from trusted sources.
Below are the known types of Rootkit malware:
| Rootkit Type | Description |
|---|---|
| Kernel Mode Rootkits | These operate at the same level as the operating system and can directly manipulate kernel structures. Their deep integration makes them difficult to detect, and they can intercept and modify system operations seamlessly. |
| User Mode Rootkits | Operate in the user space of an OS. They might replace legitimate files with malicious ones or inject malicious code into running processes. Easier to detect than kernel mode rootkits but can still be potent. |
| Application Rootkit | Target specific applications, modifying their behavior. For instance, they might alter how a software interacts with the OS, change data being processed, or intercept user inputs, all without detection. |
| Bootloader Rootkit or Bootkit | Load even before the OS starts, by replacing or modifying the legitimate bootloader. This gives them early control, allowing them to hide their presence and often bypass security software that loads later. |
| Memory Rootkit | Reside in a system's RAM and don't leave traces on the hard drive. They can manipulate system operations in real-time but might be lost after a system reboot, unless paired with another mechanism to reinfect. |
| Hardware or Firmware Rootkit | Embedded within a device's firmware or hardware components like BIOS, UEFI, or even peripheral devices. They can be especially stealthy since they exist outside the main storage and can potentially reinfect systems even after a full OS reinstall. |

Backdoor
Backdoors initially were made for legitimate uses and they refer to a method, often secret, that the developers use to bypass normal authentication or encryption in a computer system, a product, or an embedded device. Backdoors are often used for securing unauthorized remote access to a computer or obtaining access to plaintext in cryptographic systems. There are many benefits of Backdoors when they are used for legitimate reasons, some are:
- Troubleshooting and Support
Developers might create backdoors to provide technical support. If a user encounters a problem that they can’t resolve, the developer can use the backdoor to access the system and diagnose the issue. - Updates and Maintenance
Backdoors can be used to remotely update software, fix bugs, or make necessary modifications, especially in cases where regular access might be cumbersome or infeasible. - Recovery
In situations where users forget their passwords or lock themselves out, a backdoor can provide a way to regain access. - Regulatory or Legal Access
In some contexts, products may have built-in backdoors to allow legal or governmental access under specific conditions. For instance, telecommunications equipment might have a backdoor to permit lawful intercepts. - Emergency access
Having a way to access systems during outages can enable incident response and system recovery. - Licensing control
Software vendors can use backdoors to disable products if licenses expire or payments fail.
While the concept of a backdoor implies a method intentionally designed into a system, in the context of malware, it usually refers to a malicious piece of software that exploits weaknesses or vulnerabilities to create secret and unauthorized access points (covert remote access).
Backdoor commonly refers to a specific outcome of a malware infection. Think of it this way: a house may have a front door where guests are expected to knock and seek permission to enter. But if someone has secretly installed a backdoor, he can enter without knocking or even being noticed.
It’s a secret channel, often called a “covert channel”, opened after a piece of malware has successfully infected a target system. This covert channel typically operates over the network, bypassing standard authentication mechanisms and enabling the attacker to gain access and secretly spy on, control, or extract data from the compromised system.
This covert channel can manifest in various ways; it might be a hidden process, an obscurely named service, or a rarely used protocol communicating at odd hours. Because it’s crafted to be stealthy, this channel is frequently encrypted or disguised to blend in with legitimate traffic, making it challenging to detect for the untrained eye.
However, with advancements in intrusion detection systems and network monitoring tools, spotting these covert channels has become feasible, but still requires meticulous scrutiny. For instance, anomalies in data packets, unexplained network activities during off-hours, or unexpected communication to unfamiliar IP addresses can be telltale signs.
While discussing backdoors, it’s essential to touch on the relationship with Trojans. Some literature categorizes backdoors as a subtype of Trojan. This classification makes sense when you consider that a Trojan’s modus operandi is to masquerade as legitimate software and then perform malicious activities once inside the host. If the malicious activity a Trojan performs is to open a covert channel for an attacker, then it’s effectively behaving like a backdoor.
For clarity, let’s consider a practical example; Imagine a Linux-based web server running an older version of the Apache web server. An attacker discovers this and uses a known vulnerability in that Apache version to inject malicious code. Once the code is executed, it establishes a covert channel, allowing the attacker uninterrupted access to the server. This channel could be a simple reverse shell using SSH on a non-standard port, encrypted to look like normal traffic. From this point on, the attacker can upload, download files, execute commands, or even deploy additional malware. In essence, through exploiting a vulnerability, a backdoor has been installed, granting the attacker unimpeded access.
A “Reverse Shell” is a technique where a compromised computer initiates an outbound connection to an attacker’s machine, rather than the attacker connecting directly to the victim. Once established, the connection allows the attacker to send commands to the victim’s system. This method often bypasses firewall rules and network restrictions, facilitating covert remote control.
In advanced cyber-attacks, a backdoor often serves as an initial foothold, enabling attackers deeper infiltration. Once inside, they might deploy a variety of malware types depending on their objectives. For instance, ransomware could be introduced to extort money, while rootkits can further conceal their activities and maintain persistence. This multi-stage approach not only maximizes potential damage but also ensures attackers can adapt to varying circumstances within the target network.
Fileless Malware
Fileless malware, as the name suggests, is a type of malicious software that operates without the need for traditional executable files to be stored on the disk. Instead, it exploits legitimate tools and services, typically residing in volatile storage like RAM, which makes it markedly different and more elusive than file-based malware. Let’s dive more into its nature, techniques, and implications.
Traditionally, malware relied on hard disk files to infect a system, making them easier to detect using signature-based security tools. Over time, as defensive mechanisms evolved, attackers sought more sophisticated means to evade detection. This led to the rise of Fileless malware, which leverages tools already present in the system, minimizing its footprint and staying predominantly in memory.
The mechanism of Fileless malware operates by hijacking legitimate processes and tools commonly found in modern operating systems. For instance, it might use PowerShell, a task automation framework, or Windows Management Instrumentation (WMI), both native to Windows systems. By commandeering these tools, the malware can execute malicious activities while appearing as a normal process. Instead of dropping a traditional payload, Fileless malware usually commences its attack in RAM, often through a spear-phishing link or a malicious ad that runs a script to exploit an existing vulnerability. Once inside, it uses legitimate system tools to further its malicious intent, such as spreading across networks, gathering data, encrypting data, or launching other attacks.
A classic instance of Fileless malware in action was the “Kovter” attack. Initially starting as a police ransomware, it evolved into a click-fraud botnet. Kovter used a combination of PowerShell scripts and macros embedded in documents. When a user opened the malicious document, the macros would execute, fetching a PowerShell script from a remote server. This script then proceeded with its malicious activities, all while remaining fileless, leveraging the system’s own tools, and evading many detection mechanisms.
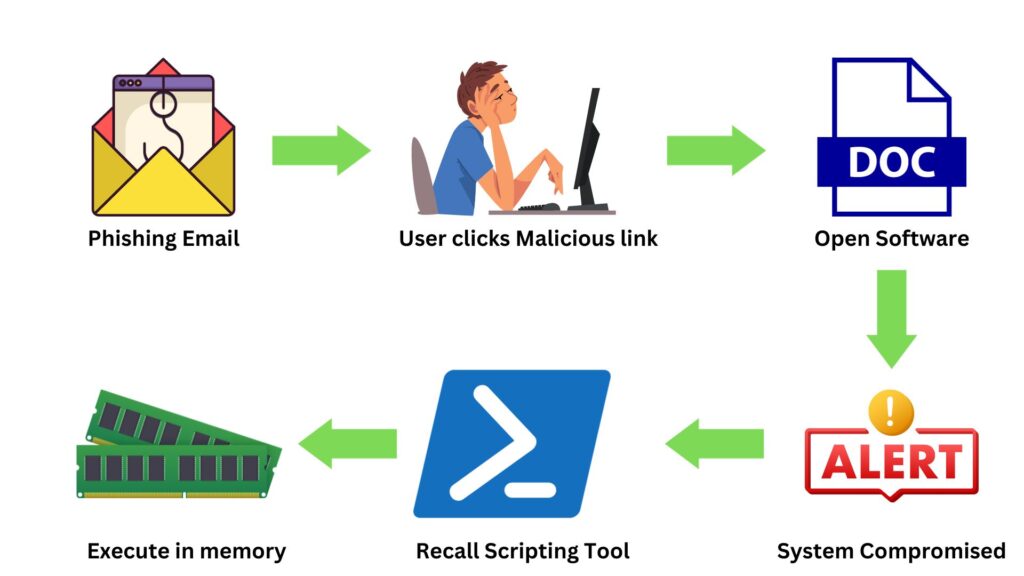
What sets Fileless malware apart from its file-based counterparts are its stealthy traits. Given its reliance on system tools and memory-based operations, it often evades traditional anti-virus solutions, which predominantly monitor file activities. Its ephemeral nature means that, unless captured in action, it leaves little to no trace on the hard disk after system reboot.
Spyware
Spyware is a type of malware designed specifically to spy on users. It covertly monitors and collects information about a person or organization without their knowledge. This data can range from browsing habits and keystrokes to personal details like passwords, credit card numbers, and other sensitive information. The primary motivation behind deploying spyware is usually financial gain, but it can also be used for targeted attacks, corporate espionage, or even by nation-states for intelligence gathering.
Unlike some other forms of malware which make their presence known (like ransomware that alerts the user of its existence), spyware tries to remain hidden, silently working in the background. It often sneaks onto computers by piggybacking on other software installations or via malicious websites. Once installed, it embeds itself deep into the system, sometimes using rootkit techniques to avoid detection.
There are several types of spyware, each with its unique characteristics:
- Keyloggers: These record every keystroke a user makes, capturing passwords, messages, and other sensitive data.
- Adware: While its primary function is to serve ads, many adware programs track users’ browsing habits to deliver targeted advertisements.
- Trojan spyware: Disguises itself as legitimate software but, once installed, delivers a spyware payload.
- System monitors: These record everything that happens on a computer, from emails sent/received to programs used, and even capture screen content.
- Tracking cookies: These are less malicious but track browsing habits, often without the user’s consent.
The implications of a spyware infection are vast. For individuals, it can lead to identity theft, financial loss, and a breach of privacy. Organizations face not only these threats but also potential intellectual property theft, loss of competitive advantage, and regulatory penalties if customer data is compromised.
Adware
Adware, an abbreviation of “advertising” and “software,” is a type of software that displays unwanted advertisements on a user’s computer. Typically, these ads pop up as banners, full-screen apps, or within the boundaries of the software environment itself. While some adware is relatively harmless and merely serves as a revenue model for free applications, the line between benign adware and malicious intent can blur. Many adware programs not only display advertisements but also collect user data without explicit permission, veering into the territory of spyware.
It is often bundled with free software. Many freeware or shareware applications disclose in their terms and conditions that, in exchange for the free service, ads will be shown. However, not all are transparent about this, leading to unexpected ad inundation. Some adware can change browser settings, alter homepage preferences, or redirect search results to promotional pages. More aggressive forms might resist uninstallation attempts, mimicking behavior seen in more overtly harmful malware types. Another common adware distribution method is through drive-by downloads. In these cases, a user might visit a seemingly benign website, but the site exploits vulnerabilities to install adware without the user’s knowledge. Additionally, fake alerts or misleading graphics (clickbait) can deceive users into downloading adware, thinking they’re accessing legitimate content.
Frequent pop-ups, banner ads, or unexpected browser behavior can disrupt a user’s experience. However, the underlying risks go beyond these disturbances. By tracking browsing habits, adware can invade user privacy. Some adware, especially those that blur lines with spyware, may collect personal information, leading to identity theft or fraud.
Bot and Botnet
Imagine your computer is like a puppet, and a puppeteer, miles away, is pulling its strings, making it do things without you knowing. In cybersecurity, if your computer becomes such a “puppet,” it’s often called a “bot.”
A bot is a computer that has been compromised, meaning a hacker has taken control of it, typically without the owner’s knowledge. This can happen when a person unknowingly downloads malicious software, or malware, which allows the hacker to take control.
Now, imagine not just one puppet, but thousands or even millions of them, all controlled by a single puppeteer or a group of puppeteers. This massive army of compromised computers is called a “botnet.” Think of it like a big team where each computer (bot) works together under the command of their controllers (hackers).
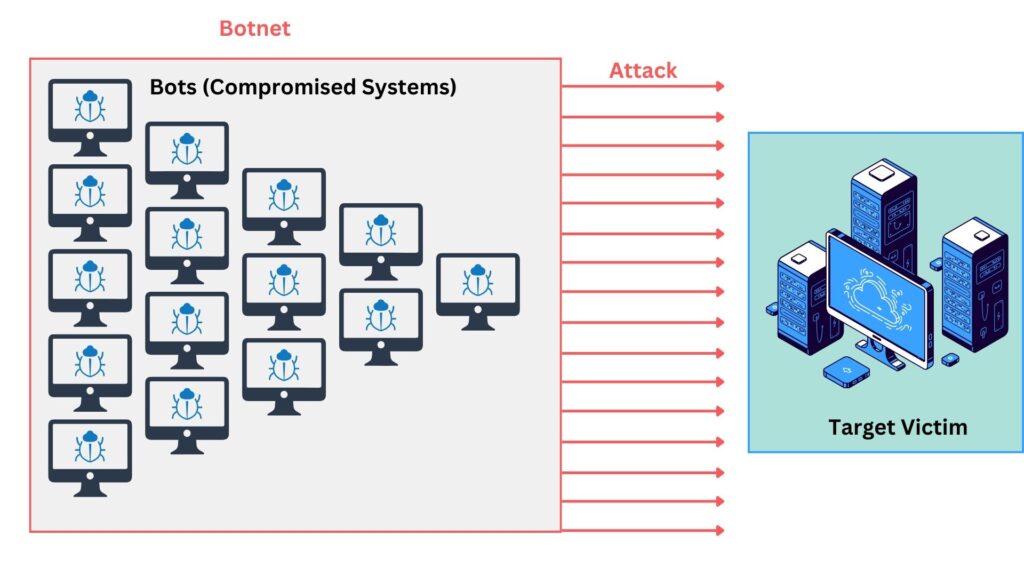
Why Are Botnets Dangerous?
- Massive Scale Attacks
Because a botnet can control many computers, it can do tasks on a huge scale. For example, it can flood a website with so much traffic that the website crashes. This is known as a Distributed Denial of Service (DDoS) attack. It’s like thousands of people trying to enter a shop at the same time, causing the shop to become overcrowded and chaotic. - Spreading Malware
Botnets can be used to send out more malware to other computers. It’s like one puppet recruiting more puppets to join the army. - Stealing Information
These bots can steal personal information from the compromised computer, like passwords or bank details. - Sending Spam
Botnets can send out massive amounts of unwanted emails, called spam. This can be used to scam people or spread more malware. - Cryptocurrency Mining
Some botnets take over computers to mine digital currencies like Bitcoin. This process uses your computer’s resources to solve complex mathematical problems, which earns the hacker cryptocurrency. It can slow down your system and increase your electricity bill without you knowing why. It’s like someone secretly using your electricity to make money for themselves. - Click fraud
Bots can be used to simulate fake clicks on online ads hosted on websites to artificially inflate revenues. This is a form of online advertising fraud.
Hackers have crafty ways to ensnare unsuspecting machines. Often, they disguise malicious software within seemingly harmless downloads. A user might think they’re getting a helpful tool or a fun game, but in reality, they’re letting in malware that converts their computer into a bot. Additionally, hackers deploy deceptive emails, known as phishing attacks, which mimic trustworthy organizations, luring individuals to click on harmful links. And sometimes, they just take advantage of the computer’s software vulnerabilities, exploiting these weaknesses to sneak their malware onto the system.
Logic Bomb
To better understand it, let’s imagine a time bomb. A time bomb sits silently until a specific moment arrives, then BOOM! It explodes. There is something similar in IT, which is a sneaky piece of software similar to a time bomb, called a “Logic Bomb.” But instead of exploding with fire and noise, it creates digital chaos on the computer system.

A Logic Bomb is a piece of malicious software, or malware, that waits silently on your computer. It doesn’t cause immediate harm. Instead, it waits for a specific event to happen or a certain condition to be met. Once that event or condition occurs, the Logic Bomb “explodes” by activating its harmful actions. This might be deleting files, corrupting data, or any other damaging task.
Let us take an example to illustrate it further. Consider a software developer at a big company. He has been told his contract won’t be renewed. Feeling bitter, he inserts a Logic Bomb into the company’s payroll system. The malicious code is set to activate on two conditions; firstly, it waits until his name is no longer on the monthly payroll, indicating he’s left the company. secondly, it checks the date to ensure it’s the last day of the financial year. When both these conditions are met, the Logic Bomb triggers. It then scrambles the salary data of every employee, causing confusion and financial chaos right when annual reports are due.
A Logic Bomb can act as the triggering mechanism for ransomware. Instead of immediately encrypting files or locking users out once the ransomware is installed, the malicious software can lie dormant, waiting for specific conditions to be met. Once these conditions occur – be it a certain date, a particular user action, or another triggering event – the Logic Bomb activates the ransomware. The ransomware then encrypts the user’s files or locks them out of their system, followed by a ransom demand for the decryption key or to regain access. In such scenarios, the Logic Bomb is essentially the “timer” or “trigger” for the ransomware’s malicious action.
The realm of malicious software is broad and complex, leading to a myriad of terms and classifications. Let’s understand the distinction between prime malware classifications and the behaviors or techniques some malicious software employs.
We already talked about the major categories of malware, which are distinguished primarily by their operational mechanics and ultimate objectives.
- Virus: Attaches itself to legitimate software and spreads upon execution.
- Worm: Replicates itself to spread across networks.
- Trojan: Disguises itself as legitimate software but delivers a malicious payload.
- Rootkit: Seeks deep system access to hide its presence.
- Ransomware: Encrypts user data and demands payment for decryption.
- Spyware: Covertly collects user data.
- Adware: Delivers unsolicited ads.
- Bot/Botnet: Compromises systems to be remotely controlled by an attacker.
- Backdoor: Provides covert remote access to a compromised system.
These prime types are based on distinct malicious objectives or modi operandi. For instance, ransomware’s main goal is to extort money, while a worm’s primary purpose is propagation.
On the other hand, you might hear a lot of terms like “Dropper,” “Polymorphic Malware,” and “Packers”, etc describe techniques, behaviors, or secondary functionalities rather than primary objectives.
- Dropper: A piece of software that “drops” or installs a malicious payload onto a system. For example, a Trojan might have a dropper mechanism to install a keylogger or backdoor after initial execution.
- Polymorphic Malware: Refers to malware that changes its code or appearance to evade detection. A virus, worm, or any prime type could be polymorphic.
- Packers: Tools that compress or obfuscate a malware’s code, making it harder to detect or analyze. Any malware type can be “packed.”
These terms don’t define the “end-goal” of the malware but rather describe its characteristics or the techniques it uses to be successful. It’s similar to distinguishing between a type of vehicle (e.g., a truck) and the features or mechanisms it might employ (e.g., turbocharged engine).
Why the Distinction Matters?
Understanding the difference between a malware’s primary classification and its behavior or technique is crucial. While primary classifications help us understand the malware’s primary intent, on the other hand, behaviors and techniques indicate how it achieves that intent. Both are important for cybersecurity professionals. It’s entirely plausible for a single piece of malware to fit a primary category and exhibit multiple behaviors. For example, a Trojan (primary classification) might be polymorphic (behavior) and contain a dropper (technique) that installs a backdoor (another primary classification).
Here’s a simplified table we made for representational purposes that categorizes malware into their primary classification, associated behaviors, and techniques. It’s worth noting that the lines between these categories can sometimes blur, and this is a generalized representation. Some malware can exhibit multiple behaviors and techniques.
| Malware Classification | Possible Behavior | Possible Technique | Intent Achievement |
|---|---|---|---|
| Virus | Polymorphic | Dropper | A virus mutates its code to evade detection and uses a dropper to embed itself within legitimate files, spreading its infection upon execution. |
| Worm | Self-replicating | Network Propagation | Worms autonomously reproduce and spread across networks, consuming resources and potentially delivering malicious payloads. |
| Trojan | Disguised | Payload Delivery | Trojans masquerade as legitimate software but deliver hidden malicious activities once executed. |
| Rootkit | Stealthy/Hiding | Kernel Manipulation | Rootkits embed deep within OS operations to hide and provide attackers with persistent, privileged access. |
| Ransomware | Data Encryption | Public Key Encryption | Ransomware encrypts victim data using a public key, rendering it inaccessible. The private key, held by the attacker, is needed to decrypt, driving victims to pay the ransom. |
| Spyware | Data Harvesting | Background Monitoring | Spyware silently collects and transmits user data, often for financial or identity theft purposes. |
| Adware | Pop-up Generation | Browser Ad Injection | Adware continuously shows unwanted ads, often redirecting users to sponsored sites, generating revenue for attackers. |
| Bot/Botnet | Remote Control | Command & Control Communication | Infected devices (bots) are remotely controlled as part of a larger network (botnet) to conduct widespread malicious activities, like DDoS attacks. |
| Backdoor | Covert Access | Reverse Shell | Backdoors provide attackers with hidden access to systems, often leveraging reverse shells for remote command execution. |
| Fileless Malware | Memory-resident Execution | Utilizing Legitimate Tools & Processes | Fileless malware operates directly from memory or piggybacks on legitimate processes, evading traditional file-based detection methods. It might leverage tools like PowerShell to run commands that fetch payloads or scripts from remote servers, executing them entirely in memory without ever writing to the disk. |
Case Study
Acme Corp is a large holding company, it presents an attractive target for sophisticated threat actors. In this case study, let us see how a determined Threat Actor group, armed with resources and intent, leveraged the Cyber Kill Chain model to orchestrate a multi-staged attack on Acme Corp. This model, outlining the stages of a typical cyber-attack, provides a structured approach for attackers and offers valuable insights for defenders. Let’s explore how Acme Corp became ensnared in this malicious web.
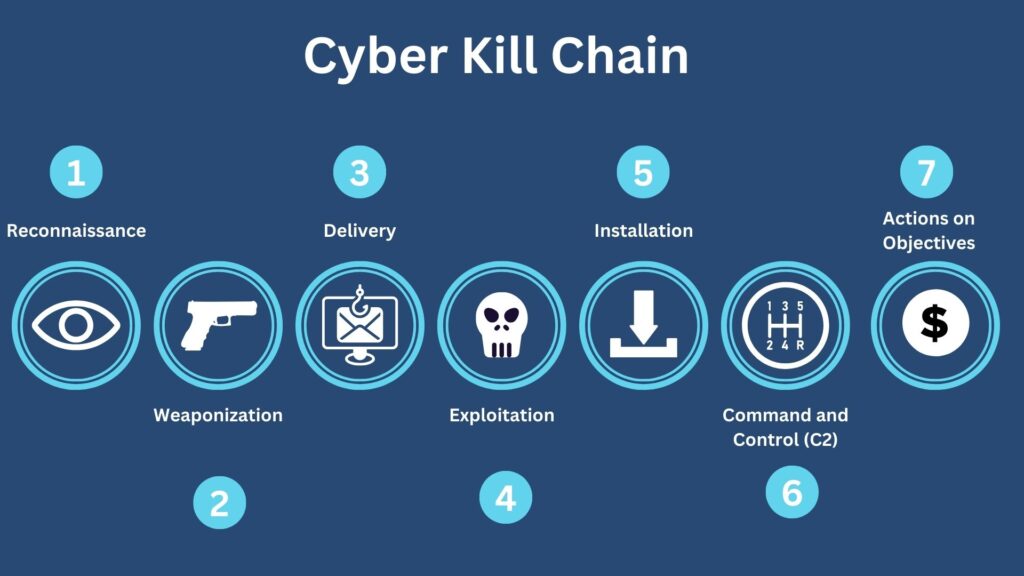
1. Reconnaissance
Before the actual attack began, the Threat Actor group invested time in understanding Acme Corp’s digital landscape. They scoured the internet for information about the company’s IT infrastructure, employees, their roles, and public-facing systems. The group found that Acme Corp had recently expanded, incorporating multiple smaller entities, potentially leading to disparate security practices.
2. Weaponization
With a clearer picture of Acme Corp’s vulnerabilities, the Threat Actor group designed a malware that was stealthy, polymorphic, and utilized zero-day vulnerabilities. Being fileless functioning in RAM memory, it ensured that no traditional traces were left behind. This malware, once activated, would have multiple stages, meaning it wouldn’t unleash its full arsenal at once.
3. Delivery
The group identified that Acme Corp’s CEO was highly influential and would often send company-wide emails. They decided to employ a BEC (Business Email Compromise) tactic. Crafting a seemingly legitimate email from the CEO, they targeted a specific employee known to be less tech-savvy.
4. Exploitation
When the unsuspecting employee opened the malicious attachment in the email, the first stage of the malware was activated. Using a zero-day vulnerability within the system, it gained an initial foothold without raising any alarms.
5. Installation
Once inside, the malware began its multi-stage deployment. The first stage established a covert communication channel back to the attacker’s command and control server (C2) using a GUI that resembled legitimate software, ensuring its disguise. With this channel, subsequent stages of the malware were downloaded piecemeal, further ensuring stealth.
6. Command and Control (C2)
With a firm grip inside Acme Corp’s systems, the malware continuously communicated with the attacker’s C2. It relayed crucial data and awaited further instructions. Through this, the threat actors were able to control the malware’s actions in real-time, adapting to any unexpected barriers.
7. Actions on Objectives
The real devastation began when the malware started its dual mission. First, it identified and transmitted sensitive Acme Corp data back to the threat actors. Once this data exfiltration was complete, the ransomware component of the malware activated. Files across the network were encrypted, leaving Acme Corp’s operations paralyzed. A ransom note popped up on the screens, demanding a hefty payment to decrypt the files. The note also threatened that if Acme Corp did not comply, their sensitive data would be auctioned in the dark web.
Acme Corp, caught off guard, had to decide between paying the ransom or facing immense financial and reputational damage. This incident was a solemn reminder of the importance of continuous cybersecurity education and the danger of highly-invested, multi-faceted threats in the digital age.
The Important Role of Anti-Malware
Anti-malware consistently reigns as a frontline defense. While a variety of cybersecurity tools offer specific functions, from firewalls to intrusion detection systems, anti-malware remains essential due to its direct combat against malicious software, a predominant threat in the digital life.
Anti-malware software detects malware using a combination of methods. It relies on signature-based detection, which checks files against a database of known malware signatures. Heuristic analysis observes file behaviors and characteristics to detect new or modified malware. Behavioral analysis monitors a program’s activities in real-time, flagging any malicious actions. Some solutions also use sandboxing, running suspicious files in a safe, isolated environment to observe their behavior. Additionally, machine learning and cloud-based analysis can be employed, leveraging vast datasets and patterns to recognize malicious intent. By combining these methods, anti-malware tools offer a layered defense against both known and emerging threats.
Malware creators are tireless, continually evolving their tactics and creating new threats. Every day, thousands of new malware samples emerge. Anti-malware tools require frequent updates to their signature databases to arm themselves against these fresh threats. Without these updates, a system becomes vulnerable to the newest strains of malware.
Anti-malware solutions typically consist of a centralized management console and agents that reside on individual machines. These agents are critical for several reasons:
- Real-time Monitoring
Agents scan in real-time, constantly checking files accessed by the user or system against their threat database. This immediate surveillance ensures that threats are detected and handled promptly. - Localized Decisions
Agents can make on-the-spot decisions, like quarantining a suspicious file, without needing to communicate with a central server. This ensures rapid response times. - Broad Protection
Every machine presents a potential entry point for malware. If one device in a network is left unprotected, it can be compromised and used as a launchpad to attack other networked devices. Agents on each machine ensure that all potential entry points are guarded.
Here is a table of the common actions typically taken by Anti-Malware security agents:
| Action | Description | Suitable For |
|---|---|---|
| Quarantine | Isolates the suspicious file or program from the rest of the system, preventing its execution or access. It's like putting the file in a "jail". | When unsure if the file is truly malicious or if there's a possibility of false positives. Useful to preserve potential evidence or to analyze later. |
| Delete/Remove | Permanently deletes the malicious file or program from the system, ensuring it can no longer execute or spread. | When confident that the file is malicious and there's no need for further analysis or recovery. |
| Clean | Removes the malicious part of a file, attempting to render the file harmless while preserving its original content or function. | When the file is essential, and only a specific part of it is compromised, such as an infected Word document. |
| Block | Prevents the suspicious or malicious file or program from being executed or accessed. This action can be temporary or permanent. | Useful for potentially unwanted programs (PUPs) or when a known malicious activity is detected but the user might need access later. |
| Ignore/Allow | Lets the file or program continue its operation without any intervention, considering it safe. | For false positives or trusted applications flagged inadvertently. Useful when the security software is overly cautious. |
| Alert/Notify | Informs the user or administrator about the suspicious or malicious activity without taking direct action against the file or program. It leaves the decision to the user or admin. | For potential threats or when the anti-malware tool needs guidance on the next action, giving the user/admin control over the decision process. |
| Recovery and Rollback | Restores the system or files to a pre-infection state. | Severe infections, to revert changes made by malware. |
As we discuss Anti-Malware, it’s important to understand its distinct functions. Each technique plays a crucial role in safeguarding systems from diverse threats. The following are common techniques available is most of the modern Anti-Malware solutions used to defeat and countermeasure malware:
- Signature-based detection: Identifies known malware based on specific signatures or patterns.
- Reputation checks: Compares files and web domains against databases to determine if they’re known to be good or malicious.
- Heuristic analysis: Assesses code behavior and structure to detect unfamiliar malware.
- Behavior monitoring: Observes how software operates in real-time, flagging abnormal actions.
- Machine learning: Uses AI to predict and detect novel malware forms based on learned patterns.
- Sandboxing: Tests suspicious files in isolated, virtual spaces to avoid real-world harm.
- Endpoint Detection and Response (EDR): Monitors devices for ongoing threats, often with response mechanisms.
- Intrusion Prevention: Examines network activity for abnormal patterns, especially using deep packet inspection.
- Application control: Permits only trusted software to operate.
- Whitelisting: Only pre-approved files can run.
- Blacklisting: Known malicious files are prevented from running.
- Memory analysis: Examines system memory for signs of malware presence.
- Patch updater: Regularly updates third-party software to close security holes.
- Threat intelligence: Continually collects and analyzes data on emerging threats.
- Removable media control: Manages and scrutinizes external storage devices.
- Isolation/segmentation: Keeps systems separated to prevent cross-contamination.
- Forensics and attribution: Deep dives into threats to understand origin and impact.
- Firewall Filtering: Restricts inbound and outbound, potentially harmful communications, and enables visibility.
- Exploit Prevention: Blocks attempts to misuse software flaws.
- Document exploit detection: Identifies malicious scripts within documents.
- File Integrity Monitoring: Alerts on unsanctioned modifications to crucial files.
- Data Leak Prevention (DLP): Stops the unauthorized transfer of sensitive data.
Frequently Asked Questions (FAQs)
Do attackers use a specific programming language to create malware, or can it be developed in common languages like Python, Java, etc.?
Attackers can use virtually any programming language to develop malware, depending on the intended target and functionality. Common languages like Python, Java, C++, and even scripting languages like JavaScript can be used. However, languages like C and Assembly are often chosen for low-level tasks and to exploit certain vulnerabilities. The choice often depends on the platform being targeted and the desired capabilities of the malware.
What exactly is a malware “payload”?
A malware payload is the actual software code that a malicious file carries. It is the malicious intent or action that the malware is designed to execute. Think about it as the “endgame” or primary function of the malware. While the delivery mechanism might be a trojan or worm, the payload is the effect those vehicles deliver, be it data theft, system corruption, or another malicious goal.
For example, a PDF resume arrives via email. When opened, an embedded malicious JavaScript (the payload) activates, stealthily harvesting passwords and leveraging the compromised machine to target other systems.
What is Zero-Day Malware and Why is it Significant?
A Zero-Day malware exploits a software vulnerability that is unknown to the software vendor or hasn’t been publicly disclosed. The term “zero-day” denotes that there’s zero time between the discovery of the vulnerability and the first attack exploiting it, leaving software vendors with no time to develop and release a security fix. This makes such malware particularly dangerous. The name emphasizes the urgency and the surprise factor, as defenders are unprepared for the new threat. Security professionals should be deeply concerned about zero-day threats because traditional defenses, like signature-based detection, might not recognize them. They represent a blind spot in security measures, and due to their unknown nature, can cause significant damage before they are detected and mitigated.
What is Malware Analysis?
Malware analysis is the process of examining and dissecting malicious software to understand its functionality, intent, and impact. This investigation helps in developing countermeasures to detect and mitigate the malware’s effects. New malware is commonly analyzed through static (examining the code without executing it) and dynamic (observing the malware’s behavior during execution) methods. Automated tools and controlled environments, like sandboxes, are often used. The analysis is typically performed by cybersecurity researchers, threat analysts, and specialized professionals in security organizations, antivirus companies, or independent research institutions. Their insights lead to updated malware signatures and improved detection mechanisms.
Why are malware files typically small in size?
Malware files are often designed to be small for efficiency and stealth. Compact sizes facilitate quicker downloads, reduce detection chances, and allow easy embedding in other files or documents. Large files might raise suspicions or cause delays. Moreover, malware can retrieve additional components post-infection, negating the need for a large initial file size.
Why are hundreds of thousands of new malware discovered daily?
The vast number of malware emerging daily stems from several factors. First, cybercrime is lucrative, driving attackers to constantly create and modify malware to bypass security measures. Second, malware generation tools and frameworks allow even less-skilled individuals to produce unique variants with minimal effort. Additionally, polymorphic and metamorphic techniques automatically change malware’s appearance without altering its core functionality. This makes each instance look different, evading signature-based detections. Lastly, the diverse range of cyber-attack objectives, from financial gain to espionage, ensures a continuous evolution and proliferation of malicious software.
What differentiates polymorphic from metamorphic malware?
Polymorphic malware alters its observable characteristics (like code or data structures) while preserving its original behavior using encryption and varying encryption keys. Each time it infects, it looks different to evade signature-based detection. On the other hand, metamorphic malware completely rewrites its own code with each iteration, aiming to perform the same malicious function but appearing as entirely different software. In essence, while both types evolve to avoid detection, polymorphism involves disguising using varied encryption, whereas metamorphism entails a full transformation of the malware’s code.
Summary
During our study in this lesson, we closely examined malware and its many aspects. Here’s a summary of our main points we discussed:
Our initiation began by unraveling the very essence of malware. We looked into its fundamental definition, examining the reasons for our heightened concern about its proliferation. As we retraced the evolutionary trajectory of malware, we simultaneously uncovered the transformation of cybercriminals. Their motivations, driven by a combination of financial gain, desire for control, ideological beliefs, and sheer mischief, have powered the growth and sophistication of malicious software. These insights offered us a deeper appreciation of the urgency and necessity to combat these digital threats.
Building on our foundational understanding, we ventured into the taxonomy of malware. We meticulously dissected various classifications, casting light on the distinct characteristics of each type. Our exploration was further enriched as we distinguished between malware classifications, behaviors, and techniques. This understanding empowers us to discern and strategize against different malware threats more effectively.
To transition from theory to practical application, we immersed ourselves in a detailed case study. This narrative portrayed a meticulously planned attack, where adversaries harnessed the structured approach of the Cyber Kill Chain. By analyzing a real-world scenario, we witnessed firsthand the complexities of a multi-stage malware attack, gaining invaluable insights into the modus operandi of sophisticated cyber adversaries.
Having understood the potential damage malware can wreak, our attention shifted to defense mechanisms. We underscored the critical importance of anti-malware solutions, elucidating how they operate to protect our digital realms. Through this, we recognized that staying updated and proactive is the cornerstone of effective malware defense.
In conclusion, this lesson aimed to provide a holistic view of malware, encompassing its genesis, evolution, nuances, and countermeasures. As we move more into the online world, knowing this helps us use the internet safely and with confidence.
Homework
- Explore more into the Brain malware. Recognized as one of the pioneering malicious software in the computer world, research its origin, propagation mechanism, and the impact it had during its time.
- Malware comes equipped with tons of techniques and behaviors to evade detection and achieve its malicious intent. List and provide a brief explanation of the various techniques and behaviors that modern malware utilizes.
- Construct a comprehensive table comparing key malware classifications like viruses, worms, trojans, and others. Try to list as many criteria as you can.
- Dive deeper into the concept of zero-day exploits. What makes them so fatal? How do they remain undetected? And most importantly, how can they be countered or mitigated?
- Investigate various modern anti-malware solutions available in the market. List their primary features, detection mechanisms, and their pros and cons.
- Explore how Artificial Intelligence (AI) and Machine Learning (ML) are being utilized in modern anti-malware solutions. What advantages do they offer, and what are the potential challenges?
- Utilize online platforms or software (such as Hybrid Analysis or Cuckoo Sandbox) that allow for safe malware analysis in a sandboxed environment. Analyze a sample (non-malicious) file and document your observations.
If you learned something new today, help us to share it to reach others seeking knowledge.
If you have any queries or concerns, please drop them in the comment section below. We strive to respond promptly and address your questions.
Thank You

